Source: www.bleepingcomputer.com – Author: Ax Sharma

A blockchain developer shares his ordeal over the holidays when he was approached on LinkedIn by a “recruiter” for a web development job.
The recruiter in question asked the developer to download npm packages from a GitHub repository, and hours later the developer discovered his MetaMask wallet had been emptied.
Take-home job exercise empties dev’s crypto wallet
Antalya-based Murat Çeliktepe, a blockchain and web developer, shared this week how he was approached by a “recruiter” on LinkedIn with an Upwork job posting that looked legitimate.
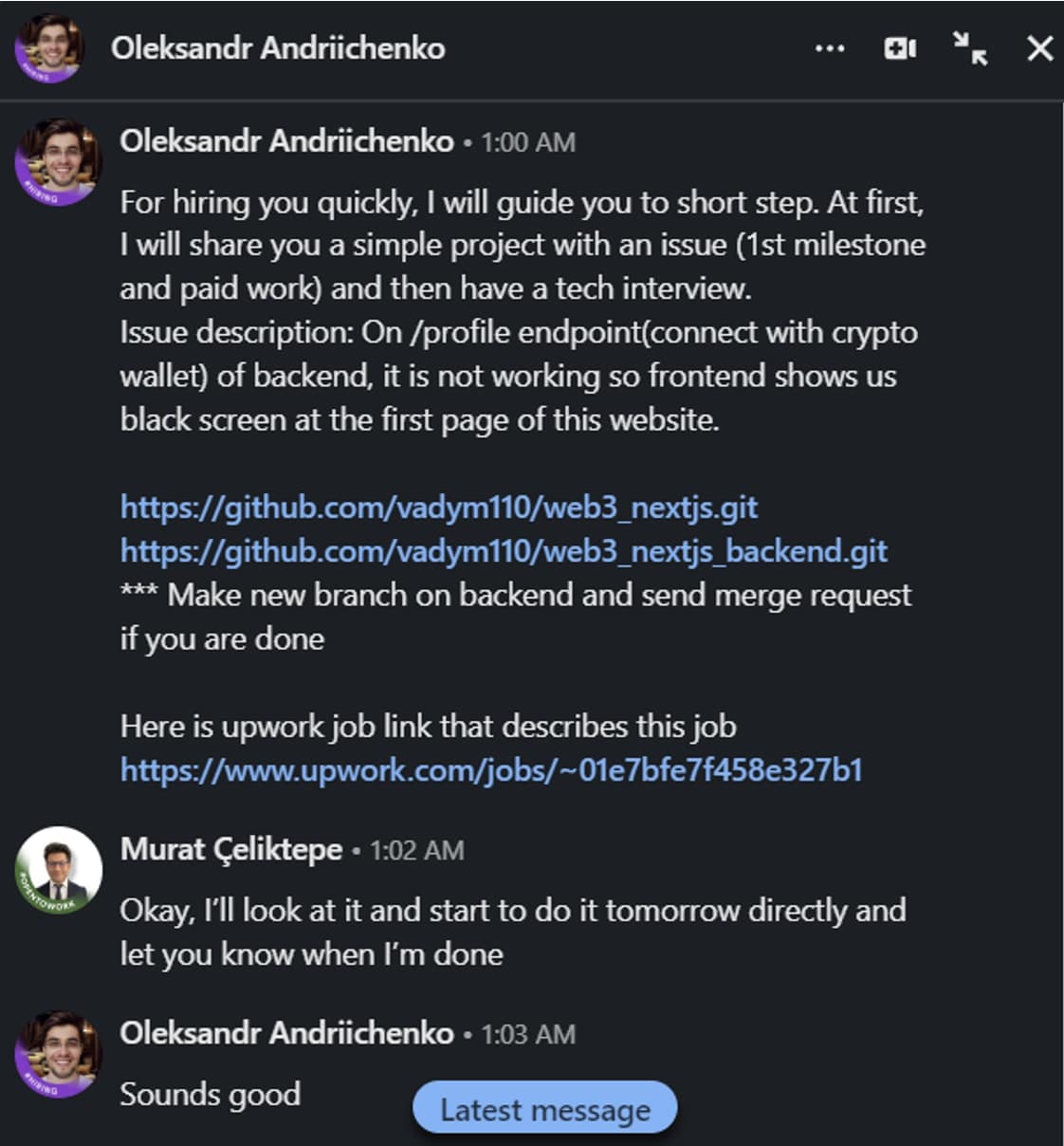
As a part of the job interview, the recruiter asked Çeliktepe to download and debug the code in two npm packages—”web3_nextjs” and “web3_nextjs_backend” hosted on a GitHub repository. However, moments later, the developer discovered that his MetaMask wallet had been drained—with upwards of $500 siphoned out of his account, based on the information seen by BleepingComputer.
