Source: www.bleepingcomputer.com – Author: Bill Toulas

A malware botnet known as ‘Ebury’ has infected almost 400,000 Linux servers since 2009, with roughly 100,000 still compromised as of late 2023.
ESET researchers have been following the financially motivated malware operation for over a decade now, warning about significant updates in the payload’s capabilities in 2014 and again in 2017.
Below are the Ebury infections logged by ESET since 2009, showing a notable growth in the volume of infections over time.
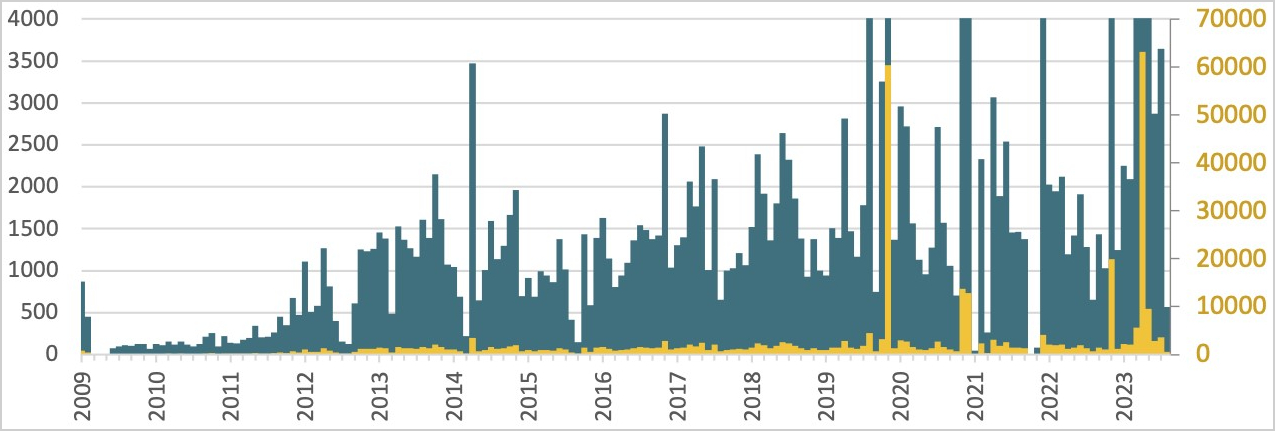
Source: ESET
In the latest update published today, ESET reports that a recent law enforcement action allowed them to gain insight into the malware operation’s activities over the past fifteen years.
“While 400,000 is a massive number, it’s important to mention that this is the number of compromises over the course of almost 15 years. Not all of those machines were compromised at the same time,” explains ESET.
“There is a constant churn of new servers being compromised while others are being cleaned up or decommissioned. The data at our disposal doesn’t indicate when the attackers lost access to the systems, so it’s difficult to know the size of the botnet at any specific point in time.”
