CISA kicks off ransomware vulnerability pilot to help spot ransomware-exploitable flawsLast week, the US Cybersecurity and Infrastructure Security Agency (CISA) announced the launch of the Ransomware...
Scam Robocalls Forecast to Cost $58bn This Year
Scam Robocalls Forecast to Cost $58bn This YearJuniper Research says most of the pain will be felt in the USRead MoreJuniper Research says most of the...
“Hinata” Botnet Could Launch Massive DDoS Attacks
"Hinata" Botnet Could Launch Massive DDoS AttacksAkamai warns of new Mirai-like botnet written in GoRead MoreAkamai warns of new Mirai-like botnet written in Go
UK Ransomware Incident Volumes Surge 17% in 2022
UK Ransomware Incident Volumes Surge 17% in 2022Jumpsec report identified Karakurt, Lockbit and Vice Society among groups responsibleRead MoreJumpsec report identified Karakurt, Lockbit and Vice Society...
BreachForums Admin Arrested in New York
BreachForums Admin Arrested in New YorkConor Brian Fitzpatrick of Peekskill was apprehended last Wednesday following an FBI investigationRead MoreConor Brian Fitzpatrick of Peekskill was apprehended last...
KillNet Group Uses DDoS Attacks Against Azure-Based Healthcare Apps
KillNet Group Uses DDoS Attacks Against Azure-Based Healthcare AppsMicrosoft said it saw between 40 and 60 daily attacks in FebruaryRead MoreMicrosoft said it saw between 40...
Mispadu Trojan Steals 90,000+ Banking Credentials From Latin American Victims
Mispadu Trojan Steals 90,000+ Banking Credentials From Latin American VictimsThese included a number of government websites: 105 in Chile, 431 in Mexico and 265 in PeruRead...
Play ransomware gang hit Dutch shipping firm Royal Dirkzwager
Play ransomware gang hit Dutch shipping firm Royal DirkzwagerDutch maritime logistics company Royal Dirkzwager suffered a ransomware attack, the company was hit by the Play ransomware...
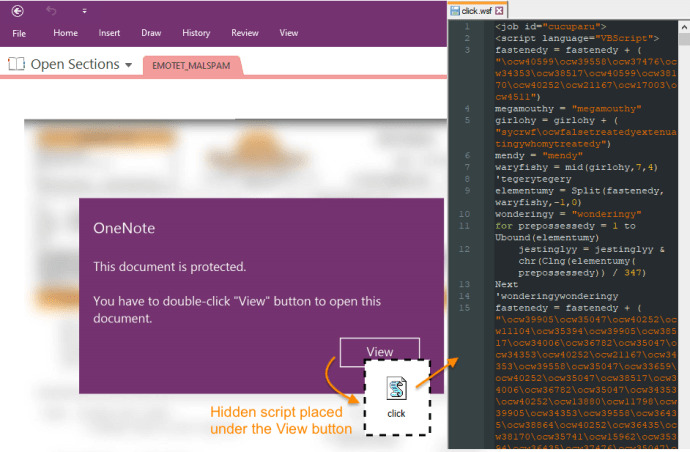
Emotet is back after a three-month hiatus
Emotet is back after a three-month hiatusThe infamous Emotet malware is back after a short hiatus, threat actors are spreading it via Microsoft OneNote email attachments. The...
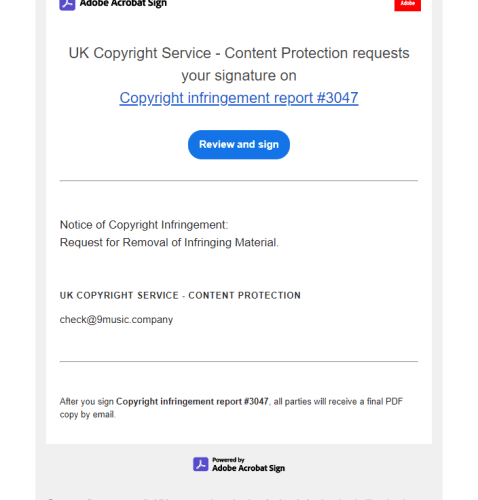
Threat actors abuse Adobe Acrobat Sign to distribute RedLine info-stealer
Threat actors abuse Adobe Acrobat Sign to distribute RedLine info-stealerThreat actors are abusing the legitimate Adobe Acrobat Sign service to distribute the RedLine information stealer. Avast...
