Source: hackread.com – Author: Waqas.
Eight Android apps on the Google Play Store, downloaded by millions, contain the Android.FakeApp trojan, stealing user data – Here’s the complete list, delete the NOW!
Russian cybersecurity firm Dr. Web has exposed several Android apps on the Google Play Store that contain a sophisticated trojan, Android.FakeApp.1669 (also known as Android/FakeApp).
These apps, which claim to provide practical functions like financial tools, planners, and recipe books; contain a hidden payload that redirects users to unwanted websites, compromising their data. What’s worse, more than 2 million users have downloaded these infected apps from Google Play, unaware of the threat.
Malware on the official Google Play Store is nothing new. In fact, reports from last month indicate a rise in malicious apps on both the Apple App Store and Google Play Store.
Android.FakeApp.1669
Android.FakeApp.1669 is part of the Android.FakeApp trojan family, a group of malware that usually redirects users to different websites, disguised as legitimate apps. However, this variant is especially notable due to its reliance on a modified dnsjava library that allows it to receive commands from a malicious DNS server, which, in turn, supplies a target link. Rather than the app’s advertised function, this target link is displayed on the user’s screen, often pretending to be an online casino or an unrelated website.
According to Dr. Web’s report, the malware activates only under specific conditions. If the infected device is connected to the Internet through designated mobile data providers, the DNS server will send a configuration to the app, containing a link that loads within the app’s WebView interface. When not connected to targeted networks, the app functions as expected, making detection difficult for users.
In January 2018, the Android.FakeApp trojan was first discovered in a fake Uber app for Android. Later, in March 2018, the same malware targeted Facebook users to steal data. In May 2020, a fake mobile version of the game Valorant was spreading the Android.FakeApp trojan just as the official version was set to release that summer.
Infected Apps and Download Counts
These apps claimed to be useful tools, from personal finance and productivity applications to cooking and recipe collections. However, once launched, the apps would connect to the DNS server to retrieve a configuration containing the website link to display.
Dr. Web’s investigation revealed several apps on the Google Play Store, some with high download counts, infected by Android.FakeApp.1669. While Google has removed some of these apps, millions of users had already installed them before the removal. Below is a list of apps identified by Dr. Web’s malware analysts, with their respective download counts:
| App Name | Number of Downloads |
|---|---|
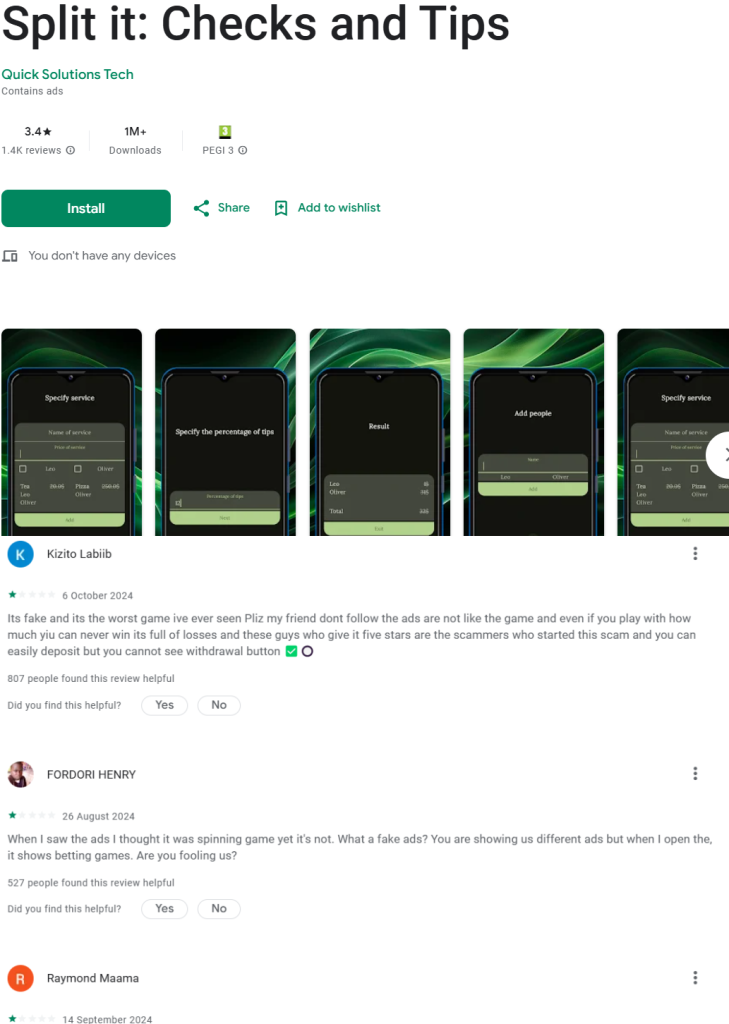
| Split it: Checks and Tips | 1,000,000+ (On Google Play at the time of writing) |
| FlashPage parser | 500,000+ (On Google Play at the time of writing) |
| BeYummy – your cookbook | 100,000+ (On Google Play at the time of writing) |
| Memogen | 100,000+ (Deleted) |
| Display Moving Message | 100,000+ (On Google Play at the time of writing) |
| WordCount | 100,000+ (On Google Play at the time of writing) |
| Goal Achievement Planner | 100,000+ (On Google Play at the time of writing) |
| DualText Compare | 100,000+ (On Google Play at the time of writing) |
| Travel Memo | 100,000+ (Deleted) |
| DessertDreams Recipes | 50,000+ (On Google Play at the time of writing) |
| Score Time | 10,000+ (Deleted) |
How Android.FakeApp.1669 Operates
Once downloaded, the trojan gathers specific data from the user’s device, such as:
- Screen size
- Device model and brand
- Battery charge percentage
- Developer settings status
- Device ID, which includes the installation time and a random number.
This data, coded into a unique sub-domain name, allows the server to customize its response to each infected device. When the device meets the connection criteria, Android.FakeApp.1669 retrieves and decrypts data from the DNS server, eventually loading a link that redirects to an unwanted website, typically an online casino.
The decryption process involves reversing and decoding Base64 data and decompressing it, revealing sensitive configuration details.
Recommendations for Users
Given the high download count, Android users should take immediate steps to protect themselves. First, it’s crucial to delete any infected apps. Uninstall any app from the list provided or other similar apps that display suspicious behaviour to minimize potential security risks.
Additionally, read the comments on these apps; many users have left negative reviews, noting that the apps spam ads and cause their devices to freeze, a behaviour that allows the malware to operate in the background.
Next, use trusted security software, regularly checking app permissions is another vital step. Users should review the permissions requested by apps, avoiding any unnecessary access that could compromise device security. Additionally, updating both the device and applications frequently can help prevent certain types of malware infections, as updates often include important security patches.
Nevertheless, download with caution, even when using official sources like Google Play. Reviewing app permissions and reading user feedback before downloading can help spot potential red flags and avoid risky apps.
Hackread.com has reached out to Google, and this article will be updated with any new developments or if Google removes the app. Stay tuned.
Original Post url: https://hackread.com/google-play-store-apps-android-fakeapp-trojan/
Category & Tags: Security,Android,Malware,Cybersecurity,Google,Play Store,TROJAN – Security,Android,Malware,Cybersecurity,Google,Play Store,TROJAN
Views: 0




















































