Source: www.securityweek.com – Author: Kevin Townsend Two new products aim to secure the traditional OSS supply chain, and the new AI model software supply chain. The...
Author:
CISO Conversations: The Legal Sector With Alyssa Miller at Epiq and Mark Walmsley at Freshfields – Source: www.securityweek.com
Source: www.securityweek.com – Author: Kevin Townsend SecurityWeek talks to legal sector CISOs Alyssa Miller at Epiq and Mark Walmsley at Freshfields Bruckhaus Deringer The post CISO...
Cybercrime’s Silent Operator: The Unraveling of VexTrio’s Malicious Network Empire – Source: www.securityweek.com
Source: www.securityweek.com – Author: Kevin Townsend VexTrio is a traffic direction system (TDS) with more than 60 affiliates feeding an unknown number of malicious campaigns. The...
Vulnerability Management Firm Vicarius Raises $30 Million – Source: www.securityweek.com
Source: www.securityweek.com – Author: Kevin Townsend New York based vulnerability management firm Vicarius has raised $30 million in a Series B funding round led by Bright...
Hacker Conversations: HD Moore and the Line Between Black and White – Source: www.securityweek.com
Source: www.securityweek.com – Author: Kevin Townsend SecurityWeek talked to HD Moore, best known as the founder and original developer of Metasploit. The post Hacker Conversations: HD...
CISO Conversations: Jason Rebholz and Jason Ozin From the Insurance Sector – Source: www.securityweek.com
Source: www.securityweek.com – Author: Kevin Townsend SecurityWeek interviews two CISOs from the insurance sector: Jason Rebholz at Corvus Insurance and Jason Ozin at UK-based PIB Group....
Merck Settles NotPetya Insurance Claim, Leaving Cyberwar Definition Unresolved – Source: www.securityweek.com
Source: www.securityweek.com – Author: Kevin Townsend In a landmark case that blurs the lines between cyber and kinetic warfare, Merck reached a settlement with insurers over...
Hacker Conversations: Runa Sandvik – Source: www.securityweek.com
Source: www.securityweek.com – Author: Kevin Townsend SecurityWeek interviews Runa Sandvik, a cybersecurity researcher focused on protecting journalists, defenders of human rights and lawyers, The post Hacker...
ZDI Discusses First Automotive Pwn2Own – Source: www.securityweek.com
Source: www.securityweek.com – Author: Kevin Townsend The Zero Day Initiative (ZDI) will host a new Automotive Pwn2Own at the Automotive World Conference in Tokyo, January 24...
Sysdig Launches Realtime Attack Graph for Cloud Environments – Source: www.securityweek.com
Source: www.securityweek.com – Author: Kevin Townsend Cloud security firm Sysdig has enhanced the cloud detection and response capabilities of its CNAPP offering with a realtime cloud...
The CISO Carousel and its Effect on Enterprise Cybersecurity – Source: www.securityweek.com
Source: www.securityweek.com – Author: Kevin Townsend The average tenure of a Chief Information Security Officer said to sit between 18 to 24 months. This is barely...
Venafi Leverages Generative AI to Manage Machine Identities – Source: www.securityweek.com
Source: www.securityweek.com – Author: Kevin Townsend Machine identity firm Venafi has launched a proprietary generative AI (gen-AI) model to help with the mammoth, complex, and expanding...
Hacker Conversations: Casey Ellis, Hacker and Ringmaster at Bugcrowd – Source: www.securityweek.com
Source: www.securityweek.com – Author: Kevin Townsend In this edition of Hacker Conversations, SecurityWeek talks to Casey Ellis, founder, chairman and CTO at Bugcrowd – and hacker....
OT/IoT and OpenTitan, an Open Source Silicon Root of Trust – Source: www.securityweek.com
Source: www.securityweek.com – Author: Kevin Townsend OpenTitan is a project aimed at bringing the success of open source software to the silicon design space – specifically...
