Source: www.bleepingcomputer.com – Author: Bill Toulas A U.S. federal court has issued a $9,918,000 penalty and an injunction against an individual named Scott Rhodes for making...
Author: CISO2CISO Editor 2
Panera Bread experiencing nationwide IT outage since Saturday – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Sergiu Gatlan Since Saturday, U.S. food chain giant Panera Bread has been experiencing a nationwide outage that has impacted its IT systems,...
It’s not just you: ChatGPT is down for many worldwide – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Mayank Parmar Update added to the bottom of the article. OpenAI’s ChatGPT is down for many people worldwide, with users facing multiple...
US sanctions crypto exchanges used by Russian darknet market, banks – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Sergiu Gatlan The U.S. Treasury Department’s Office of Foreign Assets Control (OFAC) has sanctioned three cryptocurrency exchanges for working with OFAC-designated Russian...
Hackers poison source code from largest Discord bot platform – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Bill Toulas The Top.gg Discord bot community with over 170,000 members has been impacted by a supply-chain attack aiming to infect developers...
New MFA-bypassing phishing kit targets Microsoft 365, Gmail accounts – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Bill Toulas Cybercriminals have been increasingly using a new phishing-as-a-service (PhaaS) platform named ‘Tycoon 2FA’ to target Microsoft 365 and Gmail accounts and...
US sanctions APT31 hackers behind critical infrastructure attacks – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Sergiu Gatlan The U.S. Treasury Department has sanctioned a Wuhan-based company used by the Chinese Ministry of State Security (MSS) as cover in attacks...
New ZenHammer memory attack impacts AMD Zen CPUs – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Bill Toulas Academic researchers developed ZenHammer, the first variant of the Rowhammer DRAM attack that works on CPUs based on recent AMD Zen microarchitecture that map...
Google’s new AI search results promotes sites pushing malware, scams – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Mayank Parmar Google’s new AI-powered ‘Search Generative Experience’ algorithms recommend scam sites that redirect visitors to unwanted Chrome extensions, fake iPhone giveaways,...
Over 100 US and EU orgs targeted in StrelaStealer malware attacks – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Bill Toulas A new large-scale StrelaStealer malware campaign has impacted over a hundred organizations across the United States and Europe, attempting to...
WordPress: Critical Flaw Detected in MiniOrange Plugins – Source: securityboulevard.com
Source: securityboulevard.com – Author: Shikha Dhingra Concerned about the vulnerability of WordPress plugins jeopardizing your website’s security? Did you know? Vulnerable plugins are the primary cause...
The Next Evolution of IAM: How Generative AI is Transforming Identity and Access – Source: securityboulevard.com
Source: securityboulevard.com – Author: Deepak Gupta – Tech Entrepreneur, Cybersecurity Author Identity and access management (IAM) remains a chief concern for organizations as workforce mobility, cloud...
Life in the Swimlane with Lindsay Jones, Director of Service Operations – Source: securityboulevard.com
Source: securityboulevard.com – Author: Kelly Dougherty Welcome to the “Life in the Swimlane” blog series. Here we will feature interviews with Swimlaners to learn more about...
Cybersecurity in Financial Disclosures: 11 Topics Your Section 1C of 10-K Filings Should Address – Source: securityboulevard.com
Source: securityboulevard.com – Author: Kayne McGladrey Last year, the Securities and Exchange Commission (SEC) announced new disclosure rules for publicly traded companies. Regulation S-K Item 106,...
How to Get the Most From Your Secrets Scanning – Source: securityboulevard.com
Source: securityboulevard.com – Author: Dex Tovin Secret scanning is essential for unlocking next-level software supply chain security. Get tips & best practices for optimal secret scanning...
The Show Must Go On – Source: securityboulevard.com
Source: securityboulevard.com – Author: Dave Lewis It has been a long time since I last posted on this site. Truth be told it was broken for...
