Source: securityboulevard.com – Author: Shubham Jha
Keeping pace with the latest cybersecurity threats is vital for organizations of all sizes. Here at Strobes, our security team has assembled a list of the top 5 most critical Common Vulnerabilities and Exposures (CVEs) discovered in April 2024. By staying informed about these vulnerabilities, you can take steps to mitigate potential risks and safeguard your systems. This blog post will provide a closer look at these CVEs.
CVE-2024-27322: Vulnerability in R Programming Language Allows Arbitrary Code Execution
CVE-2024-27322 is a vulnerability found in the R programming language that allows attackers to execute malicious code on a target system. This can be achieved through specially crafted RDS (R Data Serialization) files or R packages. These files are commonly used to share data between developers and data scientists, increasing the risk of exploitation.
Here’s a breakdown of the CVE:
- CVE-ID: CVE-2024-27322
- Affected Software: R programming language (versions 1.4.0 up to but not including 4.4.0)
- Impact: Arbitrary code execution on the target system
This vulnerability is rated as severe due to the following reasons:
- Widespread use of R in data analysis and AI/ML applications
- Potential for attackers to compromise systems through user-provided data
- Existence of the vulnerable code in projects of major technology firms and software vendors
If you use R for data analysis, it’s crucial to update to the latest version (4.4.0 or later) to mitigate this risk. You can find more information and patching instructions from the following resources:
CVE-2024-2389: Unauthenticated Command Injection in Flowmon
CVE-2024-2389 is a critical unpatched security vulnerability that affects Flowmon versions prior to 11.1.14 and 12.3.5. Flowmon is a network traffic monitoring software used to analyze and troubleshoot network activity. This vulnerability allows an unauthenticated user to gain remote access to the system via the Flowmon management interface and execute arbitrary system commands. This means an attacker could potentially take complete control of the affected system.
Here’s a breakdown of the CVE:
- CVE ID: CVE-2024-2389
- Affected Products: Flowmon versions prior to 11.1.14 and 12.3.5
- Vulnerability Type: Operating system command injection vulnerability
- Impact: An unauthenticated attacker can gain remote access to the system and execute arbitrary commands
Here are some recommendations to address this vulnerability:
- Apply the patch as soon as it becomes available from Progress, the vendor of Flowmon.
- Follow security best practices such as keeping your software up to date and using strong passwords.
If you are unsure about your Flowmon version or how to apply the patch, you should consult the Progress documentation or contact their support team.
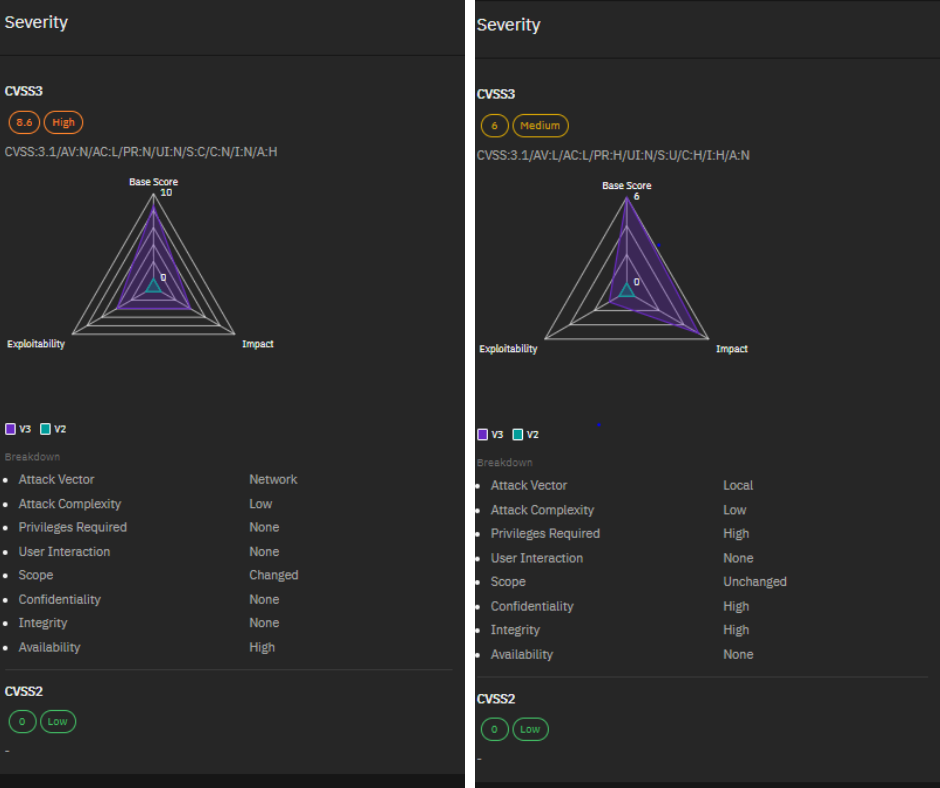
CVE-2024-20353 and CVE-2024-20359: Cisco ASA and FTD Vulnerabilities Exploited by Nation-State Actors
CVE-2024-20353 and CVE-2024-20359 are vulnerabilities that affected Cisco ASA and Firepower Threat Defense (FTD) devices. A nation-state group exploited these vulnerabilities in a cyber attack campaign named ArcaneDoor, which targeted government entities and critical infrastructure organizations for espionage purposes.