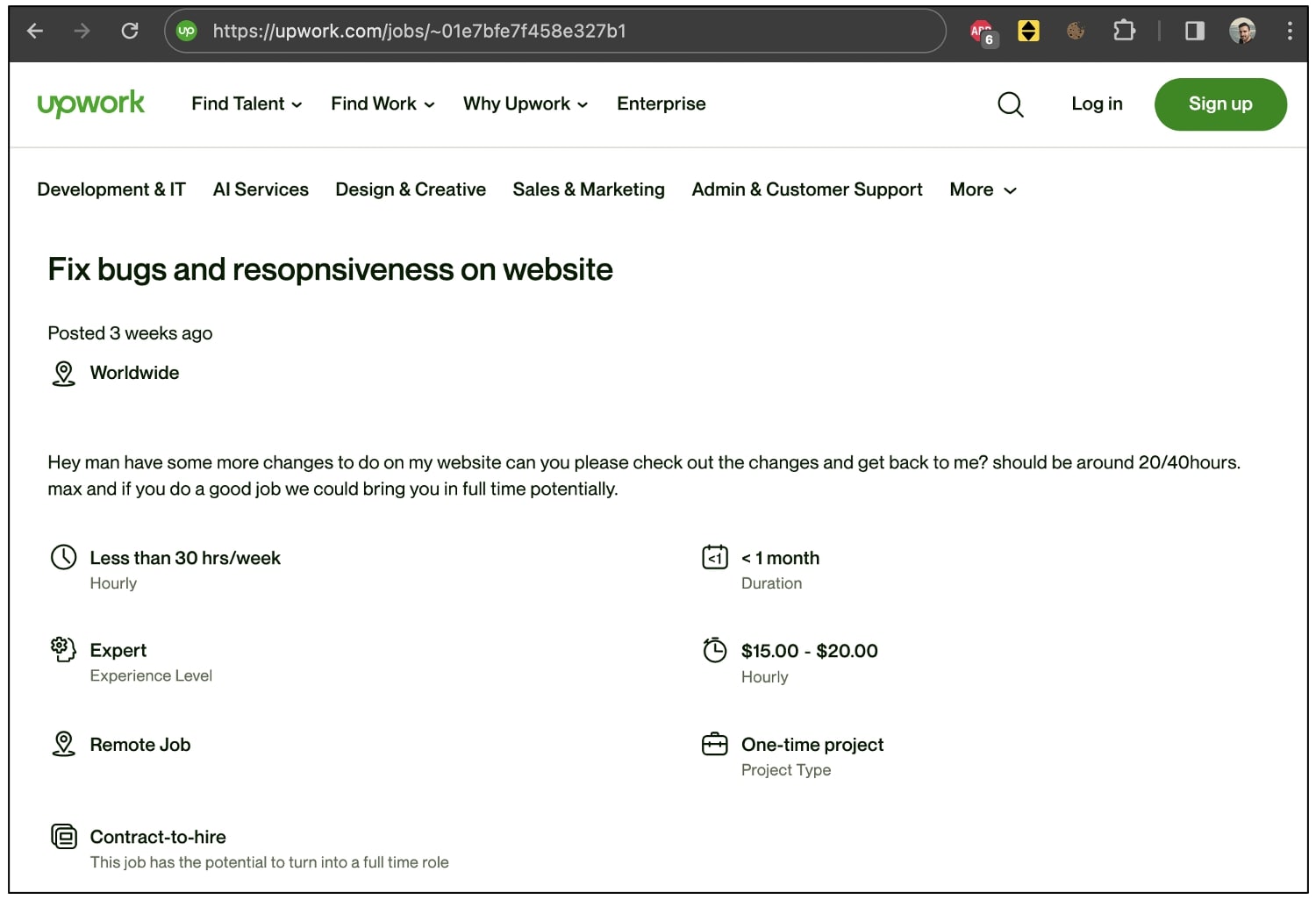
The Upwork job posting asks the applicant to “fix bugs and resopnsiveness [sic] on website” and claims to pay between $15 and $20 hourly for a task expected to take under a month.
