Source: krebsonsecurity.com – Author: BrianKrebs Microsoft Corp. today issued security updates to fix more than 80 vulnerabilities in its Windows operating systems and software. There are...
Day: September 9, 2025
18 Popular Code Packages Hacked, Rigged to Steal Crypto – Source: krebsonsecurity.com
Source: krebsonsecurity.com – Author: BrianKrebs At least 18 popular JavaScript code packages that are collectively downloaded more than two billion times each week were briefly compromised...
Axios Abuse and Salty 2FA Kits Fuel Advanced Microsoft 365 Phishing Attacks – Source:thehackernews.com
Source: thehackernews.com – Author: . Threat actors are abusing HTTP client tools like Axios in conjunction with Microsoft’s Direct Send feature to form a “highly efficient...
RatOn Android Malware Detected With NFC Relay and ATS Banking Fraud Capabilities – Source:thehackernews.com
Source: thehackernews.com – Author: . A new Android malware called RatOn has evolved from a basic tool capable of conducting Near Field Communication (NFC) relay attacks to a...
Innovator Spotlight: Oleria – Source: www.cyberdefensemagazine.com
Source: www.cyberdefensemagazine.com – Author: Gary Identity’s New Frontier: How CISOs Can Navigate the Complex Landscape of Modern Access Management The cybersecurity battlefield has shifted. No longer...
Innovator Spotlight: Straiker – Source: www.cyberdefensemagazine.com
Source: www.cyberdefensemagazine.com – Author: Gary The AI Security Frontier: Protecting Tomorrow’s Digital Landscape Cybersecurity leaders are facing an unprecedented challenge. As artificial intelligence transforms how organizations...
Innovator Spotlight: Xcape – Source: www.cyberdefensemagazine.com
Source: www.cyberdefensemagazine.com – Author: Gary Continuous Vulnerability Management: The New Cybersecurity Imperative Security leaders are drowning in data but starving for actionable insights. Traditional penetration testing...
Innovator Spotlight: Corelight – Source: www.cyberdefensemagazine.com
Source: www.cyberdefensemagazine.com – Author: Gary The Network’s Hidden Battlefield: Rethinking Cybersecurity Defense Modern cyber threats are no longer knocking at the perimeter – they’re already inside....
Exploring Key Technology Trends for 2024 – Source: www.cyberdefensemagazine.com
Source: www.cyberdefensemagazine.com – Author: News team Fast forward to today, and the importance of staying current with the latest tech trends can’t be overstated – it’s...
Software Supply Chain Attacks – Source: www.cyberdefensemagazine.com
Source: www.cyberdefensemagazine.com – Author: News team In today’s rapidly evolving business landscape, software supply chain attacks are becoming increasingly common—and more sophisticated. The XZ backdoor attack,...
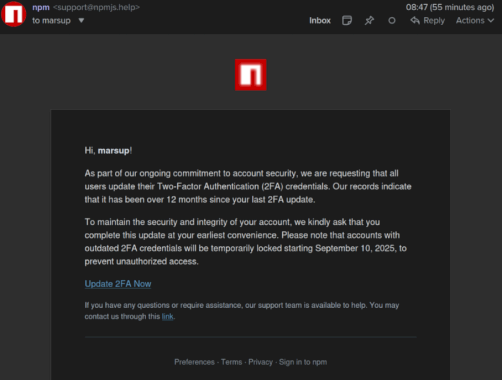
Supply chain attack targets npm, +2 Billion weekly npm downloads exposed – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Pierluigi Paganini September 09, 2025 Multiple popular npm packages were compromised in a supply chain attack after a maintainer fell...
LunaLock Ransomware threatens victims by feeding stolen data to AI models – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Pierluigi Paganini September 09, 2025 LunaLock, a new ransomware gang, introduced a unique cyber extortion technique, threatening to turn stolen...
Hackers breached Salesloft ’s GitHub in March, and used stole tokens in a mass attack – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Pierluigi Paganini September 08, 2025 Hackers breached Salesloft’s GitHub in March, stole tokens, and used them in a mass attack...
