Source: securityboulevard.com – Author: CQ Prime Threat Research Team
API threat research by the Cequence CQ Prime Threat Research team during the second half of 2022 confirms that API security and API attack mitigation are two sides of the same coin, and both are essential to ensure the security of APIs. Attackers continue to use tried and true techniques to find and exploit shadow APIs, with the team observing 45 billion search attempts for shadow APIs over six months.
In addition, with data from approximately one trillion transactions spanning a variety of industries, the team found that attackers are relentlessly modifying their payloads, with new and unique fingerprints providing valuable insights into the tenacity and sophistication of their tactics, techniques, and procedures (TTPs).
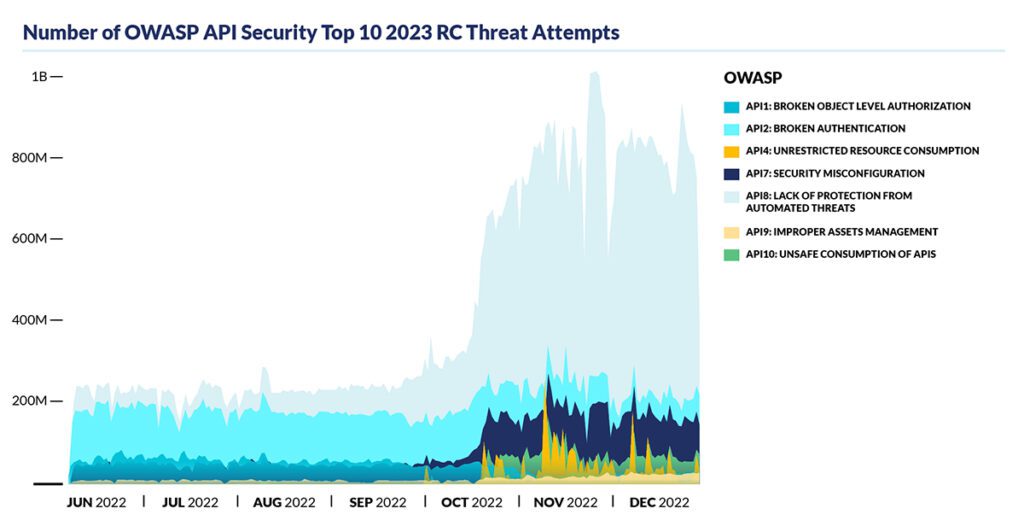
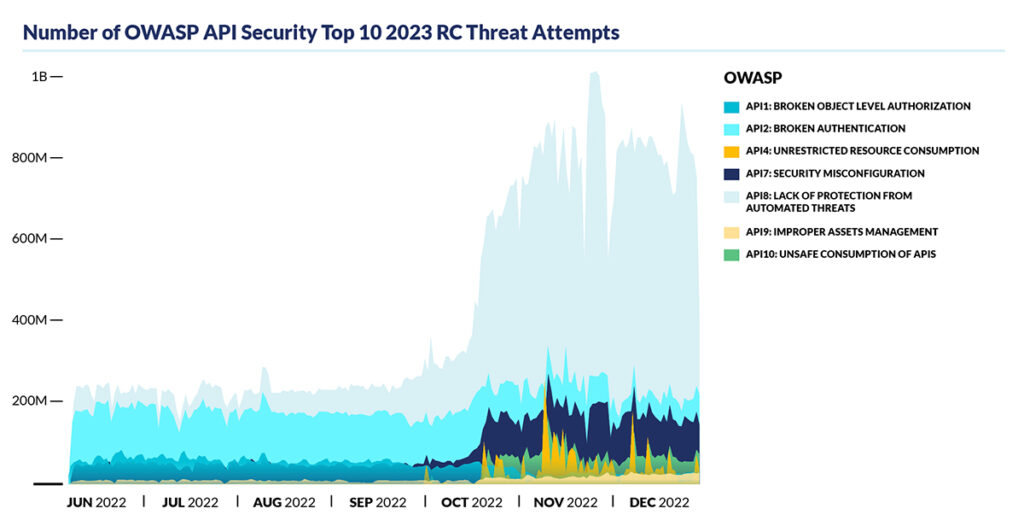
- New OWASP API threat category: lack of protection from automated threats: The CQ Prime Threat Research team mapped its observations for the second half of 2022 to the proposed API8:2023, Lack of Protection from Automated Threat category in the OWASP API Security Top 10 2023RC. The findings confirm that automated attacks and API security are complementary and necessitate a robust API security program with API attack mitigation capabilities.
