Source: hackread.com – Author: Waqas.
A Facebook malvertising campaign disguised as Bitwarden updates spreads malware, targeting business accounts. Users are tricked into installing malicious Chrome browser extensions.
Cybersecurity researchers at Bitdefender have uncovered a malicious advertising (malvertising) campaign that exploits Meta’s advertising platform to distribute malware on Facebook. This campaign, detected on November 3, 2024, disguises the malware as a security update for the popular Bitwarden password manager. Although the campaign has been taken down, experts warn that similar threats are likely to resurface.
From Malicious Facebook Ads to Fake Chrome Store
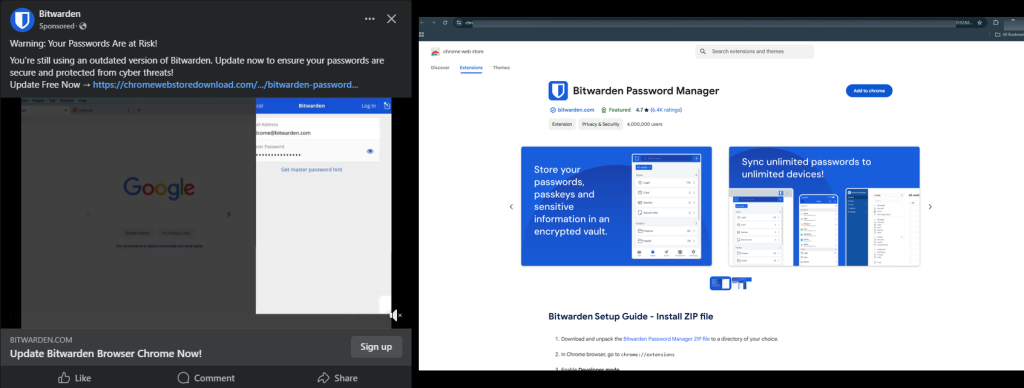
The campaign uses deceptive Facebook ads that appear to be legitimate security updates for Bitwarden. These ads warn users about the risk of compromised passwords and trick them into installing an urgent security update for the password manager. The ads are designed to look authentic, using Bitwarden’s branding and language to create a sense of urgency.
When users click on these ads, they are redirected through a series of websites before reaching a phishing page that mimics the official Chrome Web Store. This final page notifies users to install a malicious browser extension disguised as a Bitwarden update. The installation process involves downloading a zip file from Google Drive, unzipping it, and manually loading the extension into the browser.
According to Bitdefender’s blog post shared with Hackead.com heard of its publishing on Monday, once installed, the malicious Chrome extension requests permissions, enabling it to intercept and exploit the user’s online activities.
Some key permissions requested include access to all websites, modification of network requests, and access to storage and cookies. The extension’s manifest file reveals these permissions, indicating its ability to perform various malicious activities.
Researchers noted that the core of the attack lies within the background.js script, which activates upon installation. This script performs several critical tasks data exfiltration which the collected data is sent to a Google Script URL acting as a command-and-control server, cookie harvesting which allows attackers to search for Facebook cookies, particularly the c_user cookie containing the user’s Facebook ID. The script also gathers IP address and geolocation data and extracts personal and business information from Facebook using the Graph API.
Impacted Users
The malware’s primary targets are Facebook business accounts putting unsuspected individuals and organizations at risk. The malvertising campaign has already reached thousands of users, primarily in Europe, with the possibility to expand globally.
If you use Facebook for business purposes and manage a business account, it’s important to stay cautious. If you come across a malicious ad prompting you to install updates, avoid clicking on it. Instead, visit the official website of the product to verify and access legitimate security updates.
Original Post url: https://hackread.com/facebook-malvertising-malware-via-fake-bitwarden/
Category & Tags: Security,Malware,Bitwarden,Cybersecurity,Facebook,Fraud,Malvertising,Password manager – Security,Malware,Bitwarden,Cybersecurity,Facebook,Fraud,Malvertising,Password manager
Views: 0