New enhancements to the Sophos AI Assistant – Source: news.sophos.com
Source: news.sophos.com – Author: Doug Aamoth PRODUCTS & SERVICES It isn’t just another AI tool — it’s expertise from the team behind the world’s leading MDR service....
Threat Actor Accidentally Exposes AI-Powered Operations – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: Written by A threat actor has unintentionally revealed their methods and day-to-day activities after installing Huntress security software on their own operating...
Salty2FA Phishing Kit Unveils New Level of Sophistication – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: A phishing campaign leveraging the Salty2FA kit has been uncovered by cybersecurity researchers, revealing advanced techniques that highlight the growing professionalism of...
Open Source Community Thwarts Massive npm Supply Chain Attack – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: A potential npm supply chain disaster was averted in record time after attackers took over a verified developer’s credentials. On September 8,...
Axios User Agent Helps Automate Phishing on “Unprecedented Scale” – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: Security experts have warned of a huge uptick in automated phishing activity abusing the Axios user agent and Microsoft’s Direct Send feature....
Chinese Cyber Espionage Campaign Impersonates US Congressman – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: US lawmakers have accused the Chinese government of being behind a cyber espionage campaign that impersonated a prominent Congressman. The House Select...
Salesloft: GitHub Account Breach Was Ground Zero in Drift Campaign – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: A major data theft campaign targeting Salesforce data via the Salesloft Drift app began after threat actors compromised a key GitHub account,...
New Docker Malware Strain Spotted Blocking Rivals on Exposed APIs – Source:hackread.com
Source: hackread.com – Author: Waqas. Akamai’s Hunt Team has reported a new variant of malware targeting exposed Docker APIs, expanding on a campaign first documented earlier...
Aembit Named to Fast Company’s Seventh-Annual List of the 100 Best Workplaces for Innovators – Source:hackread.com
Source: hackread.com – Author: CyberNewswire. Silver Spring, USA, September 9th, 2025, CyberNewsWire Fast Company today announced its seventh-annual Best Workplaces for Innovators list, recognizing businesses that...
SentinelOne Announces Plans to Acquire Observo AI – Source: www.darkreading.com
Source: www.darkreading.com – Author: Kristina Beek The combined company will help customers separate data ingestion from SIEM, to improve detection and performance. Original Post URL: https://www.darkreading.com/cybersecurity-operations/sentinelone-acquire-observo-ai...
‘MostereRAT’ Malware Blends In, Blocks Security Tools – Source: www.darkreading.com
Source: www.darkreading.com – Author: Jai Vijayan, Contributing Writer A threat actor is using a sophisticated EDR-killing malware tool in a campaign to maintain long-term, persistent access...
Salesloft Breached via GitHub Account Compromise – Source: www.darkreading.com
Source: www.darkreading.com – Author: Rob Wright The breach kickstarted a massive supply chain attack that led to the compromise of hundreds of Salesforce instances through stolen...
[Webinar] Shadow AI Agents Multiply Fast — Learn How to Detect and Control Them – Source:thehackernews.com
Source: thehackernews.com – Author: . ⚠️ One click is all it takes. An engineer spins up an “experimental” AI Agent to test a workflow. A business...
From MostereRAT to ClickFix: New Malware Campaigns Highlight Rising AI and Phishing Risks – Source:thehackernews.com
Source: thehackernews.com – Author: . Cybersecurity researchers have disclosed details of a phishing campaign that delivers a stealthy banking malware-turned-remote access trojan called MostereRAT. The phishing...
How Leading CISOs are Getting Budget Approval – Source:thehackernews.com
Source: thehackernews.com – Author: . It’s budget season. Once again, security is being questioned, scrutinized, or deprioritized. If you’re a CISO or security leader, you’ve likely...
TOR-Based Cryptojacking Attack Expands Through Misconfigured Docker APIs – Source:thehackernews.com
Source: thehackernews.com – Author: . Cybersecurity researchers have discovered a variant of a recently disclosed campaign that abuses the TOR network for cryptojacking attacks targeting exposed...
20 Popular npm Packages With 2 Billion Weekly Downloads Compromised in Supply Chain Attack – Source:thehackernews.com
Source: thehackernews.com – Author: . Multiple npm packages have been compromised as part of a software supply chain attack after a maintainer’s account was compromised in...