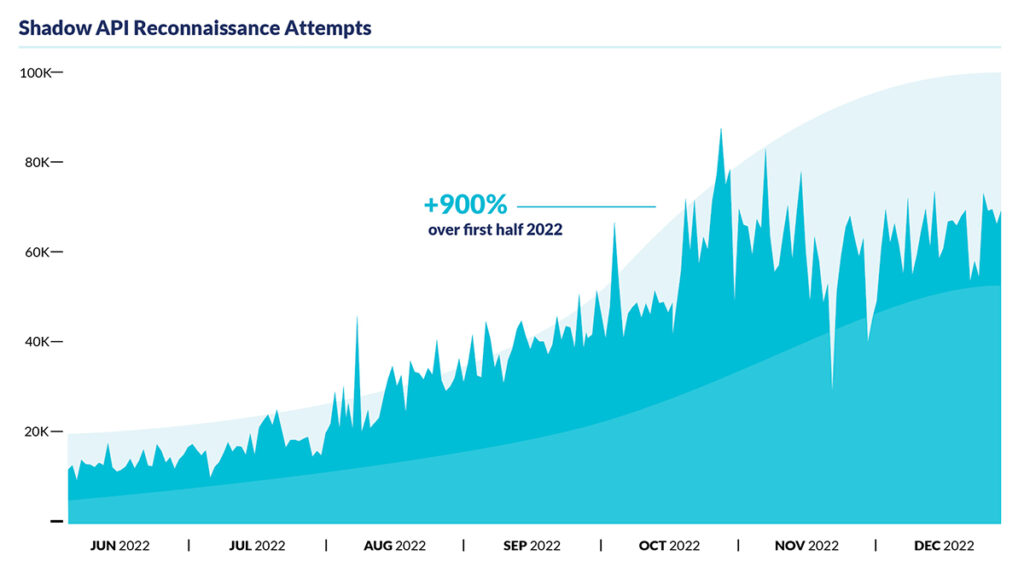
- 900% increase in attackers looking for shadow APIs: The threat landscape of shadow APIs has become increasingly alarming. In the second half of 2022 alone, approximately 45 billion search attempts were made for shadow APIs, marking a 900% increase from the 5 billion attempts made in the first half of 2022.
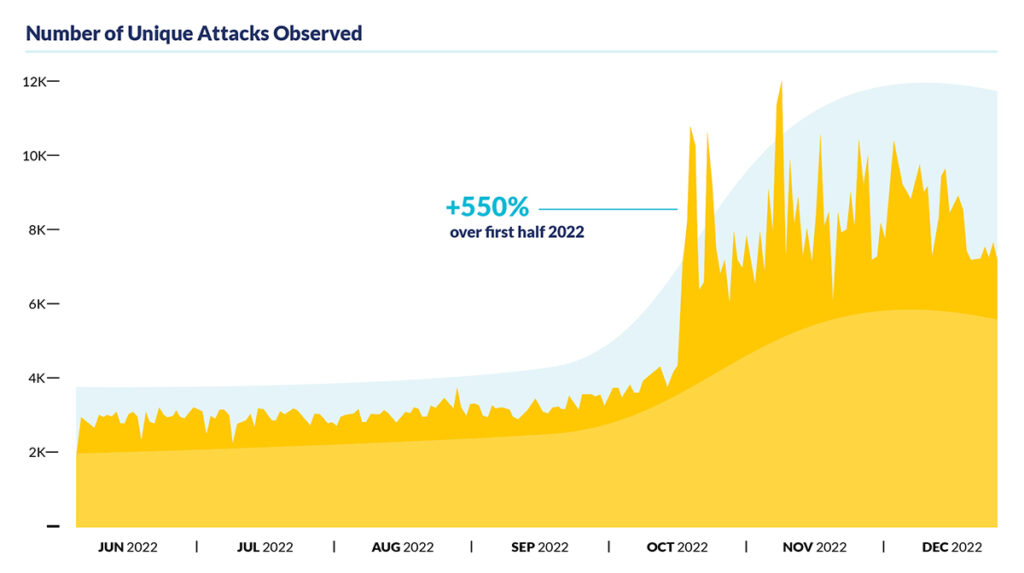
- Holiday shopping sees a 550% increase in API threats: Attackers are particularly active during the holiday season when high-value products are frequently introduced. For example, the data shows that the number of unique TTPs employed by attackers, rising from approximately 2,000 in June to a staggering 11,000 by mid-November 2022.
