Source: securityboulevard.com – Author: Max Aulakh
A lot goes into protecting the information security of the nation. The National Institute of Standards and Technology, NIST, maintains a list of security controls under the banner of NIST SP 800-53, Security and Privacy Controls for Information Systems and Organizations. Meanwhile, the Federal Risk and Authorization Management Program, or FedRAMP, sets up a framework that makes those security controls apply to governmental agencies and the third-party cloud service providers that work with them.
If you’re a CSP looking to work with the federal government in some capacity, and you will need to handle Controlled Unclassified Information (or CUI), you will need to apply for a FedRAMP Authority to Operate or ATO with your chosen agency.
Along with adhering to the standards set forth in the FedRAMP security levels, as based on the NIST security controls list, you will need to go through both ConMon and Audits to achieve your ATO and begin working with the government. The question is, what are those two elements of FedRAMP, how do you handle them, and which is more important? Let’s dig in.
FedRAMP in Brief
First, let’s go through a very brief rundown of what FedRAMP is and why it’s important.
FedRAMP is the Federal Risk and Authorization Management Program. It was designed to help the government avoid having to “reinvent the wheel” when it comes to digital services that handle potentially sensitive information. For example, why should the government create its own cloud storage when something like Google Drive exists? The same goes for office apps; why engineer their own version of a word processor when MS Word or Google Docs exist?
FedRAMP exists to help avoid a situation where the government needs its own proprietary versions of common apps, along with alleviating the need for the development and maintenance of those apps.
Of course, using one of those platforms without assurance in place is a security risk. Any data breach or backdoor in those services could jeopardize the security of government information processed using those apps.

FedRAMP exists as a framework that the cloud service provider (like Google, Microsoft, or any of hundreds of others) can use to secure their platform for government use. Larger companies like Google create “Google for Government” branches of their apps, while smaller CSPs might simply secure their offering in its entirety, allowing the private sector to benefit from the enhanced security along the way.
The process for achieving FedRAMP compliance and receiving an Authority to Operate is lengthy and complex.
- The CSP must pick a government agency to work with, obtaining an agency sponsor, or pursue a Provisional Authority to Operate with the Joint Assessment Board that applies to all agencies.
- The CSP must determine what level of FedRAMP security (low, moderate, high) will apply to them. This includes a FIPS 199 assessment.
- The CSP must work to identify all relevant security controls and ensure their implementation throughout the organization.
- The CSP must have an audit performed by a C3PAO to assess adherence to those security controls.
- The CSP must implement ConMon to ensure ongoing adherence to FedRAMP security requirements.
- The CSP must create a Plan of Action & Milestones to patch any gaps in compliance ASAP.
- The CSP must undergo regular audits to validate ongoing security.
There’s a lot more detail and nuance to this than we’re conveying here, but that’s because it’s not really the point of this post. If you want a more thorough rundown, we have other guides and are more than happy to answer questions directly if you want to contact us.
Two important elements of this process are ConMon and Audits. They’re both critical, but what are they?
FedRAMP ConMon: Purpose and Practice
ConMon is short for Continuous Monitoring. It’s a process you establish as part of gaining an ATO. The goal is exactly what the name implies: to have an established and tested system for reviewing your security posture, watching for signs of intrusion or gaps in coverage, and fixing them when they arise.
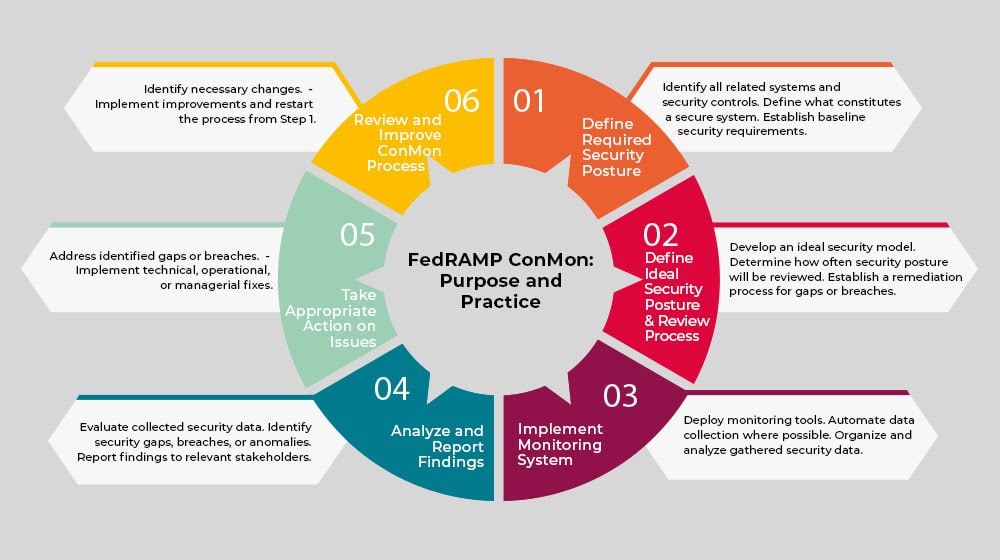
FedRAMP ConMon is a six-step process.
