Source: heimdalsecurity.com – Author: Miriam Cihodariu
DNS over HTTPS (DoH) is a relatively new protocol that became a powerful tool in providing internet privacy and security. Ever since Mozilla was first to implement it, in 2018, DoH reshaped the digital landscape and made online communication safer.
In the years that followed, big internet brands, like Apple, Microsoft, and Google also implemented DNS over HTTPS (DoH) to prevent eavesdropping and DNS data manipulation.
Of course, as with any other tool, it came with benefits and risks, when not handled properly. All in all, encrypting DNS queries enabled users to better control their online experiences and keep their communication private.
When implemented right, DoH can make network communications much more secure. This guide will tell you what this means and how you can implement DNS over HTTPS, what’s the impact on cybersecurity solutions, and what are the benefits and risks.
What Is DNS over HTTPS (DoH)?
DNS over HTTPS (DoH) is an internet security protocol that communicates domain name server information in an encrypted way over HTTPS connections.
The standard released by the IETF enables DNS protocol to be enabled over HTTPS connections (the more secure form of HTTP).

The route of a DNS query when DoH is enabled.
To better understand what DoH implies, it is also essential to know what the DNS is. For your convenience, I have included a definition and some additional clarifications in the section below.
DNS Definition
DNS stands for Domain Name System, and it helps computer networks attach various information to each web domain. To put it simply, the Domain Name System is basically the fundamental internet address book.
While people can remember a domain name easily, computers need numbers to understand it. That’s why the DNS ”translates” each domain name into an IP number and assigns this info, together with other details.
A DNS traffic filtering solution is a crucial security layer for businesses and consumers alike. We already discussed in another article the importance of DNS traffic filtering and what cybercriminals can hope to get from infiltrating it.
1. Standard DNS vs. DNS over HTTPS (DoH)
Networks using standard DNS communications are vulnerable to man-in-the-middle attacks if they are not protected by a traffic filtering solution. This is because all DNS queries are written in plain text.
The innovation brought on by the DNS over HTTPS protocol is that it encrypts queries using built-in application HTTPS standards. This helps achieve an unprecedented default level of privacy and data protection since the encryption is (or should be) the golden standard.
When DNS over HTTPS is enabled, Man-in-the-middle attacks are more or less useless. Since all DNS requests are encrypted, a 3rd party observer cannot make sense of the data they would gleam.
When DNS requests are not encrypted it is easy for a 3rd party malicious observer to see what domains you are trying to access. In contrast, when DoH is active, this data is encrypted and hidden within the enormous amount of HTTPS data that passes through the network.
Therefore, the difference between DNS over HTTPS (DoH) and DNS over HTTP is more than obvious. DoH is clearly the superior protocol, as it definitely adds value and enhances network communication privacy.
2. DNS over HTTPS (DoH) vs DNS over TLS (DoT)
DNS over TLS (or DoT) is regarded by some as being more or less the same thing with DoH, but this is not accurate. It`s true, both types of protocols, DoH and DoT achieve the same result: encrypting your DNS communications. However, each type of DNS protocol uses a different port for this encryption they make and the focus of each.
The DoH encryption allows, theoretically, network admins to view the encrypted DNS traffic should an issue arise. Unlike it, DoT encryption can protect data even from admins.
The fans of DoT protocols state that this DNS over TLS standard is a better fit for human rights concerns in problematic countries. At the same time, in countries where freedom of speech may be limited, the only effect of enabling DoT encryption may be that it draws attention. Simply put, authoritarian regimes may frown upon those who adopt DoT instead of the mainstream DoH.
Other than that, there is also the technical difference of the port used. DNS over TLS has its own dedicated TLS port, Port 853. DNS over HTTPS uses a different one, Port 443. This internet port (Port 443) is the current standard for all HTTPS communications, so it makes sense that DoH uses it too.
How Chrome and Mozilla Are Implementing DNS over HTTPS (DoH)
In the past years, both Google Chrome and Mozilla included DNS over HTTPS by default in their browsers.
Chrome
After the Chrome team experimented with the new DoH protocol only for a limited number of users, in May 2020, it introduced a secure DNS feature that implemented DNS over HTTPS. However, Chrome does not automatically switch DNS server to DoH. So, you need to enable DNS over HTTPS in Chrome yourself, either on your machine, or through Group Policy. To enable it on your endpoint, follow the steps:
- Open Chrome and click the three-dotted button on the top-right corner to open the Menu.
- Select ”Settings”.
- Click on ”Privacy and Security”.
- Click the ”Security” option.
- Scroll down and enable the ”Always use secure connections” and ”Use secure DNS” options.
