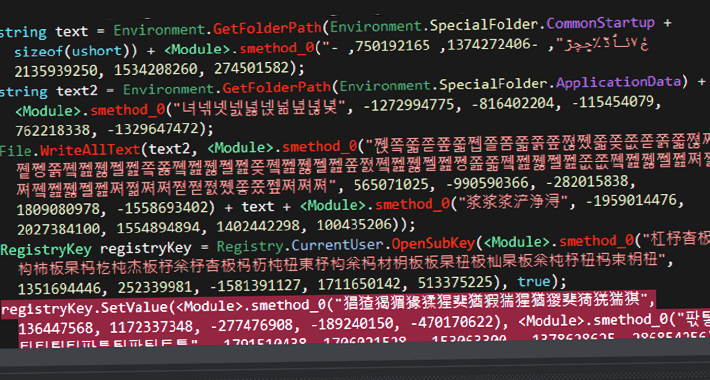
New ScrubCrypt Crypter Used in Cryptojacking Attacks Targeting Oracle WebLogicThe infamous cryptocurrency miner group called 8220 Gang has been observed using a new crypter called ScrubCrypt...
Iranian Hackers Target Women Involved in Human Rights and Middle East Politics
Iranian Hackers Target Women Involved in Human Rights and Middle East PoliticsIranian state-sponsored actors are continuing to engage in social engineering campaigns targeting researchers by impersonating...
Does Your Help Desk Know Who’s Calling?
Does Your Help Desk Know Who's Calling?Phishing, the theft of users' credentials or sensitive data using social engineering, has been a significant threat since the early...
IceFire Ransomware Exploits IBM Aspera Faspex to Attack Linux-Powered Enterprise Networks
IceFire Ransomware Exploits IBM Aspera Faspex to Attack Linux-Powered Enterprise NetworksA previously known Windows-based ransomware strain known as IceFire has expanded its focus to target Linux...
Hackers Exploiting Remote Desktop Software Flaws to Deploy PlugX Malware
Hackers Exploiting Remote Desktop Software Flaws to Deploy PlugX MalwareSecurity vulnerabilities in remote desktop programs such as Sunlogin and AweSun are being exploited by threat actors...
North Korean UNC2970 Hackers Expands Operations with New Malware Families
North Korean UNC2970 Hackers Expands Operations with New Malware FamiliesA North Korean espionage group tracked as UNC2970 has been observed employing previously undocumented malware families as part of...
Xenomorph Android Banking Trojan Returns with a New and More Powerful Variant
Xenomorph Android Banking Trojan Returns with a New and More Powerful VariantA new variant of the Android banking trojan named Xenomorph has surfaced in the wild,...
When Partial Protection is Zero Protection: The MFA Blind Spots No One Talks About
When Partial Protection is Zero Protection: The MFA Blind Spots No One Talks AboutMulti-factor Authentication (MFA) has long ago become a standard security practice. With a...
International Law Enforcement Takes Down Infamous NetWire Cross-Platform RAT
International Law Enforcement Takes Down Infamous NetWire Cross-Platform RATA coordinated international law enforcement exercise has taken down the online infrastructure associated with a cross-platform remote access...
China-linked Hackers Targeting Unpatched SonicWall SMA Devices with Malware
China-linked Hackers Targeting Unpatched SonicWall SMA Devices with MalwareA suspecting China-linked hacking campaign has been observed targeting unpatched SonicWall Secure Mobile Access (SMA) 100 appliances to drop malware...
New Version of Prometei Botnet Infects Over 10,000 Systems Worldwide
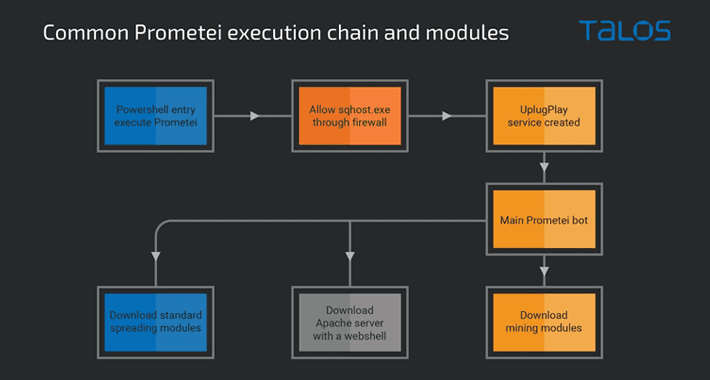
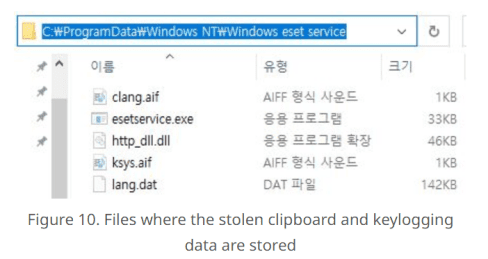
New Version of Prometei Botnet Infects Over 10,000 Systems WorldwideAn updated version of a botnet malware called Prometei has infected more than 10,000 systems worldwide since November 2022....
