Reducing the Noise: Why Vulnerability Types MatterMost application security testing focuses on server-side vulnerabilities. While vulnerability management alerts are necessary within today’s threat landscape for increased...
USENIX Security ’22 – Daniel Townley, Kerem Arıkan, Yu David Liu, Dmitry Ponomarev, Oğuz Ergin – ‘Composable Cachelets: Protecting Enclaves From Cache Side-Channel Attacks’
USENIX Security ’22 – Daniel Townley, Kerem Arıkan, Yu David Liu, Dmitry Ponomarev, Oğuz Ergin – ‘Composable Cachelets: Protecting Enclaves From Cache Side-Channel Attacks’Our thanks to...
Software supply chain security and SBOM automation: The next big step in risk management
Software supply chain security and SBOM automation: The next big step in risk management Over the last several years, supply chain risk management has evolved into...
New Mirai botnet variant V3G4 targets Linux servers, IoT devices
New Mirai botnet variant V3G4 targets Linux servers, IoT devicesA new variant of Mirai — the botnet malware used to launch massive DDoS attacks —has been...
EU parliamentary committee says ‘no’ to EU-US data privacy framework
EU parliamentary committee says 'no' to EU-US data privacy frameworkProgress on ratifying the Trans-Atlantic Data Policy Framework hit a snag, as a parliamentary committee rejected a...
7 reasons to avoid investing in cyber insurance
7 reasons to avoid investing in cyber insuranceWith cyberattacks rising at an alarming rate around the world, cyber insurance has become an increasingly popular layer of...
GoDaddy connects a slew of past attacks to a multiyear hacking campaign
GoDaddy connects a slew of past attacks to a multiyear hacking campaignWeb hosting and infrastructure provider GoDaddy said it suspects a recent attack on its infrastructure...
Three-quarters of businesses braced for ‘serious’ email attack this year
Three-quarters of businesses braced for ‘serious’ email attack this yearIT security leaders at three-out-of-four global businesses expect an email-borne attack will have serious consequences for their...
Why CISOs change jobs
Why CISOs change jobsBeing a CISO is a hard job. You must constantly balance business, technology, and regulatory requirements against things like employee and adversary behavior....
10 dark web monitoring tools
10 dark web monitoring toolsThe dark web is the place where every CISO hope their company’s data will not end up. It consists of sites that...
DNA Diagnostic Center fined $400,000 for 2021 data breach
DNA Diagnostic Center fined $400,000 for 2021 data breachDNA Diagnostics Center, a DNA testing company, will pay a penalty of $400,000 to the attorneys general of...
Cyber arms race, economic headwinds among top macro cybersecurity risks for 2023
Cyber arms race, economic headwinds among top macro cybersecurity risks for 2023Despite the billions of dollars poured annually into cybersecurity by investors, organizations, academia, and government,...
Alcatraz AI streamlines facial recognition access control with mobile update
Alcatraz AI streamlines facial recognition access control with mobile updateAccess control provider Alcatraz AI is adding web-based, mobile enrollment and privacy consent management to its flagship...
What is Traffic Light Protocol? Here’s how it supports CISOs in sharing threat data
What is Traffic Light Protocol? Here's how it supports CISOs in sharing threat dataTraffic Light Protocol (TLP) was created to facilitate greater sharing of potentially sensitive...
Backdoor deployment overtakes ransomware as top attacker action
Backdoor deployment overtakes ransomware as top attacker actionDeployment of backdoors on networks was the top action attackers made in almost a quarter of all incidents remediated...
Police Arrest Trio in Multimillion-Dollar Extortion Case
Police Arrest Trio in Multimillion-Dollar Extortion CaseMen are accused of stealing data on tens of millions of victimsRead MoreMen are accused of stealing data on tens...
