Source: www.infosecurity-magazine.com – Author: 1 Google’s Threat Analyst Group has confirmed that Iran-backed hackers have used their cyber capabilities to undercut public support for the Israel-Hamas conflict...
Author: CISO2CISO Editor 2
Cybersecurity Spending Expected to be Slashed in 41% of SMEs – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 Cybersecurity spending is predicted to be cut by 41% of SMEs over the coming year amid the challenging economic environment, according...
Microsoft Fixes Two Zero-Days in February Patch Tuesday – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 Microsoft has landed system administrators with a busy February after releasing updates for 73 vulnerabilities, including two zero-day flaws currently under...
Romantic AI Chatbots Fail the Security and Privacy Test – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 Experts have warned users of AI-powered “relationship” chatbots that their data and privacy are at risk, after failing all 11 apps...
Southern Water Notifies Customers and Employees of Data Breach – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 Southern Water has confirmed that personal data of both customers and employees has been accessed in a recent ransomware attack. The...
Bank of America Customers at Risk After Data Breach – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 Bank of America has alerted its customers about a recent data breach that occurred through one of its service providers, Infosys...
CISA adds Microsoft Windows bugs to its Known Exploited Vulnerabilities catalog – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini CISA adds Microsoft Windows bugs to its Known Exploited Vulnerabilities catalog Pierluigi Paganini February 15, 2024 U.S. Cybersecurity and Infrastructure...
Nation-state actors are using AI services and LLMs for cyberattacks – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Nation-state actors are using AI services and LLMs for cyberattacks Pierluigi Paganini February 15, 2024 Microsoft and OpenAI warn that...
Abusing the Ubuntu ‘command-not-found’ utility to install malicious packages – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Abusing the Ubuntu ‘command-not-found’ utility to install malicious packages Pierluigi Paganini February 14, 2024 Researchers reported that attackers can exploit...
Zoom fixed critical flaw CVE-2024-24691 in Windows software – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Zoom fixed critical flaw CVE-2024-24691 in Windows software Pierluigi Paganini February 14, 2024 Zoom addressed seven vulnerabilities in its desktop...
Microsoft Patch Tuesday for February 2024 fixed 2 actively exploited 0-days – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Microsoft Patch Tuesday for February 2024 fixed 2 actively exploited 0-days Pierluigi Paganini February 14, 2024 Microsoft Patch Tuesday security...
A ransomware attack took 100 Romanian hospitals down – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini A ransomware attack took 100 Romanian hospitals down Pierluigi Paganini February 13, 2024 Authorities in Romania reported that at least...
Bank of America customer data compromised after a third-party services provider data breach – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Bank of America customer data compromised after a third-party services provider data breach Pierluigi Paganini February 13, 2024 Bank of...
How Nation-State Actors Target Your Business: New Research Exposes Major SaaS Vulnerabilities – Source:thehackernews.com
Source: thehackernews.com – Author: . Feb 15, 2024The Hacker NewsSaaS Security / Risk Management With many of the highly publicized 2023 cyber attacks revolving around one...
Chinese Hackers Using Deepfakes in Advanced Mobile Banking Malware Attacks – Source:thehackernews.com
Source: thehackernews.com – Author: . A Chinese-speaking threat actor codenamed GoldFactory has been attributed to the development of highly sophisticated banking trojans, including a previously undocumented...
Critical Exchange Server Flaw (CVE-2024-21410) Under Active Exploitation – Source:thehackernews.com
Source: thehackernews.com – Author: . Feb 15, 2024NewsroomThreat Intelligence / Vulnerability Microsoft on Wednesday acknowledged that a newly disclosed critical security flaw in Exchange Server has...
Google Threat Analysis Group’s Spyware Research: How CSVs Target Devices and Applications – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: Cedric Pernet A new publication from Google’s Threat Analysis Group focuses on commercial surveillance vendors, whose services are bought by governments for...
How to Use LogMeOnce Step-by-Step Guide – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: Luis Millares Image: LogMeOnce LogMeOnce is a decent password manager that includes a wide range of multifactor authentication (MFA) options. In this...
Incident Response Policy – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: This policy from TechRepublic Premium provides information on defining an incident, assigning an incident response team, documenting a plan and conducting a...
Network Security: A Top Priority for Healthcare Organizations – Source: securityboulevard.com
Source: securityboulevard.com – Author: FireMon FireMon is purpose-built for compliance reporting with 12 built-in reports, over 500 controls, and the ability to customize using a native...
5 Reasons You Should See a DSPM This Valentine’s Day – Source: securityboulevard.com
Source: securityboulevard.com – Author: claude.mandy It’s time to embrace the season of love and connection. Valentine’s Day is the perfect time to reevaluate our relationships—not just...
USENIX Security ’23 – What Are the Chances? Explaining the Epsilon Parameter in Differential Privacy – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman Authors/Presenters: Priyanka Nanayakkara, Mary Anne Smart, Rachel Cummings, Gabriel Kaptchuk, Elissa M. Redmiles Many thanks to USENIX for publishing their...
An Affordable and Encrypted Email and File sharing Solution for Small and Medium CPAs & Tax Preparers – Source: securityboulevard.com
Source: securityboulevard.com – Author: Orlee Berlove, reviewed by Gregg Laroche Small and Medium Certified Public Accountants (CPAs) and Licensed Tax Preparers struggle with the cost and...
An Affordable, Encrypted Email and File Sharing Solution for FERPA Compliance – Source: securityboulevard.com
Source: securityboulevard.com – Author: Orlee Berlove, reviewed by Gregg Laroche Educational Institutions and third parties providing services to these institutions frequently struggle with the cost and...
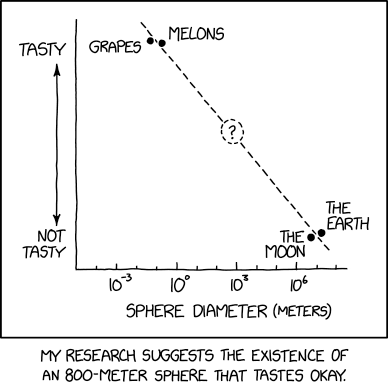
Randall Munroe’s XKCD ‘Sphere Tastiness’ – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman via the comic artistry and dry wit of Randall Munroe, creator of XKCD *** This is a Security Bloggers Network...
ALERT: Thieves❤️Wi-Fi Camera Jammers – Source: securityboulevard.com
Source: securityboulevard.com – Author: Richi Jennings Does your home security need a rethink? Wireless cameras are kinda useless, say cops. Security cameras that rely on Wi-Fi are...
Initial Access Broker Landscape in NATO Member States on Exploit Forum – Source: securityboulevard.com
Source: securityboulevard.com – Author: Flare Initial access brokers (IABs) gain unauthorized access to the system then sell this access to other malicious actors. Based on a...
Customer Story | Plainfield Community School Corporation Protects Its Students In Google Workspace With Cloud Monitor – Source: securityboulevard.com
Source: securityboulevard.com – Author: Katie Fritchen This Indiana School District Partners With ManagedMethods To Help Keep Its Data Secure And Students Safe In Google Workspace Background...
A Free Decryptor Tool for Rhysida Ransomware is Available – Source: securityboulevard.com
Source: securityboulevard.com – Author: Jeffrey Burt South Korean researchers exploited an implementation vulnerability in the ransomware strain used by the Rhysida group to enable victims decrypt...
Encryption Vital For Right to Privacy, European Court Rules – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Encryption & Key Management , Governance & Risk Management , Government Court of Human Rights Ruling Challenges Russian Data Interception in...