Constella and Social Links Join Forces to Deliver Transformative OSINT Solutions – Source: securityboulevard.com
Source: securityboulevard.com – Author: Laura Bruck March 25, 2024[1] — Social Links, a leading developer of open-source intelligence (OSINT) software, has announced a strategic partnership with...
USENIX Security ’23 – Lukas Lamster, Martin Unterguggenberger, David Schrammel, and Stefan Mangard – HashTag: Hash-based Integrity Protection for Tagged Architectures – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman Security Bloggers Network Home » Security Bloggers Network » USENIX Security ’23 – Lukas Lamster, Martin Unterguggenberger, David Schrammel, and...
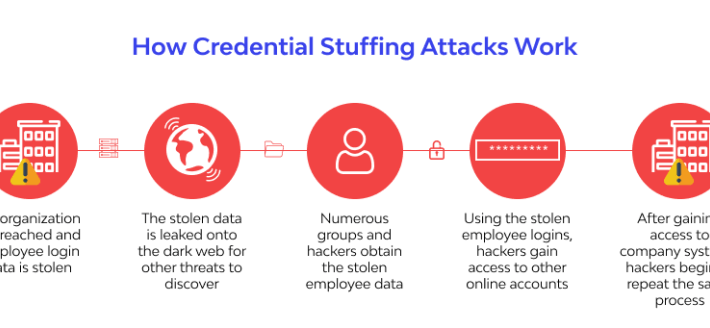
Top 4 Industries at Risk of Credential Stuffing and Account Takeover (ATO) attacks – Source: securityboulevard.com
Source: securityboulevard.com – Author: wlrmblog All industries are at risk of credential stuffing and account takeover (ATO) attacks. However, some industries are at a greater risk...
Log Formatting Best Practices for Improved Security – Source: securityboulevard.com
Source: securityboulevard.com – Author: Kevin Smith In the event of a security breach, logs play a crucial role in understanding the scope and impact of the...
UK Blames China for 2021 Hack Targeting Millions of Voters’ Data – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 The UK government has called out China state-affiliated threat actors for carrying out hacking campaigns against UK institutions and political figures...
Police Bust Multimillion-Dollar Holiday Fraud Gang – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 Police in Romania and Spain have struck a blow against a sophisticated cyber-fraud gang that tricked victims out of millions of...
Russian Cozy Bear Group Targets German Politicians – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 Security researchers have warned Western political parties to be on their guard after uncovering a new cyber-espionage campaign from Russian actors...
European Commission to Investigate Meta Subscription Model – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Governance & Risk Management , Privacy , Standards, Regulations & Compliance ‘Pay or Consent’ May Violate the Digital Services Act, Say...
CISOs: Make Sure Your Team Members Fit Your Company Culture – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 CISO Trainings , Recruitment & Reskilling Strategy , Training & Security Leadership Why? Because ‘Culture Eats Strategy for Breakfast,’ as the...
The AI Revolution and White-Collar Workers – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Artificial Intelligence & Machine Learning , Next-Generation Technologies & Secure Development , Recruitment & Reskilling Strategy Will AI Be a Catalyst...
Hospitals Lobby Feds to Clarify Breach Duties in UHG Attack – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Breach Notification , Healthcare , Industry Specific AHA Wants Change Healthcare on Hook for Notification in Potential Breach Marianne Kolbasuk McGee...
Webinar | The Cost of Convenience: Exploring the Risks of Password Reuse – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 James Condon Director of Security Research, Lacework James Condon is Director of Security Research at Lacework, where he leads the Lacework...
UK Discloses Chinese Espionage Activities – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Cyberwarfare / Nation-State Attacks , Fraud Management & Cybercrime Deputy Prime Minister Says Violet Typhoon Is Behind Attacks on UK Politicians...
Report Urges Congress to Form an Armed Cyber Military Branch – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Cyberwarfare / Nation-State Attacks , Fraud Management & Cybercrime Research Shows Military Suffers From Disjointed Cyber Operations Amid New Threats Chris...