Source: www.csoonline.com – Author: New Heimdal study reveals how tool sprawl creates blind spots, with over half of providers experiencing daily or weekly burnout Survey of...
Author: CISO2CISO Editor 2
CSO hiring on the rise: How to land a top security exec role – Source: www.csoonline.com
Source: www.csoonline.com – Author: 2025 sees strong demand for top-level CSOs who can influence the C-suite, navigate regulatory and threat complexity, and meet the AI era...
Connex Credit Union Data Breach Impacts 172,000 People – Source: www.securityweek.com
Source: www.securityweek.com – Author: Eduard Kovacs Connex Credit Union has informed authorities that a recent data breach impacts 172,000 individuals. Connex is one of the largest...
Russian Hackers Exploited WinRAR Zero-Day in Attacks on Europe, Canada – Source: www.securityweek.com
Source: www.securityweek.com – Author: Eduard Kovacs A Russian threat group has been observed exploiting a WinRAR zero-day vulnerability as part of a cyberespionage campaign aimed at...
Manage Logins, Data Sharing, and Device Syncs from One Secure Vault – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: TechRepublic Academy Published August 11, 2025 We may earn from vendors via affiliate links or sponsorships. This might affect product placement on...
Train Your Team in AI-Powered Pen Testing for Just $19.99 – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: TechRepublic Academy Published August 11, 2025 We may earn from vendors via affiliate links or sponsorships. This might affect product placement on...
Disable Your SonicWall VPN: Threat Actors May Be Exploiting This Vulnerability – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: Megan Crouse Published August 11, 2025 SonicWall and other threat researchers are investigating the ongoing incidents. It’s unknown yet whether this is...
Anthropic’s Claude Code Arms Developers With Always-On AI Security Reviews – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: Liz Ticong Topic — Artificial Intelligence Published August 11, 2025 We may earn from vendors via affiliate links or sponsorships. This might...
Dia’s Paid Plan Marks New Phase in AI-Powered Web Browsing – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: Fiona Jackson Screenshot of the Dia browser. Dia, the AI-powered browser from The Browser Company that debuted in beta a few months...
Ghanaian Nationals Extradited for Roles in $100M Romance and Wire Fraud Ring – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: Four high-ranking members of a criminal organization based in Ghana have been indicted by the US Attorney’s Office, Southern District of New...
Embargo Ransomware Gang Amasses $34.2m in Attack Proceeds – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: The Embargo ransomware gang has generated approximately $34.2m in attack proceeds since emerging in April 2024, according to a new analysis by...
Eight Countries Face EU Action Over NIS2 Deadline Failings – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: Multiple European countries are facing the regulatory wrath of the European Commission for failing to transpose the NIS2 directive into domestic law....
UK Red Teamers “Deeply Skeptical” of AI – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: Offensive cybersecurity experts have largely failed to integrate AI into their services, expressing significant reservations about its possible benefits, according to a...
Operation Chakra V: Call Center Scammers and your PII – Source: securityboulevard.com
Source: securityboulevard.com – Author: Gary Warner Here we have another cautionary tale about off-shoring customer service when faced with the reality of Call Center Scams that...
The AI Threat: How Enterprises Can Defend Against the Next Generation of Attacks – Source: www.cyberdefensemagazine.com
Source: www.cyberdefensemagazine.com – Author: News team AI is transforming the way work gets done across industries. But while it improves business efficiencies, it also arms cybercriminals...
Telcom Security: The Intersection of Critical Infrastructure – Source: www.cyberdefensemagazine.com
Source: www.cyberdefensemagazine.com – Author: News team Telecommunications service providers (TSP) are foundational to the functioning of our modern technical society, serving as the conduit through which...
Free Wi-Fi Leaves Buses Vulnerable to Remote Hacking – Source: www.securityweek.com
Source: www.securityweek.com – Author: Eduard Kovacs Researchers demonstrated that smart buses, the transportation vehicles that incorporate various systems to improve safety, efficiency, and passenger experience, can...
