New ‘HinataBot’ botnet could launch massive 3.3 Tbps DDoS attacksA new malware botnet was discovered targeting Realtek SDK, Huawei routers, and Hadoop YARN servers to recruit...
Cybersecurity funds should go towards beefing up Centrelink voice authentication, Greens say
Cybersecurity funds should go towards beefing up Centrelink voice authentication, Greens sayDavid Shoebridge says some of the $10bn allocated to Redspice program should counter misuse of...
Who Wants to Fuel Independent and High Quality OSINT/Cybercrime and Threat Intelligence Research? Accepting BitCoin Donations
Who Wants to Fuel Independent and High Quality OSINT/Cybercrime and Threat Intelligence Research? Accepting BitCoin Donations Dear blog readers, Did you already grab a copy of...
URGENT ACTION RECOMMENDED – Microsoft Outlook Vulnerability (CVE-2023-23397)
URGENT ACTION RECOMMENDED – Microsoft Outlook Vulnerability (CVE-2023-23397)Summary: Microsoft disclosed a Microsoft Outlook Vulnerability (an RCE – remote code execution) titled “Microsoft Outlook Elevation of Privilege...
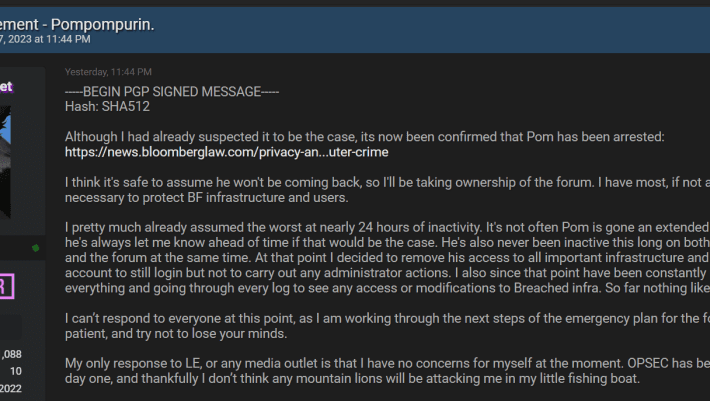
COURT DOC: US Federal Agents Arrest Alleged Administrator of Breach Forums “pompompurin”
COURT DOC: US Federal Agents Arrest Alleged Administrator of Breach Forums “pompompurin”On March 17, 2023, US federal agents arrested a New York individual for computer crimes...
What’s New in Cyolo 4.0
What’s New in Cyolo 4.0 2 min read Cyolo 4.0 has officially arrived! Discover all the details of this latest release, including (spoiler alert!) a simplified...
USENIX Security ’22 – Mohsen Minaei, Mainack Mondal, Aniket Kate – ‘Empirical Understanding Of Deletion Privacy: Experiences, Expectations, And Measures’
USENIX Security ’22 – Mohsen Minaei, Mainack Mondal, Aniket Kate – ‘Empirical Understanding Of Deletion Privacy: Experiences, Expectations, And Measures’Our thanks to USENIX for publishing their...
NBA is warning fans of a data breach after a third-party newsletter service hack
NBA is warning fans of a data breach after a third-party newsletter service hackThe NBA (National Basketball Association) disclosed a data breach after a third-party firm...
USENIX Security ’22 – David G. Balash, Xiaoyuan Wu, Miles Grant, Irwin Reyes, Adam J. Aviv – ‘Security And Privacy Perceptions Of Third-Party Application Access For Google Accounts’
USENIX Security ’22 – David G. Balash, Xiaoyuan Wu, Miles Grant, Irwin Reyes, Adam J. Aviv – ‘Security And Privacy Perceptions Of Third-Party Application Access For...
No More Missed Opportunities: Maximizing Your Threat Hunting Efforts
No More Missed Opportunities: Maximizing Your Threat Hunting EffortsThreat hunting has become an essential component of modern cybersecurity defenses. With the threat landscape constantly evolving, organizations...
Kaspersky released a new decryptor for Conti-based ransomware
Kaspersky released a new decryptor for Conti-based ransomwareKaspersky released a new version of the decryptor for the Conti ransomware that is based on the previously leaked...
Solving The AppSec Dilemma Across the Entire SDLC
Solving The AppSec Dilemma Across the Entire SDLCWhy organizations should adopt an integrated and continuous approach to application security education By Amy Baker, Security Education Evangelist,...
