Source: www.databreachtoday.com – Author: 1
Endpoint Security
,
Internet of Things Security
,
Standards, Regulations & Compliance
Denial of Service Attack, Remote Code Execution Could Affect Medtronic’s Paceart Optima System
Marianne Kolbasuk McGee (HealthInfoSec) •
June 29, 2023
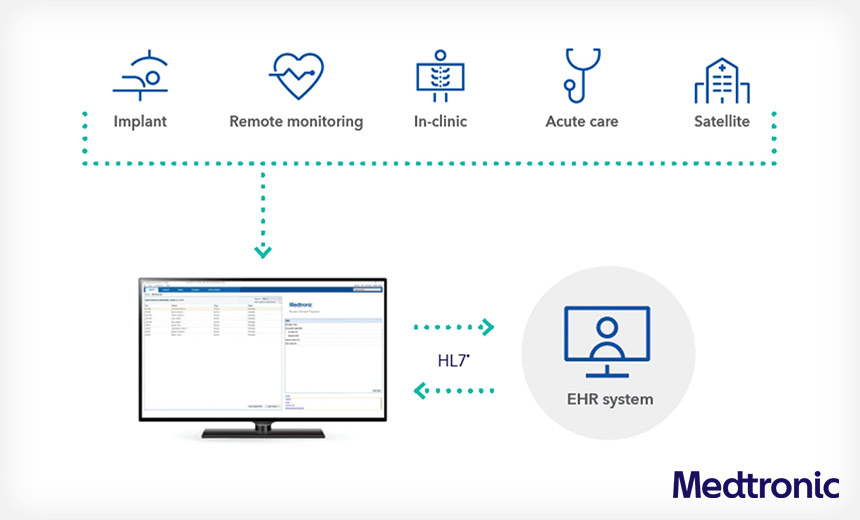
Federal regulators are warning about a vulnerability in medical device maker Medtronic’s Paceart Optima System for collecting and managing data from cardiac devices. The flaw, if exploited, could lead to a denial-of-service attack or remote code execution that could affect the system’s operations and data.
See Also: Live Webinar | The Secret Sauce to Secrets Management
CISA, in an advisory issued Thursday, said the deserialization of untrusted data vulnerability identified in Medtronic’s Paceart Optima, versions 1.11 and earlier, is exploitable remotely and has a low attack complexity.
Medtronic, which reported the flaw to CISA, also issued a bulletin explaining that the vulnerability is in an optional messaging feature of the Paceart Optima cardiac device data workflow system.
“This feature is not configured by default, and it cannot be exploited unless enabled,” Medtronic said.
CISA warned that a malicious actor could exploit the vulnerability to perform remote code execution and/or a DDoS attacks by sending specially crafted messages to the Paceart Optima system.
“Remote code execution could result in the deletion, theft or modification of Paceart Optima system’s cardiac device data, or use of the Paceart Optima system for further network penetration. A DoS attack could cause the Paceart Optima system to slow or be unresponsive,” CISA said.
CISA said the vulnerability is tracked as CVE-2023-31222, with a CVSS v3 base score of 9.8.
To address the issues, Medtronic recommends users of the Paceart Optima system update their product to v1.12.
The company also suggested immediate mitigations that users can apply including manually disabling the Paceart Messaging Service on the product’s application server and manually disabling message queuing on the application server.
“As long as the Paceart Messaging Service remains disabled, the vulnerability will remain mitigated,” Medtronic said.
Original Post url: https://www.databreachtoday.com/feds-medtronic-warn-flaw-in-cardiac-device-data-tool-a-22410
Category & Tags: –




















