Governments Targeted by Discord-Based Threat Campaign
Governments Targeted by Discord-Based Threat CampaignThreat actor delivers multiple malware types via PureCrypterRead MoreThreat actor delivers multiple malware types via PureCrypter
North Carolina Business Magnate Indicted in $2bn Fraud Case
North Carolina Business Magnate Indicted in $2bn Fraud CaseInsurance company owner alleged to have skimmed off millionsRead MoreInsurance company owner alleged to have skimmed off millions
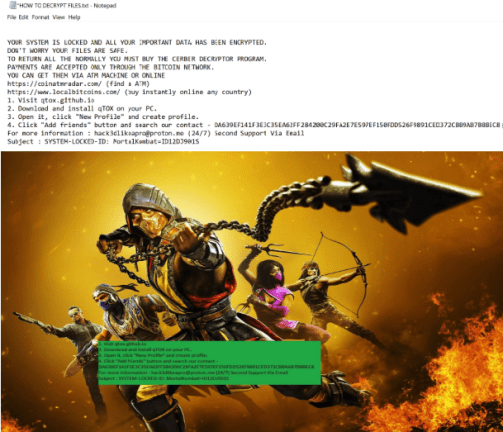
Bitdefender released a free decryptor for the MortalKombat Ransomware family
Bitdefender released a free decryptor for the MortalKombat Ransomware familyAntivirus company Bitdefender has released a free decryptor for the recently discovered ransomware family MortalKombat. Good news for the...
Pen testing report: IT budgets should focus on entire security stack
Pen testing report: IT budgets should focus on entire security stackWith nearly 90% of companies reporting cyberattacks, pen testing budgets are on the rise, with cloud...
New MortalKombat ransomware decryptor recovers your files for free
New MortalKombat ransomware decryptor recovers your files for freeCybersecurity company Bitdefender has released a free MortalKombat ransomware decryptor that victims can use to restore their files...
Windows 11 KB5022913 preview update comes with newly announced features
Windows 11 KB5022913 preview update comes with newly announced featuresMicrosoft has released the optional February 2023 optional cumulative update for all editions of Windows 11 22H2...
Windows 11 KB5022913 causes boot issues if using UI customization apps
Windows 11 KB5022913 causes boot issues if using UI customization appsMicrosoft says the KB5022913 February 2023 non-security preview release is causing boot issues on Windows 11...
CISA warns of hackers exploiting ZK Java Framework RCE flaw
CISA warns of hackers exploiting ZK Java Framework RCE flawThe U.S. Cybersecurity & Infrastructure Security Agency (CISA) has added CVE-2022-36537 to its "Known Exploited Vulnerabilities Catalog"...
Proofpoint’s 2023 State of the Phish Report: Threat Actors Double Down on Emerging and Tried-and-Tested Tactics to Outwit Employees
Proofpoint’s 2023 State of the Phish Report: Threat Actors Double Down on Emerging and Tried-and-Tested Tactics to Outwit EmployeesPost ContentRead MoreProofpoint News Feed
Cracking the code: How to avoid 7 common mistakes in corporate information security
Cracking the code: How to avoid 7 common mistakes in corporate information securityEXECUTIVE SUMMARY: In today’s digital landscape, corporations are tasked with the responsibility of safeguarding...
Simplifying your Security Stack with SSE Integration
Simplifying your Security Stack with SSE IntegrationPost ContentRead MoreDataBreachToday.com RSS Syndication
Live Webinar | Don’t Be Held Hostage: Detect and Intercept Pre-Ransomware Activity and Ransom Notes
Live Webinar | Don't Be Held Hostage: Detect and Intercept Pre-Ransomware Activity and Ransom NotesPost ContentRead MoreDataBreachToday.com RSS Syndication
Checkmarx Snags Ex-Tricentis CEO Sandeep Johri as New Leader
Checkmarx Snags Ex-Tricentis CEO Sandeep Johri as New LeaderJohri Replaces Emmanuel Benzaquen, Who Has Led the App Security Company Since 2006For the first time in its...
Supreme Court Hears Healthcare Identity Theft Case
Supreme Court Hears Healthcare Identity Theft CaseCase Involved Use of a Patient's Name to Overbill MedicaidA case before the U.S. Supreme Court may limit federal prosecutors'...