The Biggest Cyber Threats For The Financial Industry In 2023
The Biggest Cyber Threats For The Financial Industry In 2023By Ben Herzberg, Chief Scientist of Satori According to external market data, the financial sector was the...
The California Consumer Privacy Act (CCPA) and the American Data Privacy Protection Act: The Good, The Bad and The Ugly
The California Consumer Privacy Act (CCPA) and the American Data Privacy Protection Act: The Good, The Bad and The UglyBy Dr. Eric Cole, Advisor – Theon...
“The Impact of Mobile Threats on SMBs: 10 Simple Ways to Empower Your Company.”
“The Impact of Mobile Threats on SMBs: 10 Simple Ways to Empower Your Company.”By Wendy Taccetta, SVP, Small and Medium Business for Verizon Business The shift...
Emotet malware now distributed in Microsoft OneNote files to evade defenses
Emotet malware now distributed in Microsoft OneNote files to evade defensesThe Emotet malware is now distributed using Microsoft OneNote email attachments, aiming to bypass Microsoft security...
Hitachi Energy Latest Victim of Clop GoAnywhere Attacks
Hitachi Energy Latest Victim of Clop GoAnywhere AttacksAttackers Exploit Zero-Day Vulnerability in Fortra's Managed File Transfer SoftwareHitachi Energy joined the ranks of victims hit by the...
Pompompurin Unmasked: Infamous BreachForums Mastermind Arrested in New York
Pompompurin Unmasked: Infamous BreachForums Mastermind Arrested in New YorkU.S. law enforcement authorities have arrested a New York man in connection with running the infamous BreachForums hacking...
Chinese Hackers Exploit Fortinet Zero-Day Flaw for Cyber Espionage Attack
Chinese Hackers Exploit Fortinet Zero-Day Flaw for Cyber Espionage AttackThe zero-day exploitation of a now-patched medium-severity security flaw in the Fortinet FortiOS operating system has been linked to...
Profiling a Currently Active Vendor of Western Union and Banking Logs Including Stolen Credit Cards Transfer Details – An Analysis
Profiling a Currently Active Vendor of Western Union and Banking Logs Including Stolen Credit Cards Transfer Details – An Analysis I’ve recently came across to a...
Profiling a Newly Launched E-Shop For Fake IDs/Documents and Certificates – An Analysis
Profiling a Newly Launched E-Shop For Fake IDs/Documents and Certificates – An Analysis I’ve recently came across to a newly launched E-Shop for fake IDs including...
WebR WASM R Package Load/Library Benchmarking Rabbit Hole
WebR WASM R Package Load/Library Benchmarking Rabbit HoleI have a post coming on using base and {ggplot2} plots in VanillaJS WebR, but after posting some bits...
The Road To ggplot2 In WebR, Part 1: The Road Is Paved With Good Base R Plots
The Road To ggplot2 In WebR, Part 1: The Road Is Paved With Good Base R PlotsI have graphics working in Vanilla JS WebR, now, and...
The Hidden Costs of Insider Threats
The Hidden Costs of Insider ThreatsMuch of cybersecurity policy and practice is dedicated to protecting against external threats and attacks that put networks, data, and devices...
Banking turmoil opens opportunities for fraud – Week in security with Tony Anscombe
Banking turmoil opens opportunities for fraud – Week in security with Tony AnscombeScammers are looking to cash in on the chaos that has set in following...
Feds arrested Pompompurin, the alleged owner of BreachForums
Feds arrested Pompompurin, the alleged owner of BreachForumsU.S. law enforcement arrested this week a US citizen suspected to be Pompompurin, the notorious owner of the BreachForums...
US govt agencies released a joint alert on the Lockbit 3.0 ransomware
US govt agencies released a joint alert on the Lockbit 3.0 ransomwareThe US government released a joint advisory that provides technical details about the operation of...
Windows 11 to ask for permission before pinning applications
Windows 11 to ask for permission before pinning applicationsMicrosoft says it will provide developers with a new API that also asks Windows users for permission when pinning...
Why Healthcare Boards Lag Other Industries in Preparing for Cyberattacks
Why Healthcare Boards Lag Other Industries in Preparing for CyberattacksPost ContentRead MoreProofpoint News Feed
Russia Calling? Scammers Target High-level Western Officials
Russia Calling? Scammers Target High-level Western OfficialsPost ContentRead MoreProofpoint News Feed