Source: www.lastwatchdog.com – Author: bacohido By Byron V. Acohido The countdown is on for security teams still managing digital certificates with spreadsheets and manual workarounds. Related:...
Author: CISO2CISO Editor 2
Smashing Security podcast #430: Poisoned Calendar invites, ChatGPT, and Bromide – Source: grahamcluley.com
Source: grahamcluley.com – Author: Graham Cluley Skip to content A poisoned Google Calendar invite that can hijack your smart home, a man is hospitalised after ChatGPT...
US Reportedly Hid Trackers in Shipments to Monitor AI Chips Diverted to China – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: Megan Crouse Topic — Artificial Intelligence Published August 13, 2025 Trackers were placed in the packaging and sometimes inside servers from Dell...
Microsoft’s Patch Tuesday: 100+ Updates Including Azure OpenAI Service, Memory Corruption Flaw – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: Megan Crouse Microsoft patched CVE-2025-50165, an “extremely high-risk” memory corruption flaw in its graphics component that could let attackers execute code over...
Hack of North Korean Spy’s Computer Exposes 8.9 GB of Espionage Operations – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: Liz Ticong Image: thichaa/Envato Hackers have infiltrated the computer of a North Korean government spy, stealing and leaking 8.9 GB of secret...
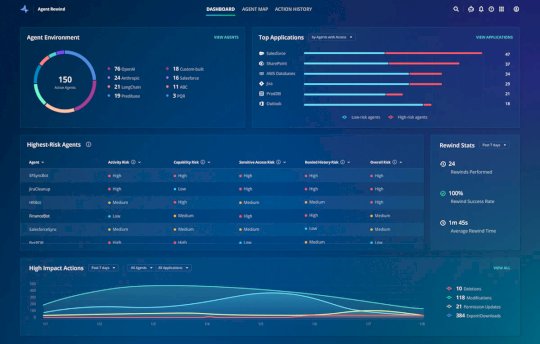
Fix AI Agent Mistakes With Rubrik’s Agent Rewind – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: Aminu Abdullahi Topic — Artificial Intelligence Published August 13, 2025 Rubrik’s new Agent Rewind tool can trace, audit, and safely reverse AI...
North Korea Attacks South Koreans With Ransomware – Source: www.darkreading.com
Source: www.darkreading.com – Author: Nate Nelson, Contributing Writer Please enable cookies. Sorry, you have been blocked You are unable to access darkreading.com Why have I been...
Fortinet Products Are in the Crosshairs Again – Source: www.darkreading.com
Source: www.darkreading.com – Author: Jai Vijayan, Contributing Writer Please enable cookies. Sorry, you have been blocked You are unable to access darkreading.com Why have I been...
Whispers of XZ Utils Backdoor Live on in Old Docker Images – Source: www.darkreading.com
Source: www.darkreading.com – Author: Alexander Culafi Please enable cookies. Sorry, you have been blocked You are unable to access darkreading.com Why have I been blocked? This...
Popular AI Systems Still a Work-in-Progress for Security – Source: www.darkreading.com
Source: www.darkreading.com – Author: Robert Lemos, Contributing Writer Please enable cookies. Sorry, you have been blocked You are unable to access darkreading.com Why have I been...
Patch Now: Attackers Target OT Networks via Critical RCE Flaw – Source: www.darkreading.com
Source: www.darkreading.com – Author: Elizabeth Montalbano, Contributing Writer Please enable cookies. Sorry, you have been blocked You are unable to access darkreading.com Why have I been...
What the LockBit 4.0 Leak Reveals About RaaS Groups – Source: www.darkreading.com
Source: www.darkreading.com – Author: Michele Campobasso Please enable cookies. Sorry, you have been blocked You are unable to access darkreading.com Why have I been blocked? This...
How an AI-Based ‘Pen Tester’ Became a Top Bug Hunter on HackerOne – Source: www.darkreading.com
Source: www.darkreading.com – Author: Rob Wright Please enable cookies. Sorry, you have been blocked You are unable to access darkreading.com Why have I been blocked? This...
How to Build, Optimize, & Manage AI on Google Kubernetes Engine – Source: securityboulevard.com
Source: securityboulevard.com – Author: Andy Suderman Artificial Intelligence (AI) is quickly changing modern enterprises, but harnessing its full potential demands not only excellent models, but infrastructure...
Rethinking Embedded IoT Security: Why Traditional IT Protections Fall Short – Source: securityboulevard.com
Source: securityboulevard.com – Author: Roland Marx In an era where billions of connected devices form the nervous system of critical infrastructure, embedded IoT systems have become...