Mozilla
To their credit, Mozilla has been working on DNS over HTTPS implementation for a longer time than Chrome. Since they have released version 63 of Firefox, Mozilla can enable DNS-over-HTTPS (DoH) by default for its users. In 2019, Mozilla succeeded rolling out DoH by default to all Firefox desktop users in the US. Canada followed in 2021. Starting March 2022, Firefox desktop users in Russia and Ukraine got default DoH to. Other countries will follow.
However, Firefox allows both users and organizations – through enterprise policies and a special-purpose domain lookup – to disable DoH in case it interferes with other preferred policy.
To enable or disable Mozilla DoH, follow the steps:
- Select
- In the panel, scroll to Network Settings and click ”Setting”
- In the dialog box that opens, go down to Enable DNS over HTTPS.
- On: select the Enable DNS over HTTPS checkbox. Select a provider or set up a custom provider (see below).
- Off: deselect the Enable DNS over HTTPS checkbox.
In the end, simply click ”OK” to save your changes and close the box.
How to Enable DNS over HTTPS in Windows 10
Enabling DNS over HTTPS in Windows 10 is a simple way to implement this functionality for all users and applications making DNS queries, including web browsers.
Nevertheless, keep in mind that Windows 10 should be up to date on your endpoints to ensure the DNS over HTTPS feature is available. For enabling via Settings, this means Build 20185 or higher, while for the registry edit option you need to have Build 19628 or higher.
Enabling DNS over HTTPS via Windows 10 Settings
For Windows 10 Build 20185 or higher, you need to go to the Settings > Network & Internet menu on your machine. There are a few steps to follow for this:
- Open Settings.
- Search for the Network status menu and open it.
- Select the desired Internet connection and open Properties.
- Under IP settings, click Edit.
- Choose the Manual selection, then toggle IPv4 on.
- Specify IP addresses for Preferred DNS and Alternate DNS.
- Windows 10 currently supports three DNS over HTTPS providers:
- Google – Primary IP: 8.8.8.8, Alternate IP: 8.8.4.4
- Cloudflare – Primary IP: 1.1.1.1, Alternate IP: 1.0.0.1
- Quad9 – Primary IP: 9.9.9.9, Alternate IP: 149.112.112.112
- Select Encrypted only for encryption under both Preferred DNS and Alternate DNS.
- Follow the same steps to configure IPv6 as well.
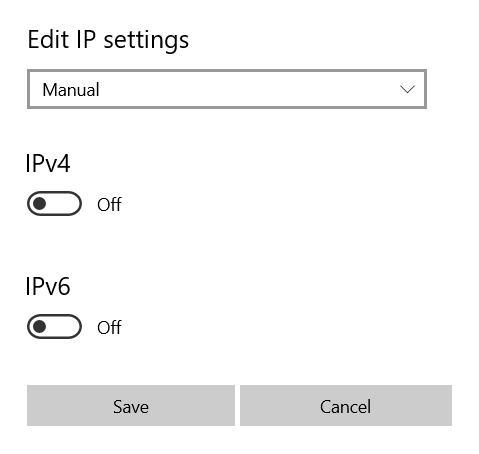
Edit IP settings menu in Windows 10.
Enabling DNS over HTTPS in the Windows 10 Registry
For Windows 10 Build 19628 or higher, you need to open the Registry Editor on your machine and make the necessary DoH changes there. There are a few steps to follow for this:
- Open Registry Editor.
- Navigate to HKEY_LOCAL_MACHINESYSTEMCurrentControlSetServicesDnscacheParameters.
- Create a DWORD named “EnableAutoDoh” with a value of 2.
- Reboot the machine.
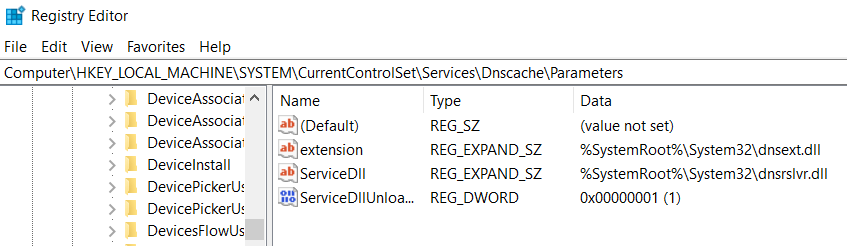
Registry Editor path for DoH enabling in Windows 10.
After the endpoint restarts, you’ll need to change the Preferred DNS and Alternate DNS addresses on it to one of the three I listed below, namely Google, Cloudflare, or Quad9. These are the only DNS over HTTPS options supported by Windows 10 at the moment.
Go under your network adapter’s Internet Protocol Version 4 (TCP/IPv4) and change the existing entries with one of the three. Do the same for IPv6 if necessary.
