Source: heimdalsecurity.com – Author: Mihaela Marian
Across Southeast Asia, Europe and Africa, a new Linux variant of the PingPull malware used by Chinese APT group Alloy Taurus (Gallium) has been reported as an active threat to telecommunications, finance and government organizations.
Alloy Taurus is a Chinese nation-state-affiliated threat actor that focuses on cyberespionage and is best known for targeting major telecommunications companies. The advanced persistent threat (APT) has been around since at least 2012, but it has only been in the spotlight since 2019.
Alloy Taurus Returns
The group was quite active in 2021 and early 2022, using the PingPull Windows RAT in multiple campaigns targeting telecoms, as well as military and government organizations in Afghanistan, Australia, Belgium, Cambodia, Malaysia, Mozambique, the Philippines, Russia, and Vietnam. However, the APT seemingly went off the grid, only to reappear with this newly discovered PingPull malware variant aimed at Linux.
While Palo Alto Networks’ Unit 42 was tracking the infrastructure used by the APT group, they also identified its use of a second backdoor they named Sword2033.
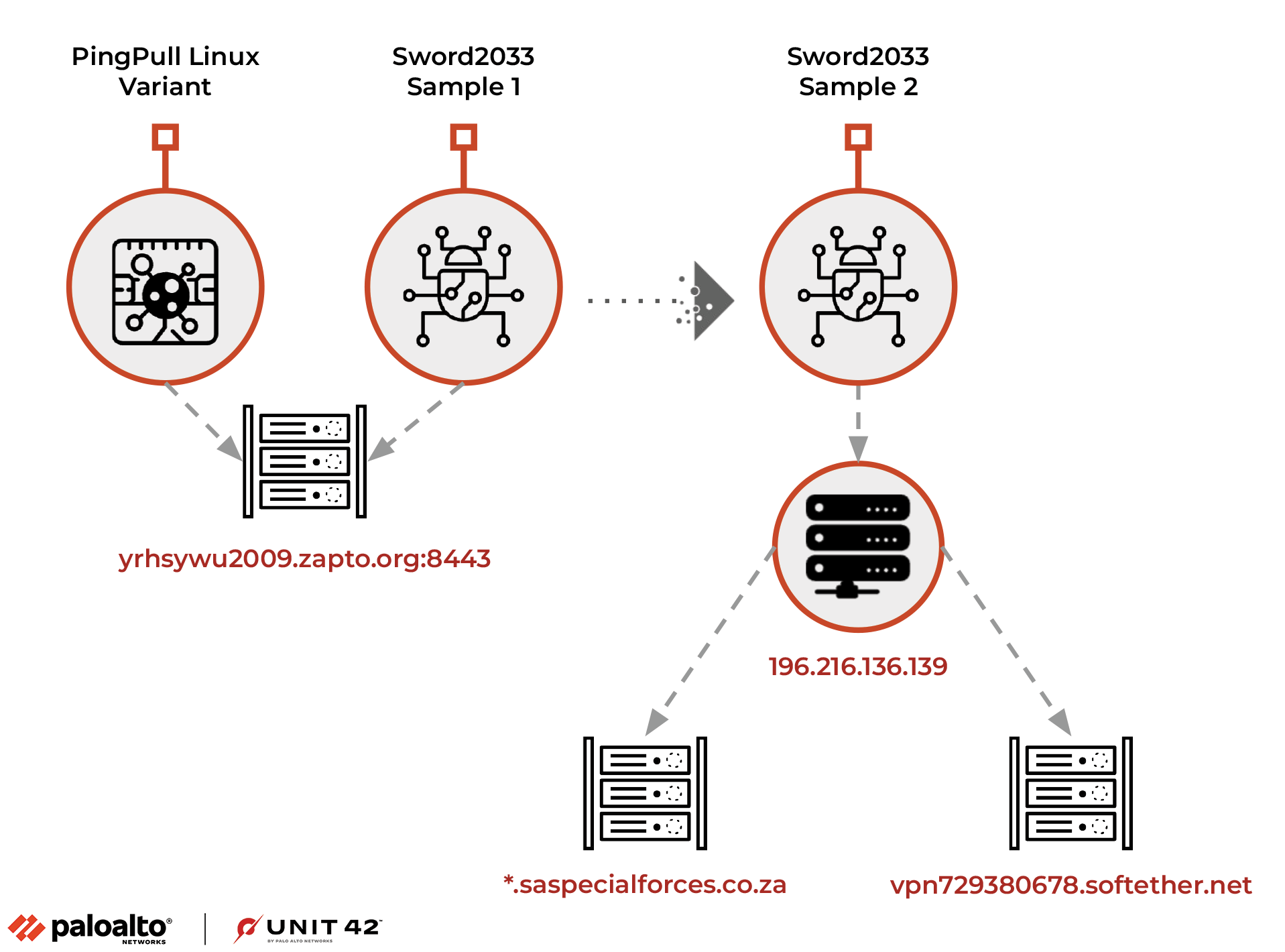
As per the researchers` report, Linux variants allow attackers to list, read, write, copy, rename, delete, and rename files, as well as run commands, thus overlapping with the Windows variant.
They burned the Windows version of PingPull, and they’ve spun up a new capability that demonstrates some degree of expertise switching to a different variant.
Furthermore, as of April 26 three out of 62 vendors identified the sample of the PingPull Linux variant as malicious. According to the researchers, they made this determination by examining HTTP communication structure, POST parameters, AES keys, and C2 commands. Additionally, Sword2033 was observed operating as a backdoor, allowing users to upload or download files (#up and #dn) respectively, and also execute commands via “exc/c:”.
A Piece of Advice from Heimdal®
In order to defend against such threats, organizations should definitely employ capabilities such as DNS security. The first step towards a secure DNS is DNS filtering. Heimdal Threat Prevention employs a powerful DNS filtering engine, more than capable of intercepting malicious data packets that could harm your endpoints and network. Additionally, our Threat Prevention solution picks up any unusual activity during querying, it will automatically block the connection. You can read more about DNS security for businesses in our DNS Security article.
If you liked this article, follow us on LinkedIn, Twitter, Facebook, and YouTube for more cybersecurity news and topics.
If you liked this post, you will enjoy our newsletter.
Get cybersecurity updates you’ll actually want to read directly in your inbox.
Original Post URL: https://heimdalsecurity.com/blog/chinese-apt-alloy-taurus-is-back-linux-variant-pingpull-malware-active/
Category & Tags: Cybersecurity News – Cybersecurity News




















