- Define your required security posture across all related systems and security controls. It’s impossible to know if you’re secure if you don’t know what secure means or what is supposed to be secure, after all.
- Define your ideal security posture and a process for checking to see if you’ve maintained it. This also needs to include how often the process is checked and how, as well as how to address gaps or breaches.
- Implement your monitoring system in a way that allows you to see, collect, organize, and analyze the information you gather about it. This is, ideally, as automated as possible to remove human error and influence from the equation.
- Analyze the reports you’re given and report those results to stakeholders. Monitoring doesn’t do you any good if there aren’t eyes to see the results, right?
- Take appropriate action when a gap or breach is discovered. This could be technical, operational, or managerial, but it needs to address the issue and find a way to prevent it from happening again, if possible.
- Review your overall analysis and identify anything in the overall ConMon process that needs to be changed. Implement those changes and return to steps one and two to repeat the process.
The overall purpose of continuous monitoring is to ensure ongoing security. Threats, threat vectors, software security, and more all change on a regular basis, and there’s no such thing as a perfectly secure system. Continuous monitoring helps ensure that you maintain valid security in the wake of changing threats, identify holes before they become problems, and react to problems when they occur.
FedRAMP Audits: Purpose and Practice
You can spend a year establishing every possible piece of security you can in adherence to the strictest standards of information security in the NIST and FedRAMP rulebook, but how is anyone else going to trust that you’ve done so? If all you have is some paperwork and your word, there’s no inherent reason to trust you.
In fact, the only way to validate your security posture is to review it directly. Whether that’s a line-by-line review of every single security control across every single system or a statistical sampling of systems across a much larger organization, it requires an expert to be able to go through the details and assess whether they’re properly implemented or not.
That’s where the 3PAO comes into play. 3PAOs are Third Party Assessment Organizations. These are companies like ourselves that are deeply familiar with everything it takes to gain FedRAMP authorization and who can review the documentation and systems of an aspiring FedRAMP CSP.
Generally, since CSPs are large and sprawling enough that it’s not feasible to go through everything manually, a FedRAMP audit will take the analysis reports from your continuous monitoring, along with first-hand harvested data and testing results, to check your overall security posture.

A thorough FedRAMP audit is required in order to validate the CSP’s security, and a readiness report will be created and submitted to the Joint Authorization Board, which will make the final determination of whether to approve or deny the CSP’s authority to operate. If denied, they can fix the problems and try again, and if approved, they can begin a government contract and continue to maintain their security.
While systems like CMMC require a full recertification every three years, FedRAMP does not. Instead, FedRAMP requires valid ConMon to be implemented, and an annual review of that ConMon and security posture, usually referred to as an audit. A failed audit means a failed ConMon and can cause a CSP to have its ATO revoked.
Expounding on the Difference: ConMon vs Audits
While the differences between ConMon and audits should be clear, it’s worth taking a moment to dig right in.
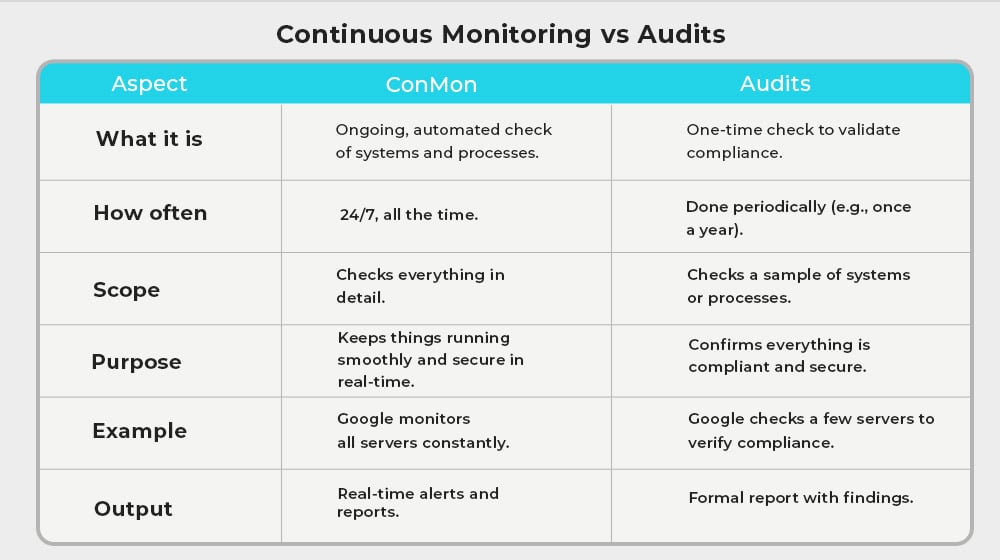
ConMon is sort of like an ongoing, automated, distilled auditing process for your entire business. Audits are one-time events that validate your security posture.