Here’s a breakdown of the CVEs:
- CVE-2024-20353: This vulnerability resides in the management and VPN web servers of the Cisco devices. It could allow an attacker to remotely crash the device (denial-of-service attack) without any authentication required.
- CVE-2024-20359: This vulnerability is more severe. It could allow an attacker to remotely execute malicious code on the device, potentially leading to data breaches or implanting malware for long-term access.
Cisco released security patches to address these vulnerabilities in April 2024. It is crucial to update your Cisco ASA and FTD devices to the latest versions to mitigate these risks.
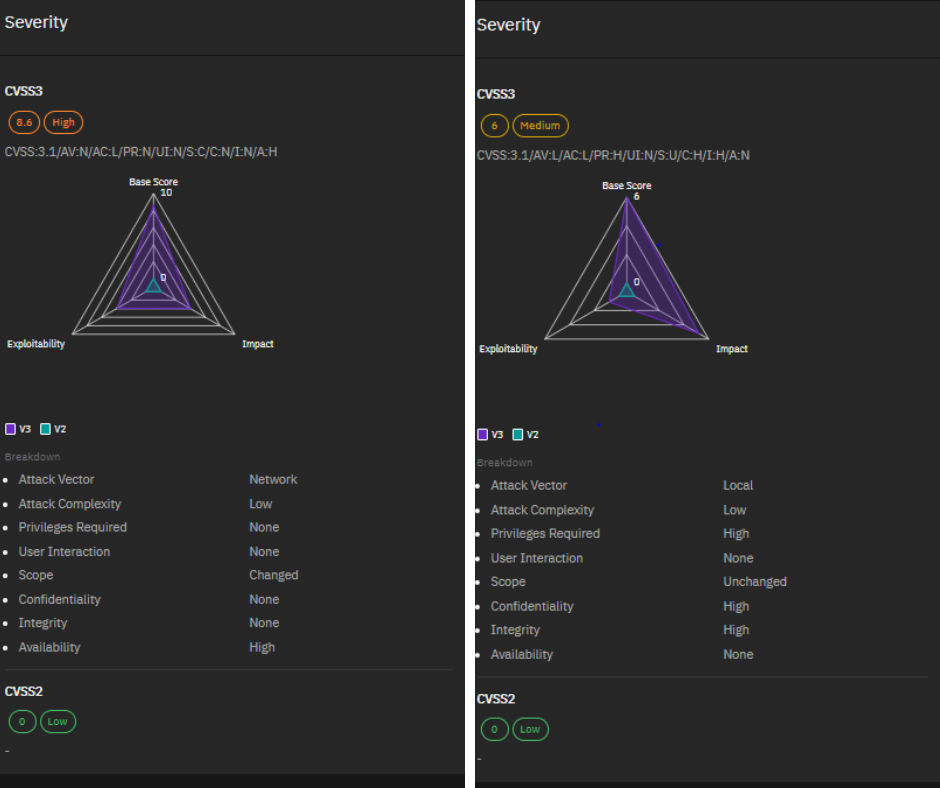
CVE-2024-26234 and CVE-2024-29988: Microsoft’s April 2024 Update Under Fire
CVE-2024-26234 and CVE-2024-29988 are two vulnerabilities that Microsoft patched in their April 2024 security update. Both of these were zero-day vulnerabilities, meaning they were exploited in attacks before a fix was available.
- CVE-2024-26234: This vulnerability is called a “proxy driver spoofing vulnerability”. In simple terms, it allowed attackers to trick your system into trusting a malicious driver program. This could potentially allow them to take control of your device.
- CVE-2024-29988: This vulnerability is described as a bypass for another vulnerability (CVE-2024-21412). It allowed attackers to bypass a security feature in Windows called Mark of the Web (MotW). MotW is designed to warn users before they open files downloaded from the internet. By bypassing this feature, attackers could deploy malware more easily.
Both of these vulnerabilities were critical because they were being actively exploited by attackers. This highlights the importance of keeping your software up to date with the latest security patches.
