Mozilla Firefox gets built-in Firefox Relay controlsMozilla has announced the integration of Firefox Relay, an email protection system that helps users evade trackers and spammers, directly...
CISA warns of Adobe ColdFusion bug exploited as a zero-day
CISA warns of Adobe ColdFusion bug exploited as a zero-dayCISA has added a critical vulnerability impacting Adobe ColdFusion versions 2021 and 2018 to its catalog of...
Cyber security for the public sector: What you need to know
Cyber security for the public sector: What you need to knowBy Mazhar Hamayun, cyber security engineer and member of the Office of the CTO at Check...
Hundreds of thousands of customer records stolen from lender Latitude in cyber-attack
Hundreds of thousands of customer records stolen from lender Latitude in cyber-attackThe company, which provides credit to JB Hi-Fi and Harvey Norman shoppers, says 100,000 ID...
CISOs on the Human Factor: How Well are we Preparing our People to Protect our Organisations?
CISOs on the Human Factor: How Well are we Preparing our People to Protect our Organisations?CISOs have faced a broad and varied set of challenges in...
CISOs on Advanced Threats: How do we Respond to Rising Cybersecurity Stakes?
CISOs on Advanced Threats: How do we Respond to Rising Cybersecurity Stakes?Cybercriminals have been launching attacks against our people, networks, and services for decades with varying...
Panel Discussion | FTC Safeguards Rule: Get Compliant and Get on with Business
Panel Discussion | FTC Safeguards Rule: Get Compliant and Get on with BusinessPost ContentRead MoreDataBreachToday.com RSS Syndication
CISA Alert: 4-Year-Old Software Bug Exploited at US Agency
CISA Alert: 4-Year-Old Software Bug Exploited at US AgencyProgress Telerik UI's .NET Vulnerability Could Lead to Remote Code ExecutionU.S. cybersecurity officials on Thursday issued an alert...
Rapid7 Buys Ransomware Prevention Firm Minerva Labs for $38M
Rapid7 Buys Ransomware Prevention Firm Minerva Labs for $38MDeal Will Help Rapid7 Neutralize and Prevent Malicious Activity Prior to ExecutionRapid7 has purchased a ransomware prevention vendor...
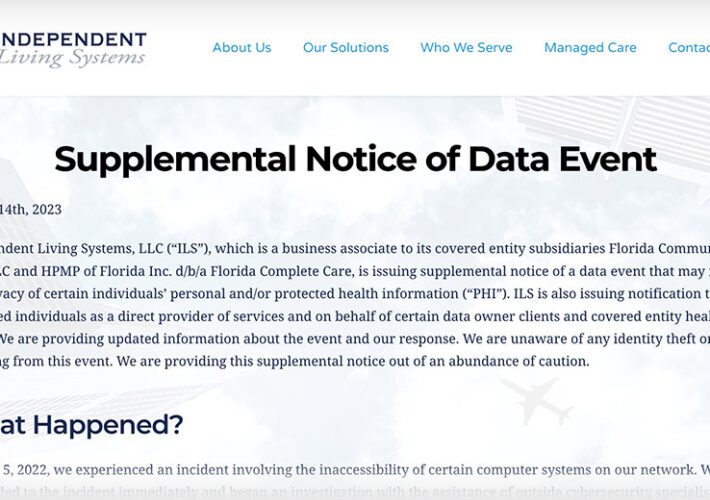
Long-Term Care Services Firm Says Breach Affects 4.2 Million
Long-Term Care Services Firm Says Breach Affects 4.2 Million'Inaccessible Computers' Incident Initially Reported as Affecting 501 PeopleA vendor of clinical and third-party administrative services to managed...
Acer confirma que ha sido hackeada: roban y venden 160 GB de datos de uno de sus servidores
Acer confirma que ha sido hackeada: roban y venden 160 GB de datos de uno de sus servidoresAcer confirma hackeo después de que salga a la...
Microsoft Fixes Russia-Exploited Zero Day
Microsoft Fixes Russia-Exploited Zero DayPatch Tuesday Fixes Address 80 Vulnerabilities, Including 8 Critical OnesMicrosoft's March dump of patches fixes two actively exploited zero-day vulnerabilities, including a...