Ebury’s latest tactics
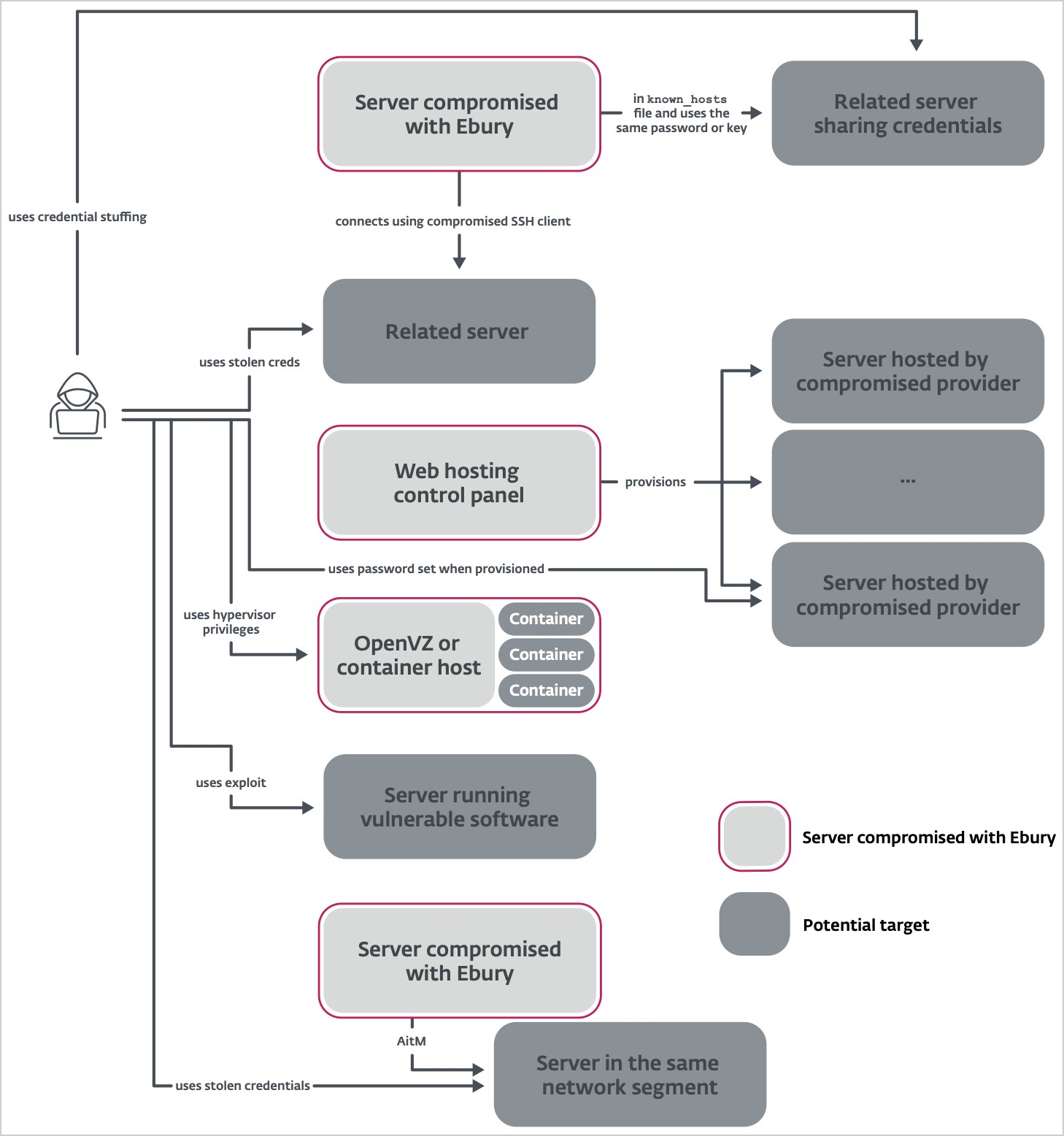
Recent Ebury attacks show a preference by the operators to breach hosting providers and perform supply chain attacks to clients renting virtual servers on the compromised provider.
The initial compromise is performed via credential stuffing attacks, using stolen credentials to log into the servers.
Once a server is compromised, the malware exfiltrates a list of inbound/outband SSH connections from wtmp and the known_hosts file and steals SSH authentication keys, which are then used to try to log into other systems.
“When the known_hosts file contains hashed information, the perpetrators try to brute force its content,” reads ESET’s detailed report.
“Out of 4.8 million known_hosts entries collected by Ebury operators, about two million had their hostname hashed. 40% (about 800,000) of those hashed hostnames were guessed or brute forced.”
Alternatively, and where possible, the attackers may also exploit known vulnerabilities in the software running on the servers to gain further access or elevate their privileges.
Source: ESET
The hosting provider’s infrastructure, including OpenVZ or container hosts, can be leveraged to deploy Ebury across multiple containers or virtual environments.