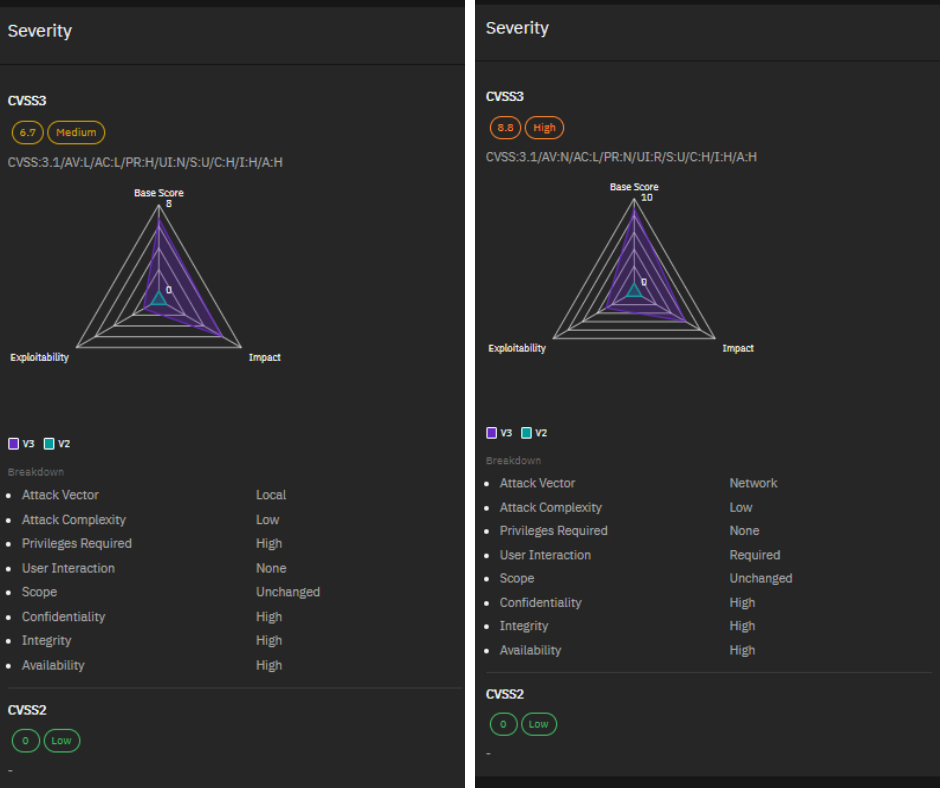
CVE-2024-3400: Critical Vulnerability in Palo Alto Networks PAN-OS
CVE-2024-3400 is a critical vulnerability in Palo Alto Networks PAN-OS, a software suite that powers their firewall appliances. It was disclosed on April 12, 2024 and allows unauthenticated attackers to take complete control (root privileges) of affected firewall devices.
Here’s a breakdown of the key points:
- CVE ID: CVE-2024-3400
- Vendor: Palo Alto Networks
- Product: PAN-OS
- Impact: Unauthenticated attackers can potentially execute arbitrary code with root privileges on the firewall
- Disclosure Date: April 12, 2024
While details about the exact vulnerability are not publicly available, Palo Alto Networks is aware of targeted attacks leveraging this flaw, and proof-of-concept exploit code is circulating. They’ve released a security advisory and patches to address this vulnerability.
If you are using PAN-OS, it is critical that you update your systems as soon as possible to mitigate this risk.
Final Words
April 2024 kept cybersecurity professionals on their toes. New vulnerabilities emerged throughout the month, highlighting the importance of staying informed and proactive. By keeping software updated and adhering to security best practices, organizations can significantly reduce their risk profile.
If you have any questions or concerns, please don’t hesitate to reach out to the security community. Together, we can build a more secure digital world.
Until next time, stay safe!
The post A Closer Look at Top 5 Vulnerabilities of April 2024 appeared first on Strobes Security.
*** This is a Security Bloggers Network syndicated blog from Strobes Security authored by Shubham Jha. Read the original post at: https://strobes.co/blog/a-closer-look-at-top-5-vulnerabilities-of-april-2024/
Original Post URL: https://securityboulevard.com/2024/05/a-closer-look-at-top-5-vulnerabilities-of-april-2024/
Category & Tags: Security Bloggers Network,Vulnerabilities,Top CVE Vulnerabilties,Top Vulnerabilities,vulnerability intelligence,Vulnerability Management,vulnerability prioritization – Security Bloggers Network,Vulnerabilities,Top CVE Vulnerabilties,Top Vulnerabilities,vulnerability intelligence,Vulnerability Management,vulnerability prioritization
Views: 3