CISOs and Board Reporting – an Ongoing Problem – Source: www.securityweek.com
Source: www.securityweek.com – Author: Kevin Townsend For CISOs to gain the support of the board, they must first translate and report highly technical cybersecurity concerns and...
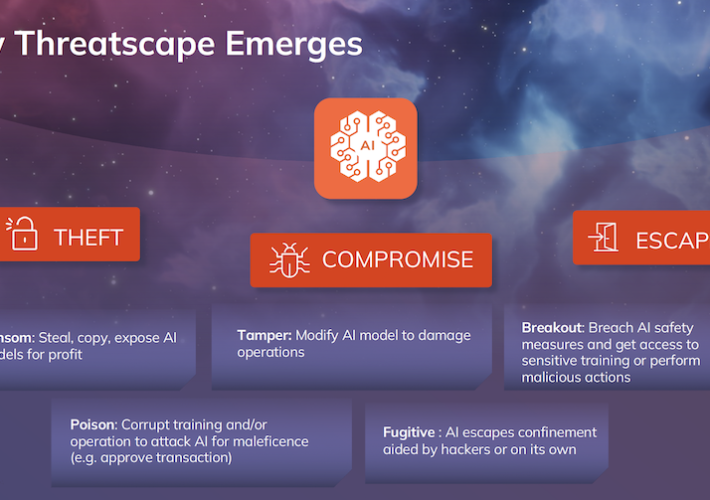
Vector Embeddings – Antidote to Psychotic LLMs and a Cure for Alert Fatigue? – Source: www.securityweek.com
Source: www.securityweek.com – Author: Kevin Townsend Vector embeddings – data stored in a vector database – can be used to minimize hallucinations from a GPT-style large...
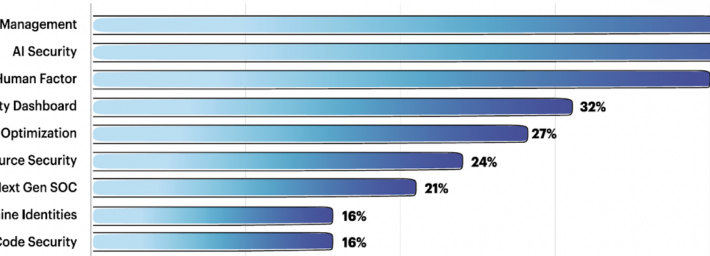
The Team8 Foundry Method for Selecting Investable Startups – Source: www.securityweek.com
Source: www.securityweek.com – Author: Kevin Townsend Team8 regularly consults with its CISO Village of around 350 enterprise CISOs over startup investments. AI security, 3rd party risk...
Hacker Conversations: Alex Ionescu – Source: www.securityweek.com
Source: www.securityweek.com – Author: Kevin Townsend In this edition of Hacker Conversations, SecurityWeek talks to Alex Ionescu, a world-renowned cybersecurity expert who has combined a career...
The Reality of Cyberinsurance in 2023 – Source: www.securityweek.com
Source: www.securityweek.com – Author: Kevin Townsend The cyberinsurance industry is maturing. In its early days, it simply accepted cyber risk with few questions asked. It lost...
Smart Cities: Utopian Dream, Security Nightmare, or Political Gimmick? – Source: www.securityweek.com
Source: www.securityweek.com – Author: Kevin Townsend How much smart does a smart city need to be called smart? It’s not a trivial question. It goes to...
Hacker Conversations: Cris Thomas (AKA Space Rogue) From Lopht Heavy Industries – Source: www.securityweek.com
Source: www.securityweek.com – Author: Kevin Townsend Researchers are hackers. In the hat color terminology, there are Blackhat, Whitehat and various shades of Greyhat hackers. Today, the...
Rapid7 Says ROI for Ransomware Remains High; Zero-Day Usage Expands – Source: www.securityweek.com
Source: www.securityweek.com – Author: Kevin Townsend The Rapid7 mid-year review of the threat landscape is not reassuring. Ransomware remains high, basic security defenses are not being...
