Source: thehackernews.com – Author: . Feb 14, 2024NewsroomArtificial Intelligence / Cyber Attack Nation-state actors associated with Russia, North Korea, Iran, and China are experimenting with artificial...
Author: CISO2CISO Editor 2
Adobe Patch Tuesday fixed critical vulnerabilities in Magento, Acrobat and Reader – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Adobe Patch Tuesday fixed critical vulnerabilities in Magento, Acrobat and Reader Pierluigi Paganini February 14, 2024 Adobe Patch Tuesday security...
Prudential Financial breached in data theft cyberattack – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Sergiu Gatlan Prudential Financial has disclosed that its network was breached last week, with the attackers stealing employee and contractor data before being blocked...
Declining Ransomware Payments: Shift in Hacker Tactics? – Source: securityboulevard.com
Source: securityboulevard.com – Author: Team Nuspire Several cybersecurity advisories and agencies recommend not caving into ransomware gangs’ demands and paying their ransoms. For a while, though,...
Improving Software Quality with the OWASP BOM Maturity Model – Source: securityboulevard.com
Source: securityboulevard.com – Author: Deb Radcliff By Deb Radcliff, industry analyst and editor of CodeSecure’s TalkSecure educational blogs and podcasts (syndicated at Security Boulevard, YouTube, and...
Qmulos Launches Q-Compliance Core for Businesses in Need of a Modern Compliance Approach – Source: securityboulevard.com
Source: securityboulevard.com – Author: Alison Underdown As cyber threats grow alongside penalties for negligence, risk and compliance management has become a higher priority function across organizations,...
USENIX Security ’23 – Chenghong Wang, David Pujol, Kartik Nayak, Ashwin Machanavajjhal – Private Proof-of-Stake Blockchains using Differentially-Private Stake Distortion – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman Security Bloggers Network Home » Security Bloggers Network » USENIX Security ’23 – Chenghong Wang, David Pujol, Kartik Nayak, Ashwin...
Exploiting Kubernetes through Operator Injection – Source: securityboulevard.com
Source: securityboulevard.com – Author: Thomas Tan Intro The Kubernetes documentation describes operators as “software extensions to Kubernetes that use custom resources to manage applications and their components.” These...
News alert: Kiteworks named as a founding member of NIST’s new AI safety consortium – ‘AISIC’ – Source: securityboulevard.com
Source: securityboulevard.com – Author: bacohido San Mateo, Calif., Feb. 13, 2023 – The U.S. White House announced groundbreaking collaboration between OpenPolicy and leading innovation companies, including...
‘Incompetent’ FCC Fiddles With Data Breach Rules – Source: securityboulevard.com
Source: securityboulevard.com – Author: Richi Jennings While Rome burns, Federal Communications Commission is once again behind the curve. The FCC is telling telcos to tell them about data...
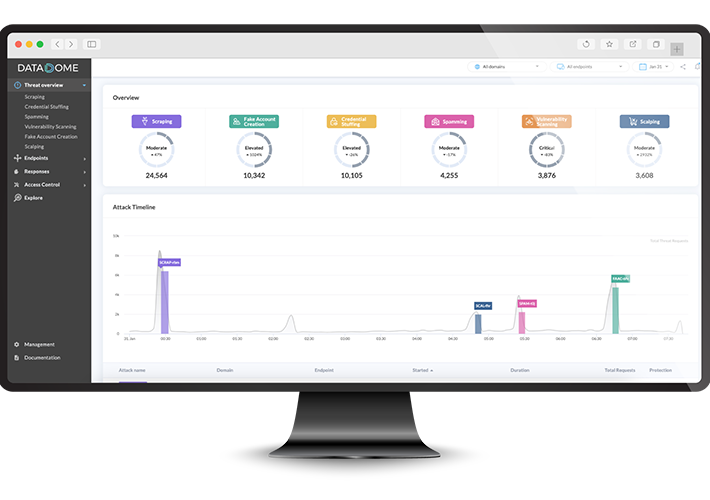
Guide to Advanced Fraud Monitoring & Proactive Detection in 2024 – Source: securityboulevard.com
Source: securityboulevard.com – Author: DataDome If you sell anything online or store any sensitive information digitally, you’re at risk of fraud. Online payment fraud losses doubled...
