Google Exposes 18 Zero-Day Flaws in Samsung Exynos ChipsFour of these vulnerabilities enabled potential attackers to perform remote code executionRead MoreFour of these vulnerabilities enabled potential...
Telegram, WhatsApp Trojanized to Target Cryptocurrency Wallets
Telegram, WhatsApp Trojanized to Target Cryptocurrency WalletsMost of these apps rely on clipper malware to steal the contents of the Android clipboardRead MoreMost of these apps...
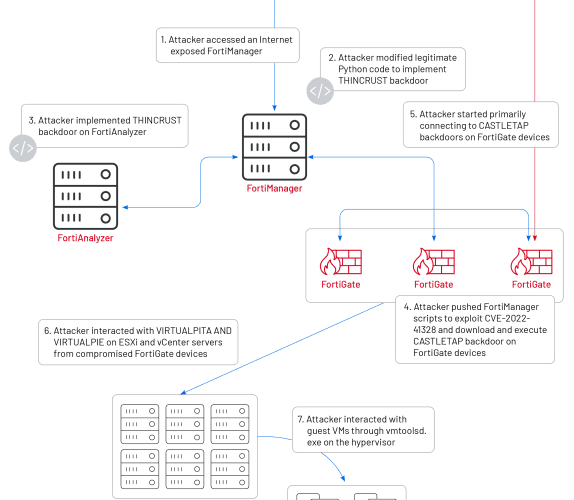
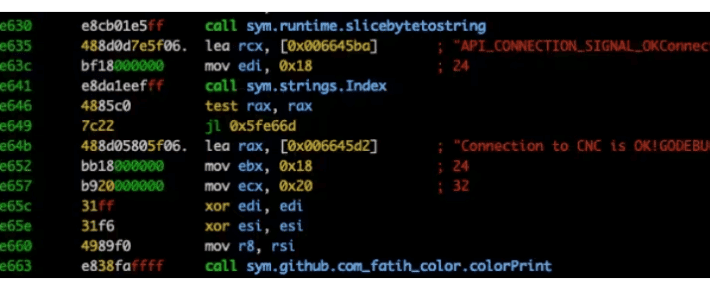
China-linked APT likely linked to Fortinet zero-day attacks
China-linked APT likely linked to Fortinet zero-day attacksAn alleged Chinese threat actor group is behind attacks on government organizations exploiting a Fortinet zero-day flaw (CVE-2022-41328). A...
Top 5 Insider Threats to Look Out For in 2023
Top 5 Insider Threats to Look Out For in 2023Unquestionably, ‘insider threats’ is one of the most neglected aspects of cybersecurity and some companies fail to...
HinataBot, a new Go-Based DDoS botnet in the threat landscape
HinataBot, a new Go-Based DDoS botnet in the threat landscapeA new Golang-based DDoS botnet, tracked as HinataBot, targets routers and servers by exploiting known vulnerabilities. Akamai researchers spotted...
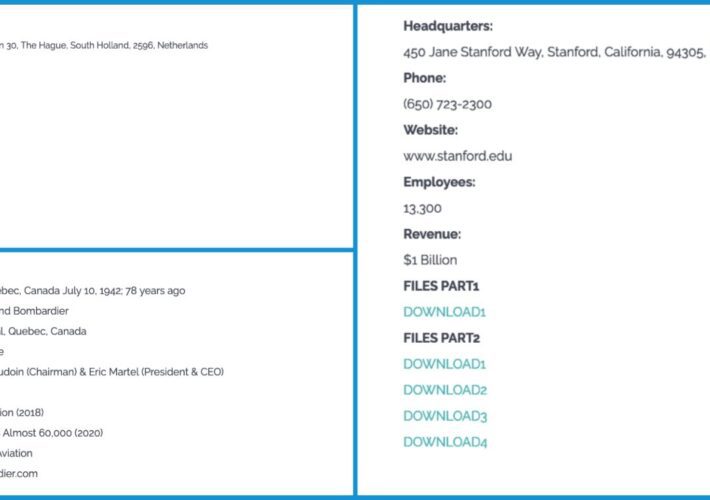
Cl0p ransomware gang claims the hack of Shell, Bombardier, and Stanford U
Cl0p ransomware gang claims the hack of Shell, Bombardier, and Stanford UThe Cl0p ransomware gang claimed dozens of new victims in the past 24 hours, including...
Weekly Update 339
Weekly Update 339Why can't I audio right? It's my 339th video and I still make mistakes ? But it came good and we got a decent...
DDoS-as-a-service Attacks. What Are They and How Do They Work?
DDoS-as-a-service Attacks. What Are They and How Do They Work?This is the time to remind you again that online threats are always changing and so should...
Makop Ransomware: The Arsenal of Cybercriminals Becomes Known
Makop Ransomware: The Arsenal of Cybercriminals Becomes KnownIn operation since 2020, the Makop ransomware gang is classified as a tier-B ransomware gang. The threat actor has...