CISO Conversations: CISOs in Cloud-based Services Discuss the Process of Leadership – Source: www.securityweek.com
Source: www.securityweek.com – Author: Kevin Townsend In this edition of CISO Conversations, SecurityWeek talks to Billy Spears, CISO at Teradata (a multi-cloud analytics provider), and Lea...
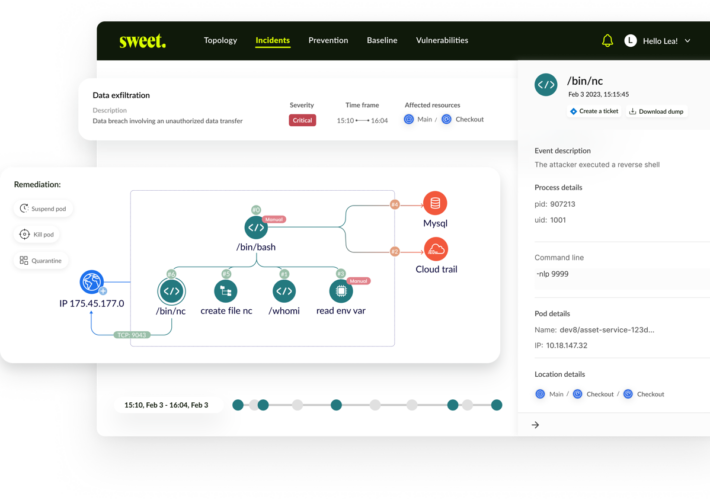
Sweet Security Emerges From Stealth With $12 Million Seed Funding and a Cloud Runtime Solution – Source: www.securityweek.com
Source: www.securityweek.com – Author: Kevin Townsend Israeli startup Sweet Security has emerged from stealth, launched a Cloud Runtime Security Suite, and announced a $12 million seed...
UK Think Tank Proposes Greater Ransomware Reporting From Cyberinsurance to Government – Source: www.securityweek.com
Source: www.securityweek.com – Author: Kevin Townsend The Royal United Services Institute (RUSI) is an independent UK think tank that has been in existence since 1831. It...
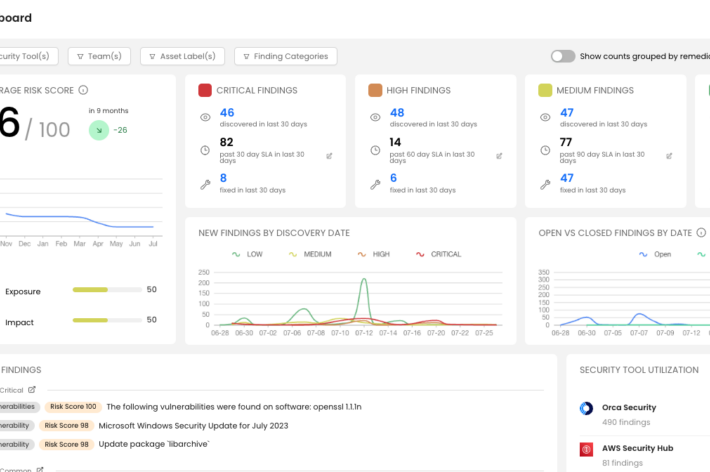
These Are the Top Five Cloud Security Risks, Qualys Says – Source: www.securityweek.com
Source: www.securityweek.com – Author: Kevin Townsend Cloud security specialist Qualys has provided its view of the top five cloud security risks, drawing insights and data from...