FBI: Ransomware afectó a 860 organizaciones de infraestructura crítica en 2022
FBI: Ransomware afectó a 860 organizaciones de infraestructura crítica en 2022La Oficina Federal de Investigaciones (FBI) reveló en su Informe sobre delitos en Internet de 2022...
Tick APT Targeted High-Value Customers of East Asian Data-Loss Prevention Company
Tick APT Targeted High-Value Customers of East Asian Data-Loss Prevention CompanyA cyberespionage actor known as Tick has been attributed with high confidence to a compromise of...
The Different Methods and Stages of Penetration Testing
The Different Methods and Stages of Penetration TestingThe stakes could not be higher for cyber defenders. With the vast amounts of sensitive information, intellectual property, and...
New Cryptojacking Operation Targeting Kubernetes Clusters for Dero Mining
New Cryptojacking Operation Targeting Kubernetes Clusters for Dero MiningCybersecurity researchers have discovered the first-ever illicit cryptocurrency mining campaign used to mint Dero since the start of...
YoroTrooper Stealing Credentials and Information from Government and Energy Organizations
YoroTrooper Stealing Credentials and Information from Government and Energy OrganizationsA previously undocumented threat actor dubbed YoroTrooper has been targeting government, energy, and international organizations across Europe as part...
Palo Alto Networks Uses Machine Learning to Reduce SASE Costs
Palo Alto Networks Uses Machine Learning to Reduce SASE Costs Palo Alto Networks today revealed it is using artificial intelligence to automate the management of its...
Raising Awareness of Connected Device Security
Raising Awareness of Connected Device Security October is officially cybersecurity awareness month, originally designated back in 2004 by United States President George W. Bush and Congress...
Data Protection Strategy for Resource-Strapped IT Teams
Data Protection Strategy for Resource-Strapped IT TeamsIT teams are increasingly asked to do more with less. With the right data protection strategy in place and strategic...
Protecting Your Organization’s Digital Identity: A Guide to Managed Attribution
Protecting Your Organization’s Digital Identity: A Guide to Managed AttributionManaged attribution has become a powerful technique for organizations to gather intelligence and protect themselves from cyber...
(Ab)using Adobe Acrobat Sign to distribute malware
(Ab)using Adobe Acrobat Sign to distribute malware Bad actors have been distributing malware through email for decades. Over time, security technology has evolved and improved greatly,...
Cyber Risk Quantification based on the MITRE ATT&CK® Framework
Cyber Risk Quantification based on the MITRE ATT&CK® FrameworkArticles related to cyber risk quantification, cyber risk management, and cyber resilience. The post Cyber Risk Quantification based...
How to Handle Secrets in Jenkins
How to Handle Secrets in JenkinsDevOps engineers must handle secrets with care. In this series, we summarize best practices for leveraging secrets with your everyday tools....
Unpacking the National Cybersecurity Strategy: Part 1
Unpacking the National Cybersecurity Strategy: Part 1Leverage this expert analysis to better understand, prepare for, and operationalize the overarching themes and initiatives presented by the National...
In the News | Why Cybersecurity Threats on Schools Have Become More Frequent in the Past Five Years?
In the News | Why Cybersecurity Threats on Schools Have Become More Frequent in the Past Five Years?This podcast was originally published in Redefining Society Podcast...
Dell Adds CrowdStrike to Cybersecurity Services Portfolio
Dell Adds CrowdStrike to Cybersecurity Services Portfolio Dell Technologies today announced an alliance with CrowdStrike as part of a larger initiative to expand the cybersecurity services...
Trustwave teams up with Trellix for better managed security
Trustwave teams up with Trellix for better managed securityManaged detection and response (MDR) company Trustwave said Wednesday that it will be partnering with extended detection and...
Palo Alto announces new SD-WAN features for IoT security, compliance support
Palo Alto announces new SD-WAN features for IoT security, compliance supportCybersecurity vendor Palo Alto has announced new software-defined wide area network (SD-WAN) features in its Prisma...
Beyond Identity launches Zero Trust Authentication to align verification with zero-trust principles
Beyond Identity launches Zero Trust Authentication to align verification with zero-trust principlesMultifactor authentication (MFA) provider Beyond Identity has announced the launch of Zero Trust Authentication —...