- Attackers Increasingly Combine API and Web Application Security Tactics: From June 2022 to October 2022, attackers favored traditional application security tactics; however, as the holidays approached, there was a 220% surge in API security tactics like anomalous traffic.
- Mobile devices continue to be extremely valuable for attacks: The constant stream of attacks on the telecom industry has created a common misconception that they lack adequate security measures. They are a high-value target due to the scope of their attack surface area and the value of the attack target – our mobile devices. These devices with varying service configurations contain user information and phone numbers that’s extremely valuable to attackers.
Protecting your APIs from Relentless and Sophisticated Attacks
Having a complete understanding of how correctly coded APIs and those with errors can be attacked is critical to protecting your APIs from exploits and abuse. Armed with this understanding security operations and development decision makers and practitioners can make great strides to complete API lifecycle protection as a key initiative. Organizations looking for end-to-end API protection, including automated attack mitigation should look for solutions that allow them to discover their APIs, assess risks and enforce compliance while natively detecting and mitigating automated attacks and vulnerability exploits.
- Discover: Right from the moment that a private, public, or partner API is used by developers as part of their application development there must be a way to discover and inventory all APIs. An often-overlooked aspect of discovery is determining the unknown attack surface – most organizations are unaware of how many shadows, hidden, deprecated, and third-party APIs they have, leaving many unprotected.
- Comply: Then there must be a way to assess that API inventory for risk, using API security testing to ensure compliance with secure API specifications and being able to test APIs before they go live. In addition, detection and remediation of coding errors, lack of best practices, or improper training can lead to vulnerabilities easily exploited by bad actors.
- Protect: APIs enable high speed communication often to back-end systems making them prime targets for automated attacks and business logic abuse, even when perfectly coded. Attackers are relentless as they execute business logic abuse such as stolen credentials or broken authentication processes to exploit APIs, commit theft, fraud, data exfiltration and business disruption. There must be a way to leverage threat intelligence to quickly detect abuse and natively block the bad activity.
Organizations with complete API visibility have a greater awareness of the types of threats they may face and the relative risks to their APIs. They can then use this knowledge to inform their ongoing efforts to detect advanced threats and prevent attacks from granting threat actors access to their data and networks.
Get Your Copy of The API Threat Research Report
To learn more, download the full report API Protection Report Findings Validate the New OWASP API Threat Category: Lack of Protection from Automated Threats.
The post API Threat Research Validates Robust API Security Program with Automated API Attack Mitigation Capabilities appeared first on Cequence Security.
*** This is a Security Bloggers Network syndicated blog from Cequence Security authored by CQ Prime Threat Research Team. Read the original post at: https://www.cequence.ai/blog/api-security/api-threat-research-validates-robust-api-security/
Original Post URL: https://securityboulevard.com/2023/05/api-threat-research-validates-robust-api-security-program-with-automated-api-attack-mitigation-capabilities/
Category & Tags: Security Bloggers Network,API security,CQ Prime Threat Research – Security Bloggers Network,API security,CQ Prime Threat Research
Views: 0