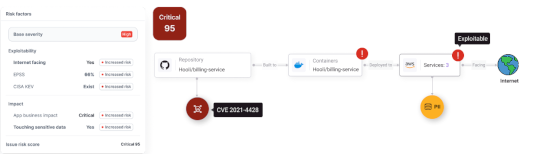
Source: socprime.com – Author: Daryna Olyniychuk Following the disclosure of the Command Center CVE-2025-34028 vulnerability, researchers are now warning about another critical threat: a max-severity flaw...
Year: 2025
‘Source of data’: are electric cars vulnerable to cyber spies and hackers? – Source: www.theguardian.com
Source: www.theguardian.com – Author: Dan Milmo Global technology editor Mobile phones and desktop computers are longstanding targets for cyber spies – but how vulnerable are electric...
SWE Community Spotlight: Public Policy Affinity Group Member Spotlight
Each month throughout the year, we’ll be spotlighting our SWE Affinity Groups. Here, the Public Policy Affinity Group shares the story of one of their active...
Meet the 2023 WE Local Barcelona Keynotes
Get to know the leaders who will be sharing their stories in Barcelona! Source Views: 2
How to Utilize the Leadership Coaching Committee
The Leadership Coaching Committee (LCC) is a trained group of more than 70 experienced SWE members who work with section, Members at Large (MALs), and affiliate...
SWE Community Spotlight: Public Policy Affinity Group Overview
Each month throughout the year, we’ll be spotlighting our SWE Affinity Groups. This month, we are excited to highlight the Public Policy Affinity Group. Source Views:...
Explore STEM Pathways Digital Library Now!
Learn about the different engineering pathways that you can pursue as a career. With so many different fields in STEM to explore, it can be difficult...
As a section officer, accuracy and transparency are key…
Section officers have taken on roles with responsibilities. For many, this is the first time they are responsible for decisions and control of communal finances. The...
Community Colleges Affinity Group Spotlight: the Community College Dream
Each month throughout the year, we’ll be spotlighting our SWE Affinity Groups. This month, we are excited to highlight the Community Colleges Affinity Group. Source Views:...
SWE Mentor Network is now welcoming all Community College Students!
The SWE Mentor Network is a virtual platform that helps facilitate mentoring conversations during 1-2 week cohorts scheduled throughout the year. SWE members at all levels...
Uyghur Diaspora Group Targeted with Remote Surveillance Malware – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: Written by Several representatives of exiled Uyghurs have been targeted by a pervasive spear phishing campaign aimed at deploying surveillance malware, researchers...
Half of Mobile Devices Run Outdated Operating Systems – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: Half of all mobile devices are operating on outdated operating systems, leaving them highly vulnerable to cyber-attacks, according to new research. The...
Researchers Note 16.7% Increase in Automated Scanning Activity – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: A surge in automated scanning activity, increasing by 16.7% globally in 2024, has exposed massive vulnerabilities in digital infrastructure. According to the...
IBM aims for autonomous security operations – Source: www.networkworld.com
Source: www.networkworld.com – Author: News Apr 28, 20254 mins High-Performance ComputingMainframesSecurity Information and Event Management Software IBM also pledged to invest $150 billion in the U.S....
Cisco automates AI-driven security across enterprise networks – Source: www.networkworld.com
Source: www.networkworld.com – Author: At RSA Conference 2025, Cisco unveiled agentic AI capabilities in Cisco XDR, the latest version of Splunk SOAR, and an open-source AI...
AI looms large on the RSA Conference agenda – Source: www.csoonline.com
Source: www.csoonline.com – Author: Expect artificial intelligence to be the topic of the week at the RSA Conference, with a slew of product announcements, panel discussions,...
Secure by Design is likely dead at CISA. Will the private sector make good on its pledge? – Source: www.csoonline.com
Source: www.csoonline.com – Author: News Analysis Apr 28, 20256 mins GovernmentRegulationTechnology Industry CISA’s high-profile proselytizing of its Secure by Design program will likely end, but some...
4 big mistakes you’re probably still making in vulnerability management…and how to fix them – Source: www.csoonline.com
Source: www.csoonline.com – Author: BrandPost By Action 1 Apr 28, 20254 mins Vulnerability management isn’t about checking boxes anymore—it’s about real-time visibility, risk prioritization, and automation...
Compliance Challenges in Cloud Data Governance – Source: securityboulevard.com
Source: securityboulevard.com – Author: Devin Partida Adopting cloud computing allows organizations of all shapes and sizes to access data and collaborate in the most flexible ways...
RSA Conference Dispatch: Mr. NHI – Leading the Movement to Expose Cybersecurity’s Biggest Blind Spot! – Source: securityboulevard.com
Source: securityboulevard.com – Author: John D. Boyle When you meet Lalit Choda, known across the cybersecurity industry as “Mr. NHI,” one word immediately comes to mind:...
Announcing New Legit ASPM AI Capabilities – Source: securityboulevard.com
Source: securityboulevard.com – Author: Liav Caspi Get details on Legit’s new AI capabilities. Developers are increasingly leveraging AI to build faster and smarter. Its use has...
News alert: Case dismissed against VPN executive, affirms no-logs policy as a valid legal defense – Source: securityboulevard.com
Source: securityboulevard.com – Author: cybernewswire Toronto, Canada, Apr. 28, 2025, CyberNewswire — Windscribe, a globally used privacy-first VPN service, announced today that its founder, Yegor Sak,...
Your NHIDR Is Getting Better—How? – Source: securityboulevard.com
Source: securityboulevard.com – Author: Alison Mack Why Does Improving Non-Human Identity and Data Response (NHIDR) Matter? How often do we consider the impact of Non-Human Identities...
Harnessing Powerful Tools for Secrets Scanning – Source: securityboulevard.com
Source: securityboulevard.com – Author: Amy Cohn Capturing the Essence of Powerful Secrets Scanning Wondering how to enhance your organization’s cybersecurity measures? Among the vast spectrum of...
Certain Your Data Is Safe in the Cloud? – Source: securityboulevard.com
Source: securityboulevard.com – Author: Amy Cohn Are You Confident Your Data Safety Measures Are Up to Scratch? The rise of digital transformation is not without its...
BSidesLV24 – Ground Truth – PhishDefend: A Reinforcement Learning Framework – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman Home » Security Bloggers Network » BSidesLV24 – Ground Truth – PhishDefend: A Reinforcement Learning Framework Author/Presenter: Bobby Filar Our...
Bugcrowd Launches Red Team Service to Test Cybersecurity Defenses – Source: securityboulevard.com
Source: securityboulevard.com – Author: Michael Vizard Bugcrowd today at the 2025 RSA Conference announced its intent to create a red team service to test cybersecurity defenses...
Blackpoint Cyber Extends MDR Service to Improve Cyber Resiliency – Source: securityboulevard.com
Source: securityboulevard.com – Author: Michael Vizard Blackpoint Cyber today at the 2025 RSA Conference unveiled a unified security posture and response platform that is based on...
African Telecom Giant MTN Group Discloses Data Breach – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ionut Arghire MTN Group, one of the largest telecommunications services providers in Africa, says the personal information of some customers was compromised...
News alert: Case dismissed against VPN executive, affirms no-logs policy as a valid legal defense – Source: www.lastwatchdog.com
Source: www.lastwatchdog.com – Author: cybernewswire Toronto, Canada, Apr. 28, 2025, CyberNewswire — Windscribe, a globally used privacy-first VPN service, announced today that its founder, Yegor Sak,...