Source: securityboulevard.com – Author: Irina 1. Least Privilege Access Least privilege access means granting users, devices, and applications only the minimum permissions they need to perform...
Author: CISO2CISO Editor 2
How AI Agents Are Creating a New Class of Identity Risk – Source: securityboulevard.com
Source: securityboulevard.com – Author: Dan Kaplan AI agents, a rapidly growing category of non-human identities, violate the core zero-trust principle (continuous verification) by maintaining long-lived credentials...
How to Streamline Your Kubernetes Add-On Updates and Stay Secure – Source: securityboulevard.com
Source: securityboulevard.com – Author: Stevie Caldwell Kubernetes add-ons are the backbone of modern clusters, powering everything from ingress and networking to observability, security, and automation. Without...
Cutting Through AppSec Noise in the Age of GenAI – Source: securityboulevard.com
Source: securityboulevard.com – Author: Alan Shimel The way organizations think about application security is shifting—fast. OX Security Co-Founder and CEO Neatsun Ziv talks about why the...
The Hidden Costs of Fragmented Security Infrastructure – Source: securityboulevard.com
Source: securityboulevard.com – Author: Gagan Gulati Cybersecurity conversations often focus on the latest threats, breaches, or AI-powered responses. But beneath the surface of every high-profile attack...
Why OT Security Demands Context, Not Just Controls – Source: securityboulevard.com
Source: securityboulevard.com – Author: Alan Shimel Operational technology (OT) security is no longer a niche concern—it’s front and center in today’s cyber conversations. At Black Hat...
Randall Munroe’s XKCD ‘Thread Meeting’ – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman via the comic artistry and dry wit of Randall Munroe, creator of XKCD Permalink *** This is a Security Bloggers...
Frequently Asked Questions About Chinese State-Sponsored Actors Compromising Global Networks – Source: securityboulevard.com
Source: securityboulevard.com – Author: Scott Caveza, Satnam Narang An analysis of Tenable telemetry data shows that the vulnerabilities being exploited by Chinese state-sponsored actors remain unremediated...
When Salesforce Becomes a De Facto Credential Repository: Lessons from the Drift OAuth Breach – Source: securityboulevard.com
Source: securityboulevard.com – Author: Dan Kaplan TL;DR: The recently disclosed Salesforce data-theft attacks highlight two distinct non-human identity failures. First, Drift’s handling of OAuth tokens broke...
Chinese hacking group Salt Typhoon expansion prompts multinational advisory – Source: www.csoonline.com
Source: www.csoonline.com – Author: Notorious for breaching major US telecoms and ISPs, the threat actors have now infiltrated Dutch infrastructure, and global authorities warn its reach...
KI greift erstmals autonom an – Source: www.csoonline.com
Source: www.csoonline.com – Author: Erste KI-gestützte Cyberattacken in freier Wildbahn stellen Sicherheitsentscheider vor neue Herausforderungen – und könnten im kriminellen Untergrund eine „Entlassungswelle“ auslösen. Das KI-gestützte...
Cybercrime increasingly moving beyond financial gains – Source: www.csoonline.com
Source: www.csoonline.com – Author: The cybercrime industry is largely organized around one motivation: to get the target person, company or organization to shell out a significant...
An Audit Isn’t a Speed Bump — It’s Your Cloud Co-Pilot – Source: www.darkreading.com
Source: www.darkreading.com – Author: Ravi Sharma Please enable cookies. Sorry, you have been blocked You are unable to access darkreading.com Why have I been blocked? This...
Proof-of-Concept in 15 Minutes? AI Turbocharges Exploitation – Source: www.darkreading.com
Source: www.darkreading.com – Author: Robert Lemos, Contributing Writer Please enable cookies. Sorry, you have been blocked You are unable to access darkreading.com Why have I been...
Apple Contends UK’s ‘EU-Style’ Antitrust Regulations Harm Users and Developers – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: Fiona Jackson Image: misu/Adobe Stock Apple has warned the UK government against applying “EU-style rules” on technology companies. The iPhone maker argues...
58% of Organizations Are Unprepared for Cyberattacks – Source: www.proofpoint.com
Source: www.proofpoint.com – Author: Proofpoint has released its most recent Voice of the CISO report, surveying 1,600 CISOs across 16 countries to better understand their challenges, expectations...
