Source: www.bitdefender.com – Author: Graham Cluley
The US Department of Justice has announced that it has disrupted the operations of the ALPHV ransomware group, and seized decryption keys that could help 500 victims unscramble their files without having to pay a ransom.
The Russian-speaking ALPHV (also known as BlackCat or Noberus) is one of the world’s most notorious ransomware groups, having counted amongst its many victims Beverly Hills plastic surgeries, Las Vegas casino giant MGM Resorts, hotel chains, and cosmetics firm Estée Lauder.
Just last month ALPHV created headlines after audaciously filing a complaint to the SEC that a company it had hacked (but had declined to pay a ransom) had not notified the authorities of the data breach.
The US DOJ says it considers ALPHV/Blackcat to be the second most prolific ransomware-as-a-service variant in the world, based upon the hundreds of millions of dollars it has extorted from victims around the world.
From today however, visitors to ALPHV’s dark web site have been greeted with a banner saying that the site has been seized by the authorities.

And, it emerges, the FBI has been working hard behind-the-scenes with dozens of ALPHV victims – saving them an estimated US $68 million in ransoms, by providing a method to decrypt their data for free.
As described in an unsealed search warrant, the ransomware gang’s infrastructure was not as secure as it might have wished.
As Bleeping Computer reports, an FBI confidential source managed to successfully sign-up to be an affiliate with the ALPHV/BlackCat ransomware operation and was granted access to the group’s backend affiliate panel.
Having managed to gain access to ALPHV’s private control panel, FBI agents were able to gather substantial information about the criminal enterprise’s operations:
“From the Campaigns screen, affiliates can see the victim entity, full ransom price demanded, discount ransom price, expiration date, cryptocurrency addresses, cryptocurrency transactions, type of computer system compromised, ransom demand note, chats with the victim, and more,” explained the FBI.
With this access, investigators were able to obtain the decryption keys used in attacks and provide them to hundreds of victims to recover their data for free.
ALPHV/BlackCat is a business. A criminal business, admittedly. But like any business it’s not going to take kindly to its money-making operations being disrupted (in this case, by crime-fighting authorities.)
Within hours of the Department of Justice issuing its press release announcing that it had disrupted some of the ransomware group’s activities, ALPHV/BlackCat had an announcement of its own to make.
On the dark web ALPHV/BlackCat claimed it had “unseized” its domain and threatened retaliation against the United States and other countries that had assisted in the takedown, by allowing its affiliates to launch attacks against critical infrastructure.
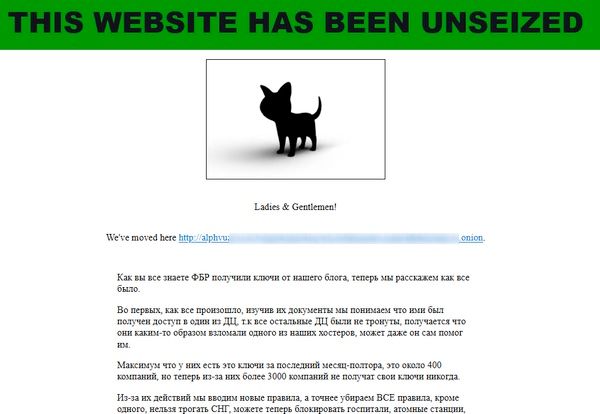
As security researcher Allan Liska explained on Twitter, the ransomware group’s claims that it has “unseized” its server are somewhat disingenuous. However, the encouragement to ALPHV/BlackCat affiliates to launch even more attacks against yet more critical targets can most definitely be seen as a raising of the stakes.
In short, ALPHV/BlackCat says it isn’t going to “play nice” anymore… as if any group that extorted millions from innocent companies by encrypting data and exfiltrating data can ever be said to be “playing nice.”
Original Post URL: https://www.bitdefender.com/blog/hotforsecurity/alphv-blackcat-ransomware-operation-disrupted-but-criminals-threaten-more-attacks/
Category & Tags: Data loss,Guest blog,Law & order,Malware,Ransomware,BlackCat,FBI,ransomware – Data loss,Guest blog,Law & order,Malware,Ransomware,BlackCat,FBI,ransomware




















































