Source: securityboulevard.com – Author: Amy Cohn Why is Smart Machine Identity Management Crucial? What comes to your mind when you think about cybersecurity? Most often, we...
Year: 2025
Crafting Impenetrable Defenses for Your NHIs – Source: securityboulevard.com
Source: securityboulevard.com – Author: Amy Cohn Why the Buzz about Impenetrable NHIs? You might have heard quite the buzz around impenetrable Non-Human Identities (NHIs). It’s the...
Optimistic About the Future of Secrets Vaulting? – Source: securityboulevard.com
Source: securityboulevard.com – Author: Amy Cohn Are You Ready to Embrace the Future of Secrets Vaulting? I often get asked: “What does the future hold for...
BSidesLV24 – HireGround – Tracking And Hacking Your Career – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman Home » Security Bloggers Network » BSidesLV24 – HireGround – Tracking And Hacking Your Career Authors/Presenters: Misha Yalavarthy, Leif Dreizler...
Speaking the Board’s Language: A CISO’s Guide to Securing Cybersecurity Budget – Source: securityboulevard.com
Source: securityboulevard.com – Author: David Meese Budget season is a defining moment for chief information security officers (CISOs). It’s the time when security leaders must make...
Trump EO Presses States to Bear the Weight of CI Resilience – Source: securityboulevard.com
Source: securityboulevard.com – Author: Teri Robinson Even as he aggressively moves to amass power in the executive, President Trump has made no secret his desire to...
20+ RSAC Things (and Places) You Should Know – Source: securityboulevard.com
Source: securityboulevard.com – Author: Shriram Sharma RSA Conference (RSAC) is one of the largest cybersecurity gatherings in the world, and our team at D3 Security is...
Friday Squid Blogging: Two-Man Giant Squid – Source: www.schneier.com
Source: www.schneier.com – Author: Bruce Schneier HomeBlog Comments ResearcherZero • April 5, 2025 12:43 AM Services and networks that transmit weather and climate information may be...
Troy Hunt Gets Phished – Source: www.schneier.com
Source: www.schneier.com – Author: Bruce Schneier HomeBlog Comments Winter • April 4, 2025 12:03 PM @ideho “justice” “my oh my, the guy says: “they don’t provide...
Cyber agencies urge organizations to collaborate to stop fast flux DNS attacks – Source: www.csoonline.com
Source: www.csoonline.com – Author: They call the tactic a ‘national security threat’ and a ‘defensive gap in many networks.’ IT leaders in governments, critical infrastructure providers,...
Ivanti warns customers of new critical flaw exploited in the wild – Source: www.csoonline.com
Source: www.csoonline.com – Author: Chinese APT group UNC5221 appears to have studied a recent Ivanti Connect Secure patch to develop a remote code execution exploit on...
Royal Mail investigates data leak – Source: www.csoonline.com
Source: www.csoonline.com – Author: Several gigabytes of sensitive customer data have surfaced on the darknet, allegedly from the British postal service Royal Mail. There are indications...
Big hole in big data: Critical deserialization bug in Apache Parquet allows RCE – Source: www.csoonline.com
Source: www.csoonline.com – Author: Successful exploitation could allow attackers to steal data, install malware, or take full control over affected big data systems. A flaw in...
Trump fires NSA and Cybercom chief, jeopardizing cyber intel – Source: www.csoonline.com
Source: www.csoonline.com – Author: Lawmakers fear the firing of Gen. Timothy Haugh will lead to a loss of critical intelligence at a time when cyber threats...
Royal Mail untersucht Datenleck – Source: www.csoonline.com
Source: www.csoonline.com – Author: Im Darknet sind mehrere Gigabyte sensible Kundendaten aufgetaucht, die von der britischen Post Royal Mail stammen sollen. Der britische Postdienst Royal Mail...