Çeliktepe, whose LinkedIn profile picture bears the “#OpenToWork” tag, decided to give this challenge a go and downloaded the GitHub repositories shared by the recruiter, as a part of the “tech interview.”
It isn’t unusual for legitimate tech interviews to involve some kind of take-home exercise or proof-of-concept (PoC) assignment involving code writing or debugging, which makes the lure highly convincing even for technically savvy people, like developers.
(BleepingComputer)
Note that the apps present in the said GitHub repos [1, 2] are valid npm projects, given their format and the included package.json manifest, but these do not appear to have ever been published to npmjs.com, the largest open-source registry of JavaScript projects.
“My MetaMask wallet was completely emptied… under the pretext of the interview process and job assignment, my entire wallet was completely emptied in a way that I don’t yet understand exactly how,” wrote Çeliktepe in Turkish on social media.
“I will share the codes below, I would be very happy if someone could help me understand how.”
As per the assignment instructions, the developer cloned both GitHub repositories and started to debug his instance to find the problem while running both the frontend and backend applications locally on his machine.
Following the task, he attended a Google Meet session with the man who had approached him on LinkedIn, and explained the solution—and this was it, or so the developer thought. Except, a few hours later, the developer noticed, his Ethereum balance had been drained.
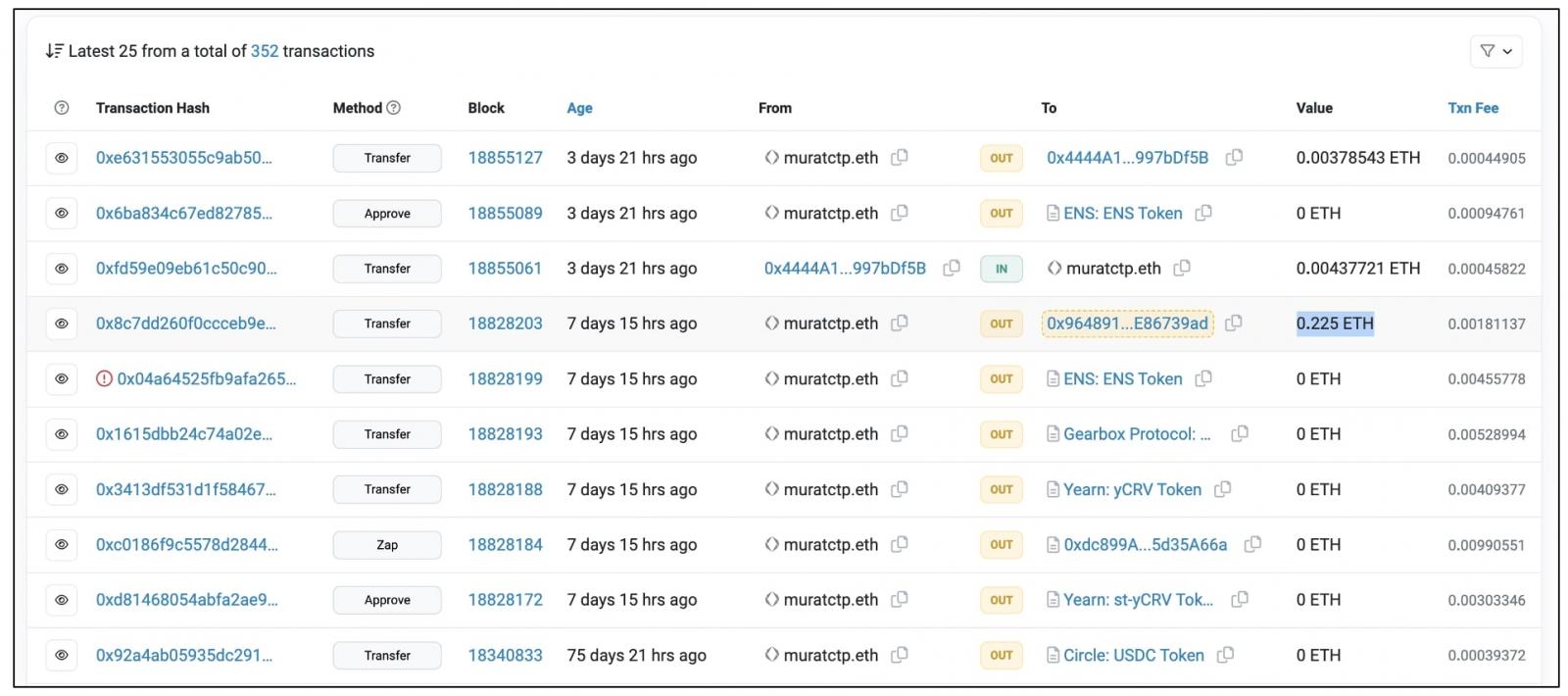
Among recent transactions shared by the developer and seen by BleepingComputer, is an outbound one for 0.225 ETH—approximately US$538 sent to another crypto address in the last week.
More devs targeted in same scam
Despite looking through the code present in both repositories, the developer is still unsure about the exact mechanics of this attack that led him to lose money and is seeking help from the community to understand the same.
His appeal was quickly followed up by, what appeared to be opportunistic crypto bots and scam accounts, enticing him to get in touch with bogus “MetaMask support” Gmail addresses and Google forms.
Some legitimately concerned community members stepped up, however, to offer their insights.