One key is that ConMon generally needs to be thorough. It has to review every system, every process, and every communication to make sure it adheres to your standards. Audits don’t have to go down every single line item in your inventory because, with a large enough company, that could take years on its own. It’s allowed to do two things to shortcut the process. The first is to trust and rely on the documentation from ConMon, and the second is to use statistical sampling for large, otherwise identical systems.
For example, Google doesn’t need every server in their data center to be individually reviewed since entire groups of them are functionally identical; all they need is a sampling of those systems, along with the results of monitoring on all of them.
Which is More Important: ConMon or Audits?
It’s impossible to say that one of these is more important than the other because they’re two parts of the same overall process. Without one of them, your ability to achieve FedRAMP compliance is jeopardized, and you can’t receive an ATO.

Some might say the audit is more important because the third-party assessment needs to be completed, the readiness report generated, and the results evaluated by the Program Management Office before an ATO can be granted or maintained. ConMon is a required part of FedRAMP compliance and is mandatory for passing that audit.
It is, however, technically possible to operate in a secure way as a CSP using just ConMon without ever undergoing an audit. The distinction is that, without the audit, you can’t work with the government. You can still be secure enough to do so, but you can’t actually gain authorization.
How to Navigate FedRAMP ConMon and Auditing Successfully
For any CSP looking to achieve FedRAMP Authority to Operate (or a Provisional Authority to Operate), how do you go about navigating the process?
Seek agency sponsorship. There’s very little point to a CSP going through the work to achieve FedRAMP qualifications without having an agency in mind to work with. An agency sponsor essentially sets up a provisional contract saying, “Yes, we’re willing to use your service once you’re authorized.”
A Provisional Authority to Operate exists for services that are large and generic enough to apply to the whole of the government, something like an Office Productivity Suite. Rather than get a new ATO for each agency, they can get a P-ATO to allow any agency to pick up a contract without having to re-validate security.

Implement your necessary security. Once you know who you’re working with, what kind of information you’d be handling, and what the risks are, you can perform a FIPS 199 assessment to determine what level of security you need. Then, you can go through the relevant security controls and implement them one by one. This is also a good point to establish ways to monitor those controls along the way so you don’t have to retrofit ConMon down the line.
Work with a certified third-party assessment organization. C3PAOs like Ignyte allow you to leverage their experience and knowledge to speed up and streamline the FedRAMP process.
Here at Ignyte, we have several different ways we can help. In addition to being able to answer your questions directly or through our reference blog, we are a certified 3PAO and can provide the auditing and readiness report services you need to be able to pass and gain your ATO.
You can also use the Ignyte Assurance Platform. This is our custom-designed app that helps streamline your ConMon in a collaborative and centralized platform, providing machine-readable outputs for your results and easy adherence to auditing and compliance rules. We can help with automated POA&Ms as well.
With over a thousand audits performed and over 100 accepted ATOs, Ignyte can be your biggest source of strength in ensuring you make it through the process as quickly and effectively as possible. All you need to do to get started is reach out and request a demo today. We’re standing by and ready to work with you whenever you’re ready.
*** This is a Security Bloggers Network syndicated blog from Ignyte authored by Max Aulakh. Read the original post at: https://www.ignyteplatform.com/blog/fedramp/fedramp-conmon-audits-difference/
Original Post URL: https://securityboulevard.com/2025/02/fedramp-conmon-vs-audits-whats-the-difference/
Category & Tags: Security Bloggers Network,FedRAMP – Security Bloggers Network,FedRAMP
Views: 1






















































