Source: hackread.com – Author: Deeba Ahmed.
SUMMARY
- Malicious Package Found: ReversingLabs uncovered aiocpa, a Python package targeting crypto wallets via malicious updates.
- Unique Attack: Hackers built trust by publishing a legitimate-looking crypto tool before injecting harmful code.
- AI Detection: ReversingLabs’ Spectra Assure flagged the package using machine learning to detect hidden malicious behaviour.
- Action Taken: PyPI reported, quarantined, and removed the package to stop further harm.
- Key Takeaways: Regular security checks, machine learning tools, and cautious dependency management are vital to combat open-source threats.
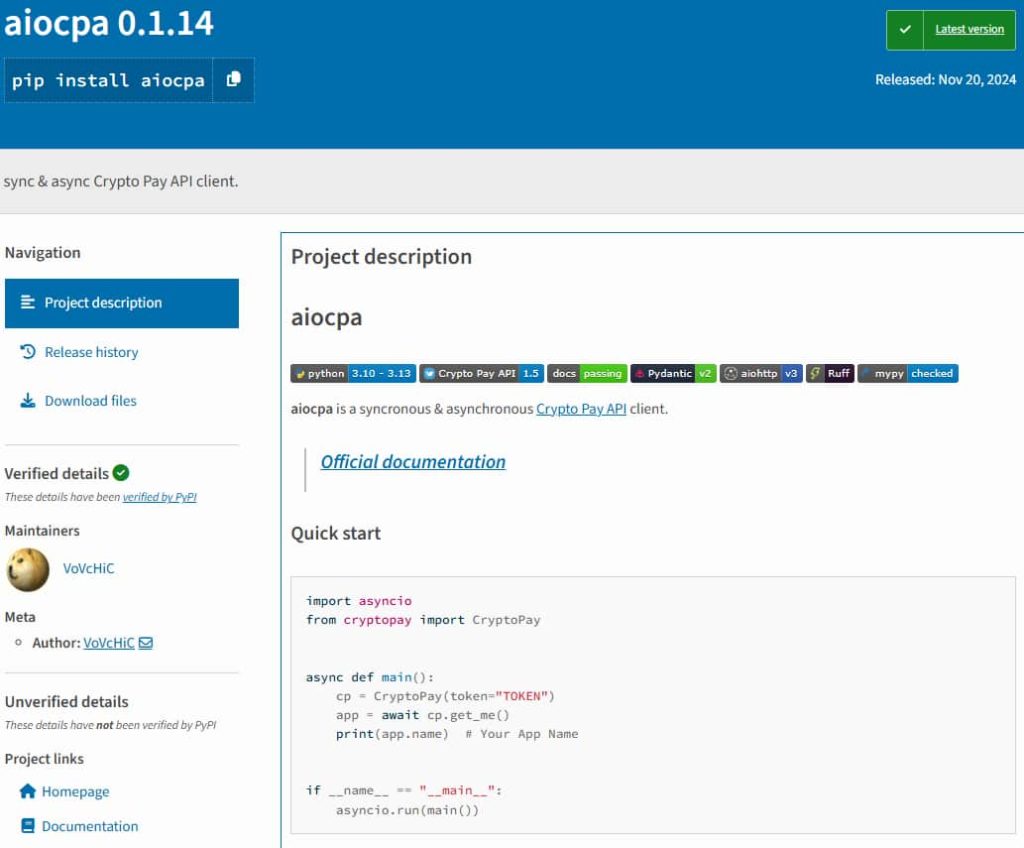
The machine learning-based threat-hunting system of leading threat intelligence and cybersecurity firm ReversingLabs (RL) recently detected malicious code in a legitimate-looking package, “aiocpa.“ According to RL’s investigation, shared with Hackread.com, this package was designed to compromise cryptocurrency wallets.
Through differential analysis of two package versions, RL was able to determine how these attackers carried out their distinctive campaign. The package, a synchronous and asynchronous Crypto Pay API client, has been downloaded 12,100 times.
While probing, researchers identified what makes this campaign unique. Unlike most attacks targeting open-source repositories like npm and PyPI, in this campaign, the threat actors published their own crypto client tool to gradually build trust with a growing user base. Then, they struck. An apparently harmless update to the aiocpa package (version 0.1.13 and later) injected malicious code.
“The malicious actor was observed trying to take over an existing PyPI project named pay, probably to gain access to an established user base, or the attacker estimated that such a package name would attract more victims,” researchers observed.
How Machine Learning Spotted the Trouble
RL uses a machine learning-based threat hunting system called Spectra Assure. This system continuously scans open-source packages for suspicious behaviour. In the case of aiocpa, on November 21, 2024, Spectra Assure flagged the updated package due to its resemblance to previously encountered malware.
Further revealed obfuscated code within the aiocpa package with numerous versions published until September 2024. This code was hidden behind layers of encryption and was designed to steal sensitive information like crypto trading tokens. If stolen, this data could be used to drain victims’ cryptocurrency wallets.
Researchers noted in the blog post that application security testing (AST) tools wouldn’t have caught this attack. The malicious code wasn’t present in the referenced GitHub repository, which would typically be reviewed for legitimacy. This is why advanced tools like Spectra Assure are crucial. They analyse code behaviour, allowing for a deeper inspection than traditional methods.
RL reported this malicious package to the Python Package Index (PYPI) for removal, which was later published on their blog on November 25. Researchers at Phylum reported on RL’s discovery, highlighting the uniqueness of the malicious campaign
The incident highlights the evolving nature of open-source software threats making it essential to perform regular security assessments, and consider machine learning-based threat hunting tools for powerful protection. Regular evaluation of third-party code, tools, packages, and extensions is also crucial.
Furthermore, PyPI users should be aware of package name takeover, a serious supply chain infection vector. If a project pay dependency is taken over by a threat actor, a new malicious version could be published to PyPI. The PyPI security team advises users to pin dependencies and versions, using hashes to prevent unwanted updates.
- ChatGPT Sandbox Flaws Enabling Python Execution
- PyPI Exploited to Infiltrate Systems Through Python Packages
- PythonAnywhere Cloud Platform Abused to Host Ransomware
- Qubitstrike Malware Hits Jupyter Notebooks for Cryptojacking
- VMCONNECT: Malicious PyPI Package Mimicking Python Tools
- New version of Jupyter infostealer delivered through MSI installer
Original Post url: https://hackread.com/aiocpa-python-package-cryptocurrency-infostealer/
Category & Tags: Security,Malware,aiocpa,Cryptocurrency,Infostealer,Python,security – Security,Malware,aiocpa,Cryptocurrency,Infostealer,Python,security
Views: 2