An Istanbul-based bug bounty hunter hypothesized that the npm projects ran by the developer effectively paved the means for the attacker to deploy a reverse shell, by opening up port 5000 on his machine that began “listening” for connections.
BleepingComputer did confirm the presence of the described code within the backend app [1, 2] “web3_nextjs_backend,” but we have not been able to independently confirm if attackers indeed gained access to the developer’s machine via this attack vector.
Furthermore, Çeliktepe says he never kept the secret “12 words” or what’s formally known as MetaMask’s Secret Recovery Phrase (SRP) on his computer and therefore does not understand how his MetaMask wallet was breached, even if attackers would have gained access to his machine.
BleepingComputer further observed the presence of a “master public key” or an extended public key in the package which appears to help generate Bitcoin addresses.
There are also network requests with data being made to flickthebean.onrender[.]com by several files within web3_nextjs. But once again, whether these are all part of a simple quasi-job interview exercise, or the crypto-stealing attack remains unclear.
Other theories proposed by the community members involve, rather than the developer’s machine getting infected with malware, the illicit npm project copied his passwords from a web browser that had auto-fill enabled, or that his network traffic was intercepted by the code he voluntarily ran during the “tech interview.”
Whatever the attack vector may be, Çeliktepe is not the only one who has been targeted in this fashion, and that too by the same “recruiter.”
Another blockchain dev and security researcher Bartu Bozkurt says he had also been approached for the “job” on LinkedIn, just days prior, and calls this a “very well-known type of hack.”
Yet another developer, Mehmet Selim, also confirms being messaged by the same recruiter who had reached out to Çeliktepe.
As such, web developers and security researchers should keep an eye out for bogus job offers on career development platforms as these could be scams. It is a good idea to complete any take-home job exercises—no matter how seemingly benign, on a (virtual) machine that is separate from your primary device.
h/t @KutluSoz for the tip-off.
Original Post URL: https://www.bleepingcomputer.com/news/security/blockchain-devs-wallet-emptied-in-job-interview-using-npm-package/
Category & Tags: Security – Security




















