HinataBot: The Latest Go-based Threat Is Launching DDoS Attacks
HinataBot: The Latest Go-based Threat Is Launching DDoS AttacksIn January, a Go-based botnet named HinataBot (named after the character from the popular anime series Naruto) was...
Emotet Malware Spreads Out Through Malicious Microsoft OneNote Attachments
Emotet Malware Spreads Out Through Malicious Microsoft OneNote AttachmentsEmotet malware returns after three months break and uses Microsoft OneNote attachments to avoid macro-based security restrictions. Threat...
A Cancer Patient’s Fight for Justice Against a Hospital Ransomware Attack
A Cancer Patient’s Fight for Justice Against a Hospital Ransomware AttackA cancer patient whose naked medical photos and records were stolen by a ransomware gang and...
SOC Prime Threat Bounty — February 2023 Results
SOC Prime Threat Bounty — February 2023 Results Threat Bounty Publications In February 2023, members of the Threat Bounty Program significantly contributed to the SOC Prime...
Why You Should Opt Out of Sharing Data With Your Mobile Provider
Why You Should Opt Out of Sharing Data With Your Mobile ProviderA new breach involving data from nine million AT&T customers is a fresh reminder that...
S4x23 Review Part 3: Healthcare Cybersecurity Sessions
S4x23 Review Part 3: Healthcare Cybersecurity SessionsThis article focuses on the healthcare sector. Over the past two years, the healthcare sector has been in a constant...
First Dero cryptojacking campaign targets unprotected Kubernetes instances
First Dero cryptojacking campaign targets unprotected Kubernetes instancesLearn how this cryptocurrency campaign operates and its scope. Then, get tips on protecting vulnerable Kubernetes instances from this...
Running WordPress on Azure for secure, fast and global content delivery
Running WordPress on Azure for secure, fast and global content deliveryLearn about Microsoft's WordPress on Azure App Service, as well as an interesting alternative from WP...
Google Pixel flaw allowed recovery of redacted, cropped images
Google Pixel flaw allowed recovery of redacted, cropped imagesAn 'Acropalypse' flaw in Google Pixel's Markup tool made it possible to partially recover edited or redacted screenshots...
Hackers mostly targeted Microsoft, Google, Apple zero-days in 2022
Hackers mostly targeted Microsoft, Google, Apple zero-days in 2022Hackers continue to target zero-day vulnerabilities in malicious campaigns, with researchers reporting that 55 zero-days were actively exploited...
Is your organization among the 1 in 10 with malware traffic? DNS data reveals scary truth
Is your organization among the 1 in 10 with malware traffic? DNS data reveals scary truthEXECUTIVE SUMMARY: In a new report, cyber security researchers have highlighted...
GUEST ESSAY: Scammers leverage social media, clever con games to carry out digital exploitation
GUEST ESSAY: Scammers leverage social media, clever con games to carry out digital exploitationOne common misconception is that scammers usually possess a strong command of computer...
How an AI voice clone fooled Centrelink – video
How an AI voice clone fooled Centrelink – videoAn investigation by Guardian Australia has found that AI technology is able to fool a voice identification system...
Is Your Identity Management Comprehensive Enough? Are You Just Tipping Your Toes?
Is Your Identity Management Comprehensive Enough? Are You Just Tipping Your Toes?Post ContentRead MoreDataBreachToday.com RSS Syndication
Impact of Technology Deployments on Privacy: Striking the Right Balance
Impact of Technology Deployments on Privacy: Striking the Right BalancePost ContentRead MoreDataBreachToday.com RSS Syndication
Future of Cybersecurity: Threats and Opportunities
Future of Cybersecurity: Threats and OpportunitiesPost ContentRead MoreDataBreachToday.com RSS Syndication
It’s Raining Zero-Days in Cyberspace
It's Raining Zero-Days in CyberspaceChinese Hackers and Others Increasingly Favor Unpatched VulnerabilitiesLast year was another bonanza in zero-days for Chinese state hackers, say security researchers in...
Roseville, Calif., CIO Brings Global Background to Local Gov
Roseville, Calif., CIO Brings Global Background to Local GovHong Sae is the CIO for the city of Roseville, Calif., and he has a tremendous track record...
Lowe’s Market chain leaves client data up for grabs
Lowe’s Market chain leaves client data up for grabsA misconfiguration on a website owned by the US-based Lowe’s Market grocery store chain could have allowed threat...
Security Affairs newsletter Round 411 by Pierluigi Paganini
Security Affairs newsletter Round 411 by Pierluigi PaganiniA new round of the weekly SecurityAffairs newsletter arrived! Every week the best security articles from Security Affairs are...