How DNS Traffic Filtering Solutions Need to Adapt to HTTPS
As most organizations are already aware, a DNS traffic filtering solution is crucial for their cybersecurity environment. But while most organizations are already using a DNS traffic filter, the dilemma brought on by DoH is that compatibility issues may arise once browsers start using DoH by default.
DNS traffic filtering solutions are using the settings built-in Operating Systems to perform DNS queries. But if the browser no longer uses the standard DNS port (53) for queries and instead switches to the DoH one (443), the traffic filtering solution will lose sight of those queries.
While DoH indeed brings more privacy by default, it should not be expected to replace compliance or security measures. Companies should still be warned that DoH does not replace other cybersecurity policies and tools.
On the downside, when the DNS queries from the browser are wrong or intentionally misled by threat actors, the DNS traffic filter might have trouble catching on. Also, DNS over HTTPS protocols might be used to display the ads which would have otherwise been blocked (since these solutions circumvent filters).
This is why when choosing a DNS traffic filter provider, you need to make sure that they support DNS over HTTPS correctly. Our Heimdal™ Threat Prevention solution, for example, comes with a solid integration of DoH.
DNS over HTTPS Benefits
Encrypting the DNS traffic communications brought about more privacy and better security for users and organizations. The main benefits are:
- DoH encrypts the DNS Name resolution traffic to hide the users’ online activities. Their DNS queries will remain private not only to the ISP, but to anyone else.
- Encrypting DNS over HTTPS prevents Man-in-the-Middle attacks
- DoH also prevents DNS spoofing, as the communication between the DNS servers and the web browsers can no longer be read or tampered with.
DNS over HTTPS Risks
It appears as if DoH was created with only the home user in mind and less concern regarding its impact on network security in a business environment. The problem with DoH is that it might bypass your security tools, if not handled properly.
Here are some of the risks that organizations might confront with in case DoH is not properly implemented:
- Ineffective DNS Firewalls – since all queries are encrypted, users would be able to access social media or malicious links from phishing emails
- DNS traffic monitoring is not possible anymore
- No DNS blocking and filtering to handle take-down notices
- Exposure to cyber threats that exploit the lack of visibility to communicate with C2s.
Can Threat Actors Abuse DoH?
We`re most sorry to say that the answer is yes. Back in 2019, Godlua, a Linux DDoS bot, was the first malware strain detected using DoH to hide its DNS traffic. The malware was written for Linux servers and used DoH to hide DNS traffic.
More recently, a Chinese threat group was discovered infecting Linux devices with malware named ”ChamelDoH”. The malware enables DNS over HTTPS communications with attackers’ servers.
Antivirus is no longer enough to keep an organization’s systems secure.
Heimdal® Threat Prevention
– Endpoint
Is our next gen proactive DNS-Layer security that stops unknown
threats before they reach your system.
- Machine learning powered scans for all incoming online traffic;
- Stops data breaches before sensitive info can be exposed to the outside;
- Advanced DNS, HTTP and HTTPS filtering for all your endpoints;
- Protection against data leakage, APTs, ransomware and exploits;
How We Cover DoH within Heimdal® Threat Prevention
Heimdal is the world’s first vendor to integrate true DNS over HTTPS in a product – Threat Prevention Endpoint. We thus evolved past the standard rerouting of DNS packages.
DoH makes sure that any communication between the browser and the DNS server is encrypted. This way it keeps your IT environment safe from DNS spoofing and man-in-the-middle (MitM) attacks.
Our functionality encrypts DNS traffic by circulating all queries through an HTTPS-encrypted session. As a result, no threat actor will be able to compromise the resolution request results and direct the end user’s browser toward a malicious website.

As a user of Threat Prevention Endpoint, all you need to do is go to Endpoint Settings -> Threat Prevention Endpoint -> Compatibility Settings area of the Heimdal™ dashboard. Then tick the check box called “DNS over HTTPS Server”.
Once you enabled it, all DNS queries will be resolved via the DoH server that is set through the Group Policy settings, except the server itself.
Wrapping Up
Like any IT innovation, DNS over HTTPS did pose a few challenges at first, until everyone got aligned with it. Some might say it still is a challenge. However, once DoH became the standard, its benefits greatly outweighed the difficulties it once posed.
Integrating DoH with endpoint security makes maintaining effective DNS filtering possible despite the encryption of DNS traffic.
Original Post URL: https://heimdalsecurity.com/blog/dns-over-https-doh/
Category & Tags: Networking,DNS – Networking,DNS





















