BianLian Ransomware: The Dangerous Shift Toward Pure Data Extortion
BianLian Ransomware: The Dangerous Shift Toward Pure Data ExtortionBianLian is a ransomware group that first appeared in July 2022, successfully infiltrating several high-profile organizations. It seems...
AI-Generated YouTube Videos Spread Raccoon, RedLine, and Vidar Info-stealers
AI-Generated YouTube Videos Spread Raccoon, RedLine, and Vidar Info-stealersHackers use AI-generated YouTube videos to deploy Raccoon, RedLine, and Vidar malware. The videos look like tutorials on...
5 Ways Heimdal® Protects You From DNS Attacks
5 Ways Heimdal® Protects You From DNS AttacksAs cyber-attacks continue to proliferate, it’s essential for organizations to stay ahead of the game when it comes to...
What Is Stack Smashing?
What Is Stack Smashing?Stack smashing is a type of vulnerability that can lead to serious security breaches. This vulnerability occurs when a hacker exploits a flaw...
Android phones can be hacked just by someone knowing your phone number
Android phones can be hacked just by someone knowing your phone numberWell, this isn’t good. Google has issued a warning that some Android phones can be...
Free decryptor released for Conti-based ransomware following data leak
Free decryptor released for Conti-based ransomware following data leakSecurity researchers have released a new decryption tool which should come to the rescue of some victims of...
Turbocharge your IT career with cybersecurity training for just $50
Turbocharge your IT career with cybersecurity training for just $50Whether you have one year or ten years of IT experience, you'll have an edge when applying...
How to prevent data theft by existing and departing employees
How to prevent data theft by existing and departing employeesSome 12% of employees take customer details, health records, sales contracts and other confidential data when leaving...
Microsoft shares script to fix WinRE BitLocker bypass flaw
Microsoft shares script to fix WinRE BitLocker bypass flawMicrosoft has released a script to make it easier to patch a BitLocker bypass security vulnerability in the...
RAT developer arrested for infecting 10,000 PCs with malware
RAT developer arrested for infecting 10,000 PCs with malwareUkraine's cyberpolice has arrested the developer of a remote access trojan (RAT) malware that infected over 10,000 computers...
Hitachi Energy confirms data breach after Clop GoAnywhere attacks
Hitachi Energy confirms data breach after Clop GoAnywhere attacksHitachi Energy confirmed it suffered a data breach after the Clop ransomware gang stole data using a zero-day...
Why is TikTok banned from government phones – and should rest of us be worried?
Why is TikTok banned from government phones – and should rest of us be worried?UK has removed app over concerns data can be monitored by Chinese...
Webinar | Open Source License Compliance and M&A Activity: What You Don’t Know Can Hurt You
Webinar | Open Source License Compliance and M&A Activity: What You Don't Know Can Hurt YouPost ContentRead MoreDataBreachToday.com RSS Syndication
SVB Parent Company Seeks Bankruptcy Amid Asset Sale Process
SVB Parent Company Seeks Bankruptcy Amid Asset Sale ProcessSVB Financial Group Pursues Chapter 11 to Sell Assets Outside the Commercial BankThe former parent company of Silicon...
ISMG Editors: Will SVB Crash Kill Cybersecurity Innovation?
ISMG Editors: Will SVB Crash Kill Cybersecurity Innovation?Also: Blackbaud Fined; DOJ Reproaches Federal Contractor for Lax SecurityIn the latest weekly update, ISMG editors discuss how the...
The Importance of Physical Access Endpoint Detection
The Importance of Physical Access Endpoint Detection In our latest blog, Nozomi Networks Labs share insights into host-based threats, highlight the importance of endpoint detection sensors like...
SafeBreach Coverage for US-CERT Alert (AA23-074A) – Telerik Vulnerability in IIS Server
SafeBreach Coverage for US-CERT Alert (AA23-074A) – Telerik Vulnerability in IIS ServerSafeBreach coverage for US-CERT Alert (AA22-335A) - Cuba Ransomware The post SafeBreach Coverage for US-CERT...
USENIX Security ’22 – Lawrence Roy, Stanislav Lyakhov, Yeongjin Jang, Mike Rosulek – ‘Practical Privacy-Preserving Authentication For SSH’
USENIX Security ’22 – Lawrence Roy, Stanislav Lyakhov, Yeongjin Jang, Mike Rosulek – ‘Practical Privacy-Preserving Authentication For SSH’Our thanks to USENIX for publishing their Presenter’s outstanding...
Scams Lost US $10 BILLION in 2022 — Crypto Fraud Grows Fast
Scams Lost US $10 BILLION in 2022 — Crypto Fraud Grows Fast Ben is disappointed: FBI reports huge rise in cryptocurrency investment scams. Why am I not...
5 Things to Know About NIS2
5 Things to Know About NIS2We summarize the top 5 things to know about NIS2 and what you can do today to prepare for the new...
Top 8 Malicious Attacks Recently Found On PyPI
Top 8 Malicious Attacks Recently Found On PyPI The post Top 8 Malicious Attacks Recently Found On PyPI appeared first on Security Boulevard. Read MoreSecurity...