The Future Is Femtech
Femtech is short for “female technology,” and encompasses the technology, companies, and services that focus on the unique health care needs of females. Source Views: 1
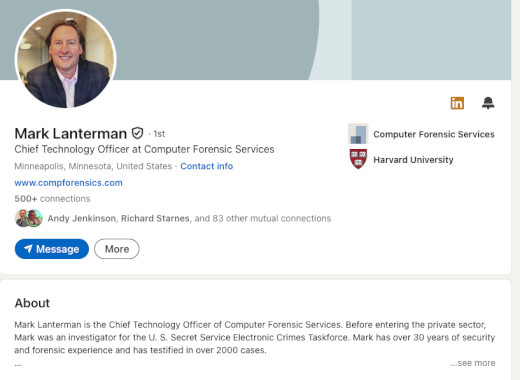
Cyber Forensic Expert in 2,000+ Cases Faces FBI Probe – Source: krebsonsecurity.com
Source: krebsonsecurity.com – Author: BrianKrebs A Minnesota cybersecurity and computer forensics expert whose testimony has featured in thousands of courtroom trials over the past 30 years...
DDoS Attacks Now Key Weapons in Geopolitical Conflicts, NETSCOUT Warns – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: Aminu Abdullahi Published April 4, 2025 We may earn from vendors via affiliate links or sponsorships. This might affect product placement on...
Benchmarks Find ‘DeepSeek-V3-0324 Is More Vulnerable Than Qwen2.5-Max’ – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: J.R. Johnivan Topic — Artificial Intelligence Published April 4, 2025 We may earn from vendors via affiliate links or sponsorships. This might...
Windows 11 Forces Microsoft Account Sign In & Removes Bypass Trick Option – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: Aminu Abdullahi Published April 4, 2025 We may earn from vendors via affiliate links or sponsorships. This might affect product placement on...
North Korean Hackers Disguised as IT Workers Targeting UK, European Companies, Google Finds – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: Fiona Jackson Image: DC_Studio/Envato North Korean hackers who disguise themselves as IT workers are applying for work in the U.K., according to...
Google DeepMind Proposes AI ‘Monitors’ to Police Hyperintelligent Models – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: Megan Crouse Topic — Artificial Intelligence Published April 3, 2025 DeepMind’s approach to AGI safety and security splits threats into four categories....
Are You Certain Your Secrets Are Safe? – Source: securityboulevard.com
Source: securityboulevard.com – Author: Amy Cohn Is Your Organization Fully Protected Against Security Breaches? Non-Human Identities (NHIs) have emerged as key players in fortifying the security...
Satisfied with Your NHI Lifecycle Management? – Source: securityboulevard.com
Source: securityboulevard.com – Author: Amy Cohn Is Your NHI Lifecycle Management Really Satisfying Your Security Needs? I invite you to ponder this question: Is your Non-Human...
How NHIs Can Deliver Real Business Value – Source: securityboulevard.com
Source: securityboulevard.com – Author: Amy Cohn Are NHIs the Unsung Heroes of Cybersecurity? It’s no secret that cybersecurity is a top priority for organizations, but did...
DMARC Adoption in U.S. and Canada Higher Education Sector – Source: securityboulevard.com
Source: securityboulevard.com – Author: Fred Bianchi Phishing attacks are an immediate and growing threat to higher education institutions where sensitive data and susceptible audiences are targeted...
Cloud Native Security: How to Protect Your Kubernetes Infrastructure – Source: securityboulevard.com
Source: securityboulevard.com – Author: Brian Bensky As organizations increasingly adopt cloud-native technologies, securing Kubernetes infrastructure has become more important than ever. Cloud-native security encompasses practices and...
BSidesLV24 – HireGround – What Goes Bump in the Night? Recruiter Panel About Job Search and Other Scary Things – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman Home » Security Bloggers Network » BSidesLV24 – HireGround – What Goes Bump in the Night? Recruiter Panel About Job...
Hunters International Dumps Ransomware, Goes Full-on Extortion – Source: securityboulevard.com
Source: securityboulevard.com – Author: Jeffrey Burt Ransomware groups over the past few years have been running double-extortion campaigns, not only encrypting the data of targeted organizations...
CMMC Level 2 Documentation: What Auditors Want to See – Source: securityboulevard.com
Source: securityboulevard.com – Author: Max Aulakh If you’re part of the defense industrial base and you’re seeking CMMC certification, there’s a very good chance you’re aiming...