Source: www.darkreading.com – Author: 1
Many security professionals today associate the Dark Web with named leaks, which are leaked credentials from employee password reuse. This is still a relevant threat; in the last six years, the Flare platform has counted over 12 billion leaked credentials. The Dark Web is rapidly growing along with the variety of cybercrime. So is the value in monitoring it.
The cybercrime ecosystem now not only includes private communications platforms like I2P and Tor but also reaches across clear websites and Telegram channels.
Dark Web Monitoring: What to Watch For
There is tangible value in monitoring the Dark Web for potential risks. Following are some of the threats you might encounter.
Infostealer Malware
Stealer logs with corporate access are likely one of the most significant vectors for data breaches and ransomware attacks today.
Infostealer variants such as RedLine, Raccoon, Vidar, Titan, and Aurora infect computers, then exfiltrate the browser fingerprint containing all the saved passwords in the browser. Threat actors then sell the results on Dark Web marketplaces or Telegram channels.
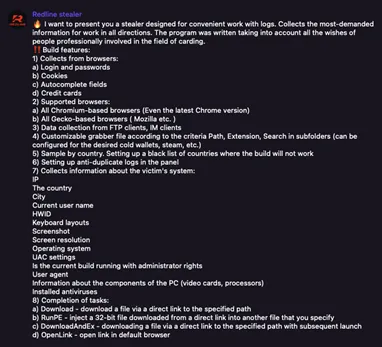
These logs are then used for account takeover attacks, stealing cryptocurrency, or as initial access for ransomware attacks. Flare monitors more than 20 million infostealer logs and is adding 1 million new logs per month, many of which contain credentials to multiple corporate applications. We believe that somewhere between 2% and 4% of logs contain access to corporate IT environments that could pose significant risk if compromised.
To detect malicious actors distributing stealer logs across the Dark Web and Telegram, companies can monitor for any logs that contain an internal corporate domain access, such as sso.companyname.com.
Initial Access Brokers
Initial access brokers (IABs) are active across Dark Web forums, such as XSS and Exploit.in. IABs establish initial access to companies, which they resell in auction and forum threads, typically for $10,000 to $500,000 per listing, depending on the company and level of access. A listing usually contains:
- Number of devices and services compromised
- Industry of the victim company
- Antivirus or endpoint detection and response platform the company is using
- Company revenue
- Number of employees
- Geographic location of company
- Compromised hosts or servers
Threat actors can purchase this access and use it to deploy ransomware or steal sensitive data or financial resources.
Monitoring IAB forums can provide early warning that malicious actors have compromised devices. IABs never list the exact company name but generally provide enough detail that if your organization is a victim, there is a reasonable chance you can identify it.
IABs are also deliberately seeking out stealer logs to gain access to IT infrastructure. An IAB may purchase an infected device for $10 from Russian Market, use the credentials to gain access, escalate privileges, then list the access for sale on Exploit.in with bids starting at $20,000.
Ransomware Extortion and Data Breach Pages
Ransomware isn’t what it used to be. Ransomware groups are becoming decentralized, with many groups providing the source code for ransomware and handing off the work of infecting companies out to affiliates for a cut of the ransom payment. In addition, the ubiquity of backup and recovery solutions has caused many groups to entirely ditch encryption and instead focus on data exfiltration tactics involving data theft and disclosure, targeting individual employees, or targeting third parties of the victim organization,
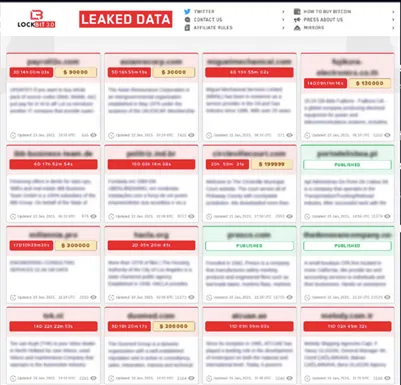
Another disturbing trend in the cybercriminal underground is ransomware extortion and data breach blogs. Threat actors use these blogs to publicly shame and extort victims by threatening to leak sensitive data if they do not pay ransom. This tactic has proven to be highly effective, as organizations fear the potential legal and reputational consequences that could arise from a data breach.
In addition, some groups will release files in batches, add timers counting down to releasing sensitive data, and target individual employees to increase pressure.
As a result, many victims opt to pay the ransom, perpetuating the cycle of cybercrime and incentivizing further attacks.
Your organization would likely know if it was a victim of ransomware; however, many organizations suffer data exposure due to third-party breaches.
By proactively monitoring ransomware blogs such as LockBit, you can detect unwanted data exposure from third parties and rapidly begin incident response procedures.
Detect Dark Web Threats
It’s crucial for organizations to be able to detect threats across the clear and Dark Web and illicit Telegram channels. Look for a solution that integrates easily into your security program and provides advanced notice of potential high-risk exposure in a single platform.
You want to identify high-risk vectors that could enable threat actors to access your environment and conduct continuous monitoring for infected devices, ransomware exposure, public GitHub secrets, leaked credentials, and more.
To learn more about using Flare to detect Dark Web threats, sign up for a free trial.
About the Author:

Eric Clay has experience across governance risk and compliance, security data analysis, and security research. He currently works as the VP of marketing at Flare, a Threat Exposure Management SaaS solution.
Original Post URL: https://www.darkreading.com/threat-intelligence/the-dark-web-is-expanding-as-is-the-value-of-monitoring-it
Category & Tags: –
Views: 1




















