Training Bank Employees on Cybersecurity – Source: www.proofpoint.com
Source: www.proofpoint.com – Author: Aug 26 2025 Security Annual cybersecurity training may help an organization stay compliant, but it doesn’t mean they’re more secure. Teta Alim...
AI website builder Lovable fuels rise in phishing & scams – Source: www.proofpoint.com
Source: www.proofpoint.com – Author: Cybercriminals are increasingly using the AI-driven website builder Lovable to rapidly create and host fraudulent sites for phishing, malware delivery, and financial...
CISOs grow more concerned about risk of material cyberattack – Source: www.proofpoint.com
Source: www.proofpoint.com – Author: An article from A report by Proofpoint shows growing anxiety among security leaders about their companies’ cyber readiness. Published Aug. 26, 2025...
Illicit activity powered by Lovable website builder abuse on the rise – Source: www.proofpoint.com
Source: www.proofpoint.com – Author: Phishing, AI/ML More malicious websites, malware portals, and phishing pages have been created using the artificial intelligence-powered website creation and hosting platform...
How attackers adapt to built-in macOS protection – Source: securelist.com
Source: securelist.com – Author: Alexander Chudnov If a system is popular with users, you can bet it’s just as popular with cybercriminals. Although Windows still dominates,...
Reduce Fraud Risk with Effective Identity Verification – Source: www.cyberdefensemagazine.com
Source: www.cyberdefensemagazine.com – Author: News team In a world where transactions occur smoothly across borders and platforms, the need for robust fraud and risk management strategies has become...
Innovator Spotlight: ManageEngine – Source: www.cyberdefensemagazine.com
Source: www.cyberdefensemagazine.com – Author: Gary Unifying IT Management and Security with ManageEngine In today’s digital landscape, IT can feel like juggling flaming torches, one wrong move...
Affiliates Flock to ‘Soulless’ Scam Gambling Machine – Source: krebsonsecurity.com
Source: krebsonsecurity.com – Author: BrianKrebs Last month, KrebsOnSecurity tracked the sudden emergence of hundreds of polished online gaming and wagering websites that lure people with free...
CISA, FBI, NSA Warn of Chinese ‘Global Espionage System’ – Source: www.darkreading.com
Source: www.darkreading.com – Author: Alexander Culafi Please enable cookies. Sorry, you have been blocked You are unable to access darkreading.com Why have I been blocked? This...
Hackers Steal 4M+ TransUnion Customers’ Data – Source: www.darkreading.com
Source: www.darkreading.com – Author: Kristina Beek Please enable cookies. Sorry, you have been blocked You are unable to access darkreading.com Why have I been blocked? This...
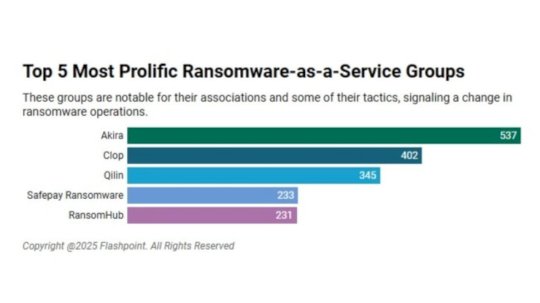
Akira, Cl0p Top List of 5 Most Active Ransomware-as-a-Service Groups – Source: www.darkreading.com
Source: www.darkreading.com – Author: Arielle Waldman Please enable cookies. Sorry, you have been blocked You are unable to access darkreading.com Why have I been blocked? This...
1,000+ Devs Lose Their Secrets to an AI-Powered Stealer – Source: www.darkreading.com
Source: www.darkreading.com – Author: Nate Nelson, Contributing Writer Please enable cookies. Sorry, you have been blocked You are unable to access darkreading.com Why have I been...
Dark Reading Confidential: A Guided Tour of Today’s Dark Web – Source: www.darkreading.com
Source: www.darkreading.com – Author: Dark Reading Staff Please enable cookies. Sorry, you have been blocked You are unable to access darkreading.com Why have I been blocked?...
CISA’s New SBOM Guidelines Get Mixed Reviews – Source: www.darkreading.com
Source: www.darkreading.com – Author: Becky Bracken Please enable cookies. Sorry, you have been blocked You are unable to access darkreading.com Why have I been blocked? This...