Source: www.databreachtoday.com – Author: 1 Blockchain & Cryptocurrency , Cryptocurrency Fraud , Fraud Management & Cybercrime Also: Personal Data Theft From OKX; Terraform-SEC Settlement Terms Rashmi...
Author: CISO2CISO Editor 2
NetSPI Strengthens Attack Surface Management With Hubble Buy – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Attack Surface Management , Security Operations Acquiring Hubble Means NetSPI Can Now Manage External and Internal Attack Surfaces Michael Novinson (MichaelNovinson)...
Treasury Seeks Industry, Academic Insight on AI Use, Risks – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Artificial Intelligence & Machine Learning , Next-Generation Technologies & Secure Development Department Is Asking for Information About How AI Is Used...
NIST Publishes Draft OT Cybersecurity Guide for Water Sector – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Governance & Risk Management , Government , Industry Specific Agency Seeks Feedback on OT Security Reference Guide for Water, Wastewater Sectors...
Brazil’s Climb Onto the World Stage Sparks Cyber Risks – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Cybercrime , Cyberwarfare / Nation-State Attacks , Fraud Management & Cybercrime Cyber Spies, Extortionists and Domestic Crooks All Vie to Hack...
Everfox to Acquire British Hardware Security Vendor Garrison – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Endpoint Security , Government , Hardware / Chip-level Security High-Assurance Security Tech Boosts Everfox’s Government and Infrastructure Tools Michael Novinson (MichaelNovinson)...
Fraudsters Impersonate CISA in Money Scams – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Fraud Management & Cybercrime , Social Engineering CISA Won’t Ask You to Wire Money or Keep Discussions Secret Chris Riotta (@chrisriotta)...
Live Webinar | Special Delivery! Defending and Investigating Advanced Intrusions on Secure Email Gateways – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Nader Zaveri Senior Manager – Incident Response & Remediation, Google Cloud Nader Zaveri has over 15 years in the cybersecurity industry,...
Justifying Your Hybrid Cloud Network Security Investment – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 David Holmes Research Analyst for Zero Trust, Security, and Risk, Forrester David Holmes is a principal analyst at Forrester, advising security...
Ransomware: Disruption of Hospitals and Nearby Facilities – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Fraud Management & Cybercrime , Healthcare , Industry Specific Researchers Rahi Abouk and David Powell on Study Findings, Need for Better...
The Shift to Skills-Based Hiring – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Leadership & Executive Communication , Recruitment & Reskilling Strategy , Training & Security Leadership How and Why to Select Candidates Based...
On the Future of Cybersecurity in Hybrid Cloud Environments – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Artificial Intelligence & Machine Learning , Cloud Security , Next-Generation Technologies & Secure Development An Interview with Gigamon’s Chief Security Officer,...
UK Sides With APP Fraud Victims – Despite Industry Pressure – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Fraud Management & Cybercrime , Fraud Risk Management , Geo Focus: The United Kingdom Payments Regulator Says Banks Should Prioritize Customer...
Ransomware Gang TellYouThePass Exploits PHP Vulnerability – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Fraud Management & Cybercrime , Governance & Risk Management , Patch Management Flaw Allows Unauthenticated Attackers to Execute Arbitrary Code Prajeet...
Chinese-Made Biometric Access System Has 24 Vulnerabilities – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Identity & Access Management , Security Operations Kaspersky Unveils 24 Flaws in ZKTeco Terminals Prajeet Nair (@prajeetspeaks) • June 11, 2024...
Cleveland Cyber Incident Prompts Shutdown of City IT Systems – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Cybercrime , Fraud Management & Cybercrime , Incident & Breach Response Cleveland Investigating Cyber Incident that Forced City to Shutdown IT...
Dutch Agency Renews Warning of Chinese Fortigate Campaign – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Cyberwarfare / Nation-State Attacks , Fraud Management & Cybercrime , Network Firewalls, Network Access Control Chinese Cyber Espionage Campiagn Is ‘Much...