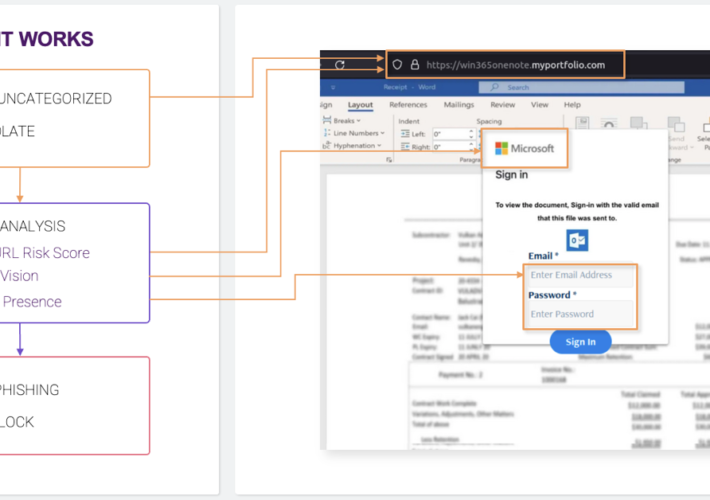
Shield and Visibility Solutions Target Phishing From Inside the Browser – Source: www.securityweek.com
Source: www.securityweek.com – Author: Kevin Townsend Menlo Security has introduced two anti-phishing solutions that tackle the problem from within the browser; that is, by analyzing what...
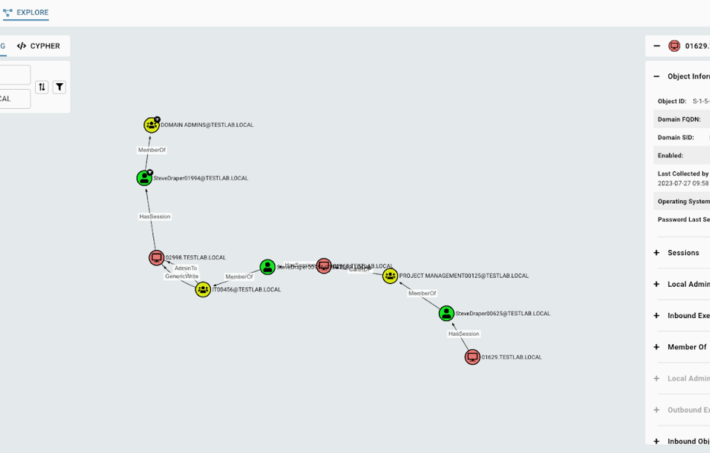
SpecterOps Updates BloodHound Active Directory Mapping Tool – Source: www.securityweek.com
Source: www.securityweek.com – Author: Kevin Townsend BloodHound is SpecterOps’ graph-based map of Active Directory relationships used by external pentesters (and malicious attackers), and internal users to...
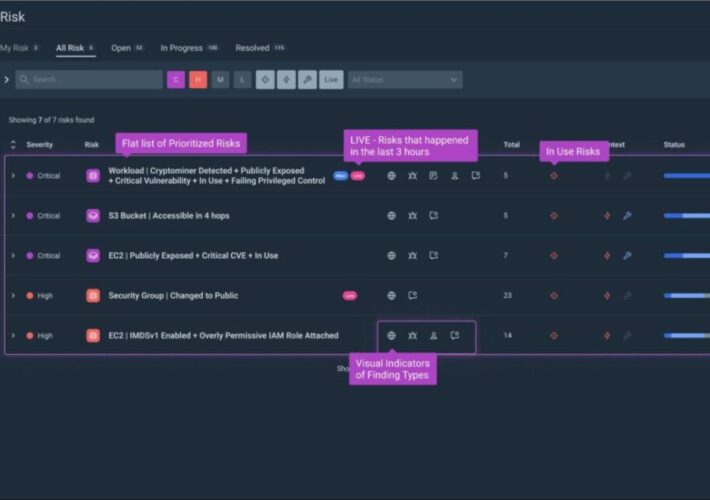
Silk Security Emerges from Stealth With $12.5 Million Seed Funding – Source: www.securityweek.com
Source: www.securityweek.com – Author: Kevin Townsend New York based Silk Security has raised $12.5 million in a seed funding round led by Insight Partners and Hetz...
Hacker Conversations: Youssef Sammouda, Bug Bounty Hunter – Source: www.securityweek.com
Source: www.securityweek.com – Author: Kevin Townsend Youssef Sammouda is a Tunisian security researcher who focuses on bug bounty programs. He describes himself as, “Vulnerability researcher with...