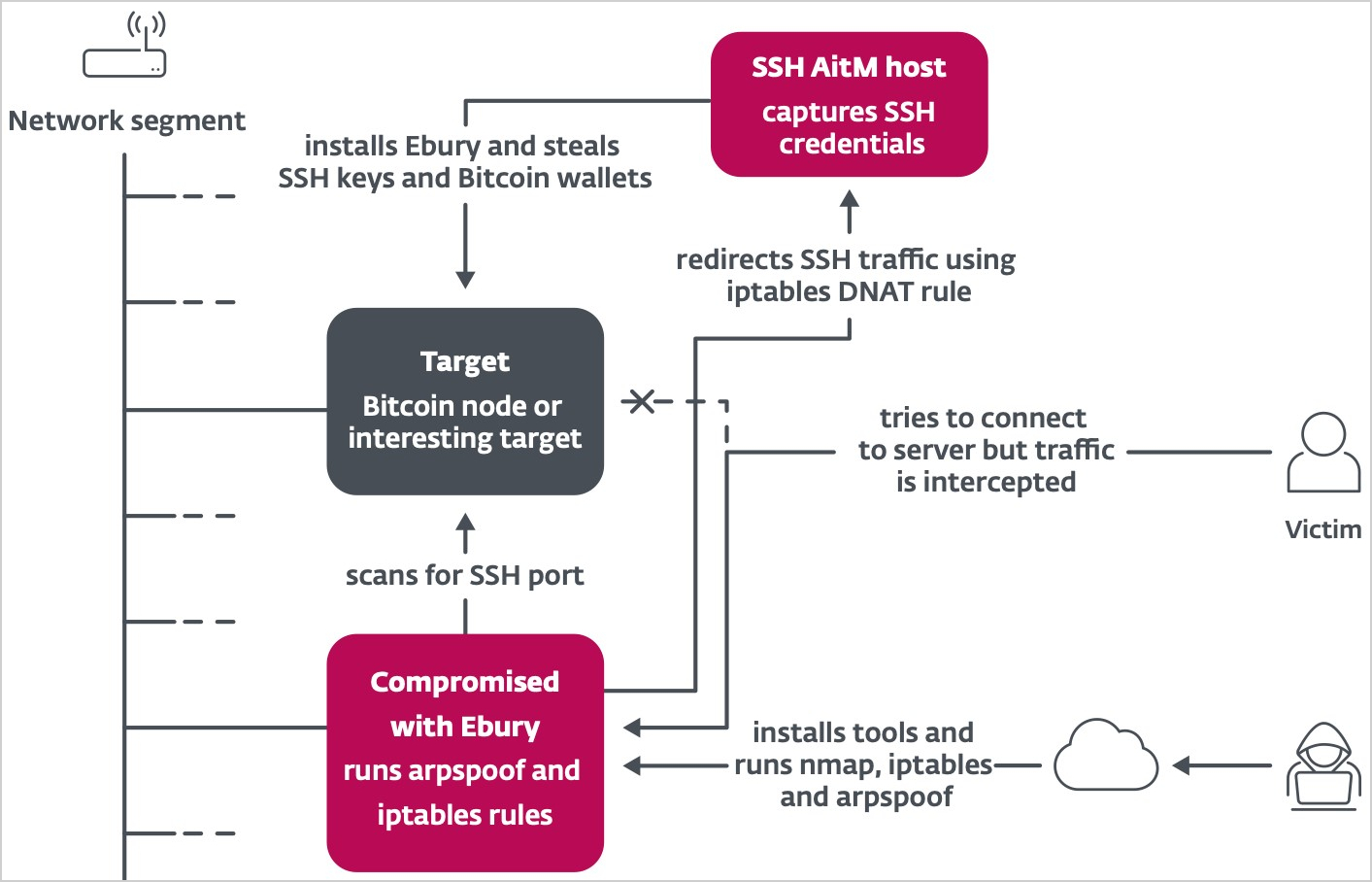
In the next phase, the malware operators intercept SSH traffic on the targeted servers within those data centers by using Address Resolution Protocol (ARP) spoofing to redirect traffic to a server under their control.
Once a user logs into a compromised server via SSH, Ebury captures the login credentials.