Comic Agilé – Mikkel Noe-Nygaard, Luxshan Ratnaravi – #278 – The Non-Senior Consultant – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman Wednesday, February 14, 2024 Security Boulevard The Home of the Security Bloggers Network Community Chats Webinars Library Home Cybersecurity News...
Reshaping Trust and Security for the Realities of 2024 – Source: securityboulevard.com
Source: securityboulevard.com – Author: Jenn Markey The new year is always a time for reflection, and after a year shaped by AI, biometrics, and nation-state attacks...
Europe’s AI Act Poised To Become Law After Committees Vote – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Artificial Intelligence & Machine Learning , Legislation & Litigation , Next-Generation Technologies & Secure Development ACt Will Require Developers to Allows...
Responsible Use of Artificial Intelligence – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Artificial Intelligence & Machine Learning , Governance & Risk Management , Next-Generation Technologies & Secure Development A Practical Guide for Cybersecurity...
Generative AI and the Brave New World of Work – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Artificial Intelligence & Machine Learning , Next-Generation Technologies & Secure Development , Professional Certifications & Continuous Training CyberEd.io’s Steve King on...
USPTO: AI Can Assist Inventors But Can’t Hold Patents – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Artificial Intelligence & Machine Learning , Next-Generation Technologies & Secure Development Humans Must Show Significant Role in AI-Assisted Cases for Inventor...
More Signs of a Qakbot Resurgence – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Cybercrime , Endpoint Detection & Response (EDR) , Fraud Management & Cybercrime Qakbot Wouldn’t Be the First Trojan to Come Back...
They’re Back? HHS OCR Is Eyeing the Return of HIPAA Audits – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Healthcare , Industry Specific , Standards, Regulations & Compliance The Agency Is Surveying Previous Auditees to Reassess the Dormant Program Marianne...
A Hacker’s Mind is Out in Paperback – Source: www.schneier.com
Source: www.schneier.com – Author: Bruce Schneier HomeBlog A Hacker’s Mind is Out in Paperback The paperback version of A Hacker’s Mind has just been published. It’s...
Molly White Reviews Blockchain Book – Source: www.schneier.com
Source: www.schneier.com – Author: Bruce Schneier Molly White—of “Web3 is Going Just Great” fame—reviews Chris Dixon’s blockchain solutions book: Read Write Own: In fact, throughout the...
On Passkey Usability – Source: www.schneier.com
Source: www.schneier.com – Author: Bruce Schneier HomeBlog Comments Matt • February 12, 2024 12:39 PM Nice article, but no mention of account recovery in case you...
Friday Squid Blogging: A Penguin Named “Squid” – Source: www.schneier.com
Source: www.schneier.com – Author: Bruce Schneier HomeBlog Comments Anonymous • February 9, 2024 8:39 PM “Philadelphia sheriff caught posting over 30 fake news stories generated by...
No, Toothbrushes Were Not Used in a Massive DDoS Attack – Source: www.schneier.com
Source: www.schneier.com – Author: Bruce Schneier HomeBlog No, Toothbrushes Were Not Used in a Massive DDoS Attack The widely reported story last week that 1.5 million...
On Software Liabilities – Source: www.schneier.com
Source: www.schneier.com – Author: Bruce Schneier On Software Liabilities Over on Lawfare, Jim Dempsey published a really interesting proposal for software liability: “Standard for Software Liability:...
NIST Establishes AI Safety Consortium – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: Megan Crouse Image: Adobe/Grandbrothers The National Institute of Standards and Technology established the AI Safety Institute on Feb. 7 to determine guidelines...
Google Cloud’s Nick Godfrey Talks Security, Budget and AI for CISOs – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: Megan Crouse As senior director and global head of the office of the chief information security officer (CISO) at Google Cloud, Nick...
Atlas VPN Free vs. Premium: Which Plan Is Best For You? – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: Franklin Okeke We may earn from vendors via affiliate links or sponsorships. This might affect product placement on our site, but not...
20+ hospitals in Romania hit hard by ransomware attack on IT service provider – Source: grahamcluley.com
Source: grahamcluley.com – Author: Graham Cluley Over 20 hospitals in Bucharest have reportedly been impacted by a ransomware attack after cybercriminals targeted an IT service provider....
“Smart” helmet flaw exposes location tracking and privacy risks – Source: www.bitdefender.com
Source: www.bitdefender.com – Author: Graham Cluley A smart helmet for biking and skiing fans sounds like a good idea. If you’re on the slopes or trails,...