ChatGPT Integration Fortifies Apple’s Siri and Writing Tools – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Artificial Intelligence & Machine Learning , Next-Generation Technologies & Secure Development AI Integration Boosts Siri’s User Writing Tools As Apple Plays...
FCC Advances BGP Security Rules for Broadband Providers – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Standards, Regulations & Compliance Regulatory Body Approves Notice of Proposed Rulemaking Targeting BGP Hijacking Chris Riotta (@chrisriotta) • June 10, 2024...
Lawmakers: UHG Violating HIPAA Breach Notification Rule – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Breach Notification , Fraud Management & Cybercrime , Healthcare Bipartisan U.S. Senators Demand Change Healthcare Breach Notification by June 21 Marianne...
Psychological Strategies for Bridging the IT-OT Divide – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Cyberwarfare / Nation-State Attacks , Fraud Management & Cybercrime , Governance & Risk Management Ilionx’s Trish McGill on Tackling Geopolitical Risks...
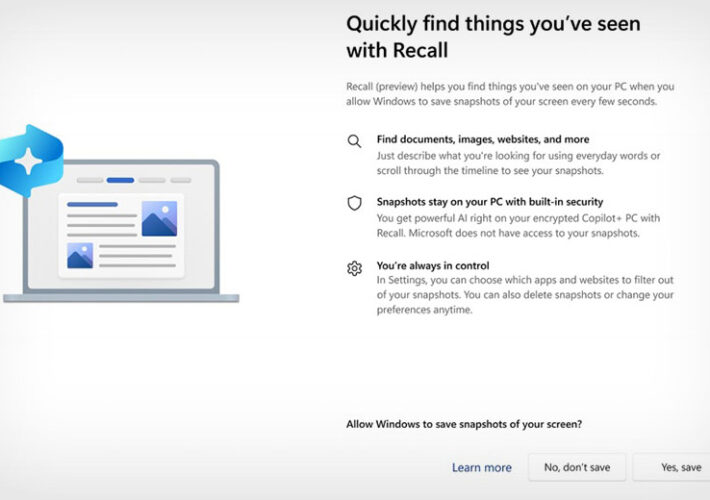
Microsoft Now Promises Extra Security for AI-Driven Recall – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Artificial Intelligence & Machine Learning , Next-Generation Technologies & Secure Development Concerns Remain Over Screenshot-Capture Feature and Microsoft’s Security Practices Mathew...
Hackers Claim They Breached Telecom Firm in Singapore – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Breach Notification , Cybercrime , Fraud Management & Cybercrime Threat Actor GhostR Says It Stole 34 GB of Data Prajeet Nair...
Critical PHP Vulnerability Threatens Windows Servers – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Governance & Risk Management , Patch Management , Vulnerability Assessment & Penetration Testing (VA/PT) Remote Code Execution Exploit Found; Patch Now...
ISMG Editors: Infosecurity Europe Conference 2024 Wrap-Up – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Application Security , Events , Infosecurity Europe Conference Panelists Discuss Latest Updates on AI Tech, Cyber Resilience and Regulations Anna Delaney...
Hypr Secures $30M to Expand Identity Protection Platform – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Identity & Access Management , Multi-factor & Risk-based Authentication , Security Operations Silver Lake Waterman Investment in Hypr Fuels Product Development,...
CISA Planning JCDC Overhaul as Experts Criticize Slow Start – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Government , Industry Specific , Standards, Regulations & Compliance Top US Cyber Defense Agency Aims to Revamp Its Key Public-Private Collaborative...
Qilin RaaS Group Believed to Be Behind Synnovis, NHS Attack – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Fraud Management & Cybercrime , Healthcare , Industry Specific Patient Care, Including Transplants, Still Disrupted at London Hospitals, Clinics Marianne Kolbasuk...
Collaborative Security: The Team Sport Approach – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 The shortage of cybersecurity professionals in a world where the demand for them is always increasing makes it necessary to treat...
Technical or Nontechnical? Choosing Your Cybersecurity Path – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Recruitment & Reskilling Strategy , Training & Security Leadership Assess Your Interests, Skills, Educational Background and Career Goals to Decide Brandy...