Source: ESET
In cases where servers host cryptocurrency wallets, Ebury uses the captured credentials to empty the wallets automatically.
ESET says Ebury targeted at least 200 servers using this method throughout 2023, including Bitcoin and Ethereum nodes.
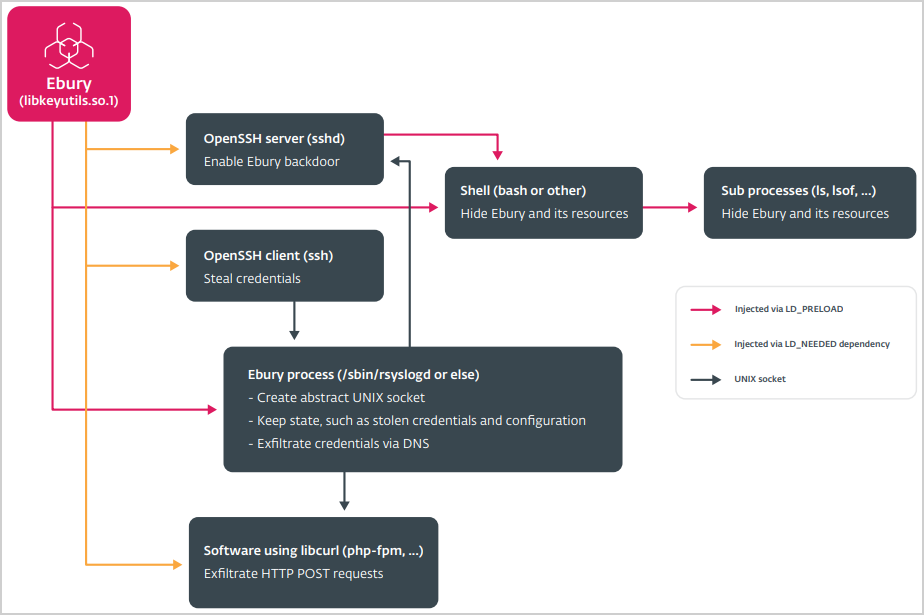
The monetization strategies vary, though, and they also include stealing credit card information entered into payment sites, redirecting web traffic to generate revenue from ads and affiliate programs, using compromised servers to send spam, and selling the captured credentials.
Source: ESET
In late 2023, ESET says it observed the introduction of new obfuscation techniques and a new domain generation algorithm (DGA) system that allows the botnet to evade detection and improve its resilience against blocks.
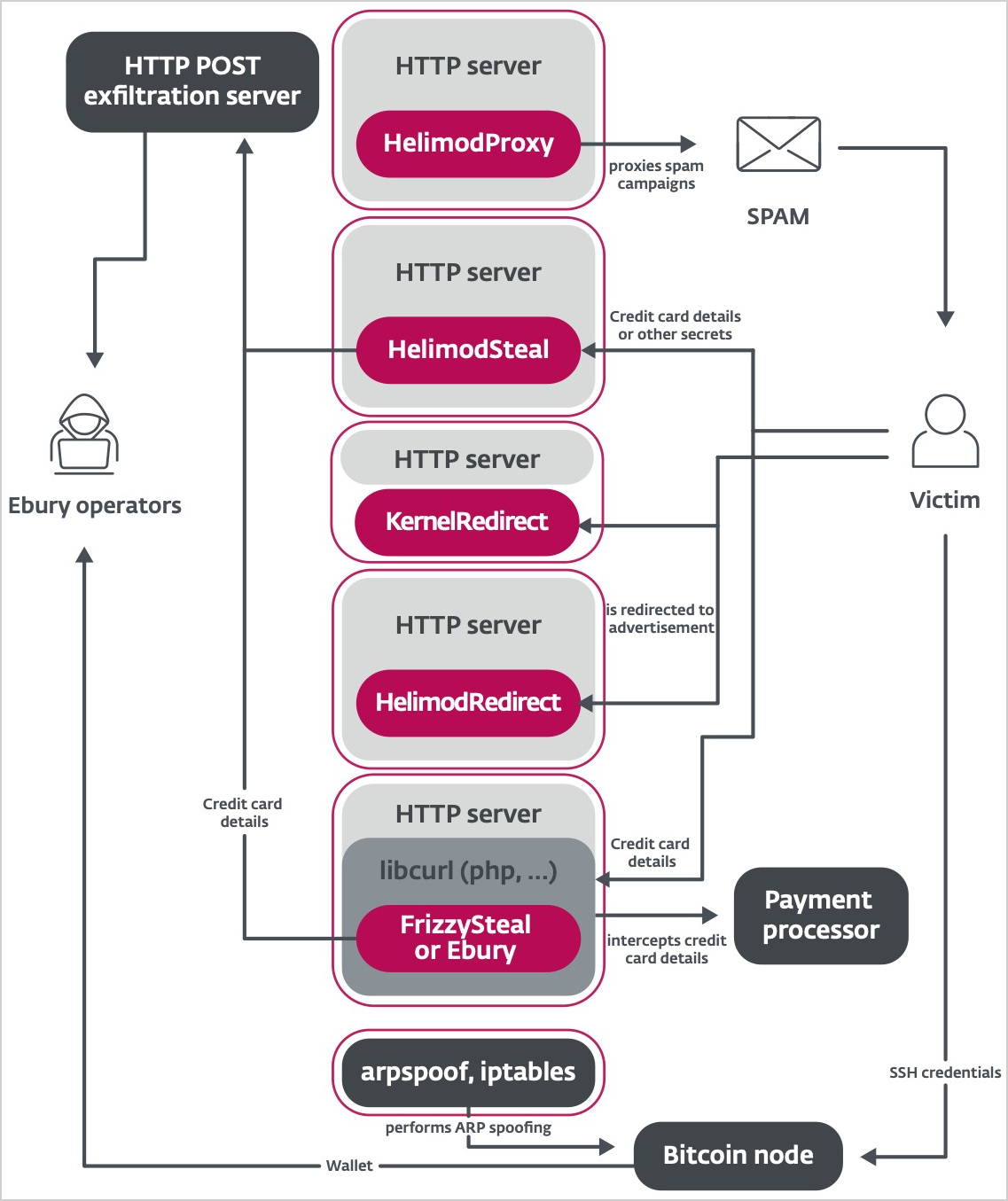
The malware modules spread via the Ebury botnet, based on ESET’s latest observations, are:
- HelimodProxy: Proxies raw traffic and relays spam by modifying the mod_dir.so Apache module, allowing the compromised server to run arbitrary commands and support spam campaigns.
- HelimodRedirect: Redirects HTTP traffic to attacker-controlled websites by modifying various Apache and nginx modules to redirect a small percentage of web traffic to malicious sites.
- HelimodSteal: Exfiltrates sensitive information from HTTP POST requests by adding an input filter that intercepts and steals data submitted via web forms, such as login credentials and payment details.
- KernelRedirect: Modifies HTTP traffic at the kernel level to redirect visitors by using a Linux kernel module that hooks into Netfilter, changing the Location header in HTTP responses to redirect users to malicious URLs.
- FrizzySteal: Intercepts and exfiltrates HTTP requests by hooking into libcurl, enabling it to capture and steal data from HTTP requests made by the compromised server.
Source: ESET
ESET’s latest investigation was carried out in collaboration with the Dutch National High Tech Crime Unit (NHTCU), which recently seized a backup server used by the cybercriminals.
The Dutch authorities say Ebury actors use fake or stolen identities (via the Vidar Stealer), even assuming the monikers of other cybercriminals sometimes to mislead law enforcement.
The NHTCU is investigating evidence found in that server, including virtual machines containing web browsing artifacts such as history and saved logins, but no concrete attributions have been made yet.
Original Post URL: https://www.bleepingcomputer.com/news/security/ebury-botnet-malware-infected-400-000-linux-servers-since-2009/
Category & Tags: Security,Linux – Security,Linux
Views: 0