Futurum Signal: Real-Time Market Intelligence for Cyber Defenders – Source: securityboulevard.com
Source: securityboulevard.com – Author: Alan Shimel In cybersecurity, speed is survival. When adversaries are moving at machine speed—launching AI-powered attacks, exploiting zero-days within hours of disclosure,...
Randall Munroe’s XKCD ‘Bad Map Projection: Interrupted Spheres’ – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman via the cosmic humor & dry-as-the-desert wit of Randall Munroe, creator of XKCD Permalink The post Randall Munroe’s XKCD ‘Bad...
New downgrade attack can bypass FIDO auth in Microsoft Entra ID – Source: www.proofpoint.com
Source: www.proofpoint.com – Author: Security researchers have created a new FIDO downgrade attack against Microsoft Entra ID that tricks users into authenticating with weaker login methods, making...
Work from home, malware included – Source: www.proofpoint.com
Source: www.proofpoint.com – Author: Welcome in! You’ve entered, Only Malware in the Building. Join us each month to sip tea and solve mysteries about today’s most...
Attackers Use Fake OAuth Apps with Tycoon Kit to Breach Microsoft 365 Accounts – Source: www.proofpoint.com
Source: www.proofpoint.com – Author: Cybersecurity researchers have detailed a new cluster of activity where threat actors are impersonating enterprises with fake Microsoft OAuth applications to facilitate...
Cybercrooks faked Microsoft OAuth apps for MFA phishing – Source: www.proofpoint.com
Source: www.proofpoint.com – Author: Proofpoint observed campaigns impersonating trusted brands like SharePoint and DocuSign with malicious OAuth applications to get into Microsoft 365 accounts. Threat actors...
Black Hat USA 2025 – AI, Innovation, and the Power of the Cybersecurity Community – Source: www.cyberdefensemagazine.com
Source: www.cyberdefensemagazine.com – Author: Gary By Gary Miliefsky, Publisher of Cyber Defense Magazine Black Hat, the cybersecurity industry’s most established and in-depth security event series, has...
The Looming Domino Effect of Cyberattacks on Energy and Utilities – Source: www.cyberdefensemagazine.com
Source: www.cyberdefensemagazine.com – Author: News team When systems go dark and become unavailable, consumers and operators may feel frustration, panic, and anger. When there is disruption...
The Limitations of Agentic AI in Cybersecurity: Why Large-Scale Autonomous Cyberattacks Aren’t Yet a Reality – Source: www.cyberdefensemagazine.com
Source: www.cyberdefensemagazine.com – Author: News team There are a few universal rules that apply in the ongoing cybersecurity arms race between attackers and security companies. The...
AI Takes Center Stage at Black Hat USA 2025 – Booz Allen Leads the Conversation – Source: www.cyberdefensemagazine.com
Source: www.cyberdefensemagazine.com – Author: Gary Gary Miliefsky August 12, 2025 Black Hat USA 2025 was nothing short of groundbreaking. The show floor and conference tracks were...
The Inevitable AI Breach? Predicting Data Theft Through Shared Vulnerabilities – Source: www.cyberdefensemagazine.com
Source: www.cyberdefensemagazine.com – Author: News team Statistics shared by the World Economic Forum in 2024 show healthcare and finance to be the top two industries most targeted by...
The Impact of Cloud computing in 2025 – Source: www.cyberdefensemagazine.com
Source: www.cyberdefensemagazine.com – Author: News team Key Trends Driving Cloud Computing in 2025 Smarter Cloud Tools with AI Artificial Intelligence (AI) and Machine Learning (ML) have...
New trends in phishing and scams: how AI and social media are changing the game – Source: securelist.com
Source: securelist.com – Author: Olga Altukhova Introduction Phishing and scams are dynamic types of online fraud that primarily target individuals, with cybercriminals constantly adapting their tactics...
Silicon under siege: Nation-state hackers target semiconductor supply chains – Source: www.csoonline.com
Source: www.csoonline.com – Author: As semiconductors become central to national security and economic power, cyberattacks have evolved into long-term infiltration campaigns driven by global rivalries. Cyberattacks...
New ransomware ‘Charon’ uses DLL sideloading to breach critical infrastructure – Source: www.csoonline.com
Source: www.csoonline.com – Author: Charon uses encrypted payloads and trusted binaries to bypass EDR defenses, marking a shift toward stealthier, more persistent ransomware campaigns. Trend Micro...