The Future of API Security Reviews – Source: www.cyberdefensemagazine.com
Source: www.cyberdefensemagazine.com – Author: News team As organizations increasingly rely on application programming interfaces (APIs) to facilitate communication and data exchange between software systems, these “gates”...
SMBs Know the Risks, So Why Are Cybercriminals Still Winning? – Source: www.cyberdefensemagazine.com
Source: www.cyberdefensemagazine.com – Author: News team Cybercriminals are no longer primarily focused on large enterprises. They now see small- and medium-sized businesses (SMBs) as prime targets...
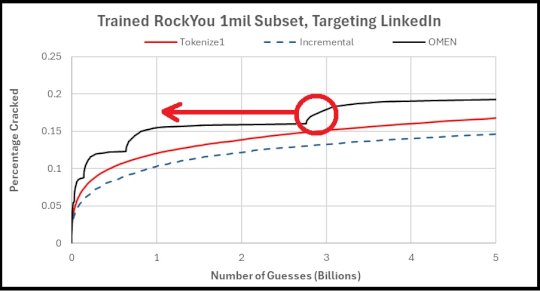
OMEN Improvements – Source: securityboulevard.com
Source: securityboulevard.com – Author: Matt Weir “If I had an hour to solve a problem, I would spend 55 minutes thinking about the problem and five...
Tips to Protect Yourself on LinkedIn from Fraud, Social Engineering, and Espionage – Source: securityboulevard.com
Source: securityboulevard.com – Author: Matthew Rosenquist LinkedIn is a great communication tool for business professionals that informs, provides opportunities, and fosters collaboration — which is exactly why...
Friday Squid Blogging: New Vulnerability in Squid HTTP Proxy Server – Source: www.schneier.com
Source: www.schneier.com – Author: Bruce Schneier HomeBlog Comments finagle • August 9, 2025 6:47 AM I was asked recently to do a security audit on a...
Google Project Zero Changes Its Disclosure Policy – Source: www.schneier.com
Source: www.schneier.com – Author: Bruce Schneier Google’s vulnerability finding team is again pushing the envelope of responsible disclosure: Google’s Project Zero team will retain its existing...
Former New York Times Cyber Reporter Issues Chilling Warning at Black Hat – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: Matt Gonzales Nicole Perlroth, former New York Times reporter and founding partner of Silver Buckshot Ventures, speaking at Black Hat 2025 in...
KrebsOnSecurity in New ‘Most Wanted’ HBO Max Series – Source: krebsonsecurity.com
Source: krebsonsecurity.com – Author: BrianKrebs A new documentary series about cybercrime airing next month on HBO Max features interviews with Yours Truly. The four-part series follows...
Are You Sending the Wrong Signals? – Source: www.cyberdefensemagazine.com
Source: www.cyberdefensemagazine.com – Author: News team The Salt team has spent the last 5-10 years producing blogs, comparison documents and webinars which highlight our credentials versus...
VCF 9.0 Live Patching Ends Maintenance Window Dread – Source: securityboulevard.com
Source: securityboulevard.com – Author: Tom Hollingsworth For IT administrators, two words sure to cause undue stress are “patching cycle.” It’s a necessary process fraught with challenges....
Randall Munroe’s XKCD ‘Geologic Periods’ – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman via the cosmic humor & dry-as-the-desert wit of Randall Munroe, creator of XKCD Permalink The post Randall Munroe’s XKCD ‘Geologic...
Survey Sees Drop in Cybersecurity Spending Growth Rates – Source: securityboulevard.com
Source: securityboulevard.com – Author: Michael Vizard A survey of 587 CISOs published this week finds security budget growth dropped to 4%, down from 8% in 2024,...
Tea App Data Breach Fallout: A New App with Security Flaws and Lawsuits – Source: securityboulevard.com
Source: securityboulevard.com – Author: Jeffrey Burt In the wake of the high-profile data breaches of the popular and controversial Tea app, another app called TeaOnHer for...