Hunting Emotet: How Behavioural Hunting Trumps IOC Detection Every Time
Hunting Emotet: How Behavioural Hunting Trumps IOC Detection Every TimeAs a threat hunter, I have seen the evolution of cyber threats firsthand and the challenges that...
USENIX Security ’22 – Shujiang Wu, Jianjia Yu, Min Yang, Yinzhi Cao – ‘Rendering Contention Channel Made Practical In Web Browsers’
USENIX Security ’22 – Shujiang Wu, Jianjia Yu, Min Yang, Yinzhi Cao – ‘Rendering Contention Channel Made Practical In Web Browsers’Our thanks to USENIX for publishing...
A security use case for ChatGPT: Email Scam Robo Judge
A security use case for ChatGPT: Email Scam Robo JudgeI have been noodling around with ChatGPT recently and have found a nice little use case that...
PlugX malware delivered by exploiting flaws in Chinese programs
PlugX malware delivered by exploiting flaws in Chinese programsResearchers observed threat actors deploying PlugX malware by exploiting flaws in Chinese remote control programs Sunlogin and Awesun....
Clop ransomware gang begins extorting GoAnywhere zero-day victims
Clop ransomware gang begins extorting GoAnywhere zero-day victimsThe Clop ransomware gang has begun extorting companies whose data was stolen using a zero-day vulnerability in the Fortra...
US Bracing for Bolder, More Brazen Russian Cyberattacks
US Bracing for Bolder, More Brazen Russian CyberattacksPost ContentRead MoreProofpoint News Feed
Access management must get stronger in a zero-trust world
Access management must get stronger in a zero-trust worldPost ContentRead MoreProofpoint News Feed
Scammers Impersonate Barclays, Shell As Investment Fraud Soars
Scammers Impersonate Barclays, Shell As Investment Fraud SoarsPost ContentRead MoreProofpoint News Feed
Russian Influence Duo Targets Politicians, CEOs for Embarrassing Video Calls
Russian Influence Duo Targets Politicians, CEOs for Embarrassing Video CallsPost ContentRead MoreProofpoint News Feed
The Anti-Fragile CISO
The Anti-Fragile CISOPost ContentRead MoreProofpoint News Feed
New Version of Prometei Botnet Infects Over 10,000 Systems Worldwide
New Version of Prometei Botnet Infects Over 10,000 Systems WorldwideAn updated version of a botnet malware called Prometei has infected more than 10,000 systems worldwide since November 2022....
SHEIN shopping app goes rogue, grabs price and URL data from your clipboard
SHEIN shopping app goes rogue, grabs price and URL data from your clipboardIt's not exactly data theft, but it's worryingly close to "unintentional treachery" - apparently...
S3 Ep125: When security hardware has security holes [Audio + Text]
S3 Ep125: When security hardware has security holes [Audio + Text]Lastest episode - listen now! (Full transcript inside.)Read MoreNaked SecurityLastest episode - listen now! (Full transcript...
‘Extraordinary, Egregious’ Data Breach at House and Senate
‘Extraordinary, Egregious’ Data Breach at House and Senate Capitol Trouble: Senators, representatives and staffers suffer PII leak. Could it finally kickstart some action? The post ‘Extraordinary, Egregious’...
Vendor Tips for the SIG Questionnaire
Vendor Tips for the SIG Questionnaire Many companies understand the pain of constantly filling out extremely arduous customer- requested security questionnaires. Most of the time, the...
USENIX Security ’22 – Mohammadkazem Taram, Xida Ren, Ashish Venkat, Dean Tullsen – ‘SecSMT: Securing SMT Processors against Contention-Based Covert Channels’
USENIX Security ’22 – Mohammadkazem Taram, Xida Ren, Ashish Venkat, Dean Tullsen – ‘SecSMT: Securing SMT Processors against Contention-Based Covert Channels’Our thanks to USENIX for publishing...
Digital Trust Digest: This Week’s Must-Know News
Digital Trust Digest: This Week’s Must-Know NewsThe Digital Trust Digest is a curated overview of the week’s top cybersecurity news. Here's what happened the week of...
Sick of that Security Questionnaire? Automation is the Answer
Sick of that Security Questionnaire? Automation is the AnswerSecurity questionnaires (SQs) are not fun. They’re time-consuming, tedious work and sometimes, they’re the one thing standing between...
Camelot Launches Cybersecurity Service Augmented by ML
Camelot Launches Cybersecurity Service Augmented by ML Camelot this week launched a Secure360 cybersecurity platform that enables its cybersecurity team to leverage machine learning algorithms to...