Source: www.csoonline.com – Author: Mutmaßlich chinesische Hacker drangen tief in Telekom-Netze in den USA ein. Jetzt wird bekannt, dass auch Dutzende andere Länder betroffen waren. Laut...
Month: August 2025
The CISO succession crisis: why companies have no plan and how to change that – Source: www.csoonline.com
Source: www.csoonline.com – Author: Organizations can no longer afford to wait for the cybersecurity leader to hand in their resignation to start looking for a replacement,...
7 Anzeichen für akuten MSSP-Bedarf – Source: www.csoonline.com
Source: www.csoonline.com – Author: Feature 28. Aug. 20256 Minuten IT-StrategieManaged Service Providers Managed Security Service Provider versprechen sorgenfreien Rundumschutz. Diese Signale deuten darauf hin, dass Sie...
Attackers exploiting NetScaler ADC and Gateway zero day flaw, Citrix warns – Source: www.csoonline.com
Source: www.csoonline.com – Author: Latest patches fix three dangerous flaws amid worries about possible ongoing persistence. Citrix NetScaler ADC and NetScaler Gateway customers have been hit...
Anthropic detects the inevitable: genAI-only attacks, no humans involved – Source: www.csoonline.com
Source: www.csoonline.com – Author: One cybersecurity consultant said this highly-expected development may change the attack community as the bad guys start getting laid off. When Anthropic...
Whistleblower: DOGE put Social Security database covering 300 million Americans on insecure cloud – Source: www.csoonline.com
Source: www.csoonline.com – Author: The complaint accuses DOGE of bypassing security protocols to move Americans’ sensitive personal data outside federal oversight and onto an insecure AWS...
Storm-0501 debuts a brutal hybrid ransomware attack chain – Source: www.csoonline.com
Source: www.csoonline.com – Author: Storm-0501 is hijacking privileged accounts, deleting backups, and encrypting cloud data in a new hybrid ransomware campaign. Microsoft urges CISOs to enforce...
Fachkräftemangel bedroht Cybersicherheit – Source: www.csoonline.com
Source: www.csoonline.com – Author: KI-gestützte Angriffe gelten als große Gefahr für die Cybersicherheit. Laut einer Studie stellt jedoch der Security-Personalmangel die größte Bedrohung dar. Um die...
NSA, FBI, Others Say Chinese Tech Firms are Aiding Salt Typhoon Attacks – Source: securityboulevard.com
Source: securityboulevard.com – Author: Jeffrey Burt Intelligence agencies in the United States and more than a dozen other countries are putting a focus on three Chinese...
Empowering Teams with Better Secrets Management – Source: securityboulevard.com
Source: securityboulevard.com – Author: Alison Mack Why is Secrets Management a Strategic Imperative? Why are global businesses increasingly focusing on secrets management? Intricate digital and growing...
De-identifying test data: K2View’s entity modeling vs Tonic’s native modeling – Source: securityboulevard.com
Source: securityboulevard.com – Author: Expert Insights on Synthetic Data from the Tonic.ai Blog The process of de-identifying test databases can be approached in a variety of...
BSidesSF 2025: Shadow IT Battlefield: The CyberHaven Breach And Defenses That Worked – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman Creators, Authors and Presenters: Rohit Bansal, Zach Pritchard Our deep appreciation to Security BSides – San Francisco and the Creators,...
The Coding Personalities of Leading LLMs—GPT-5 update – Source: securityboulevard.com
Source: securityboulevard.com – Author: Prasenjit Sarkar In our previous report, “The Coding Personalities of Leading LLMs,” we revealed the shared strengths and flaws of some of...
Emulating the Expedited Warlock Ransomware – Source: securityboulevard.com
Source: securityboulevard.com – Author: Francis Guibernau Introduction Warlock is a ransomware strain operating under the Ransomware-as-a-Service (RaaS) model that emerged in June 2025, following an advertisement...
TDL001 | Cybersecurity Explained: Privacy, Threats, and the Future | Chester Wisniewski – Source: securityboulevard.com
Source: securityboulevard.com – Author: Carly_Engelbrecht Summary “The Defenders Log” Episode 1 features host David Redekop and guest Chet Wisniewski discussing the dynamic world of cybersecurity. Wisniewski,...
DigiCert Discloses Details of Two Massive DDoS Attacks – Source: securityboulevard.com
Source: securityboulevard.com – Author: Michael Vizard DigiCert revealed today that over the last month it has thwarted two separate distributed denial of service (DDoS) attacks that...
Randall Munroe’s XKCD ‘Where Babies Come From’ – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman via the cosmic humor & dry-as-the-desert wit of Randall Munroe, creator of XKCD Permalink *** This is a Security Bloggers...
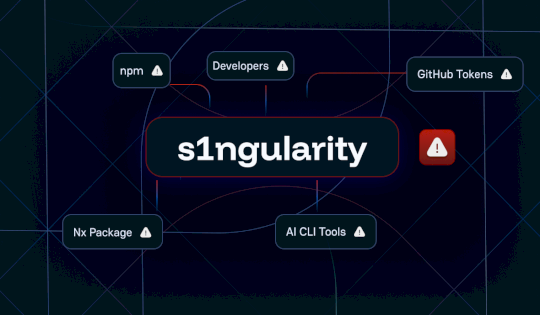
The Nx “s1ngularity” Attack: Inside the Credential Leak – Source: securityboulevard.com
Source: securityboulevard.com – Author: Guillaume Valadon This supply chain attack combines credential theft, environmental sabotage, and novel attack vectors, offering a glimpse into future threats. The...
CISA Strengthens Software Procurement Security With New Tool – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: A new Software Acquisition Guide: Supplier Response Web Tool has been released by the US Cybersecurity and Infrastructure Security Agency (CISA) to...
Researchers Discover First Reported AI-Powered Ransomware – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: In what is reportedly a world-first, ESET researchers have discovered PrompLock, a generative AI-powered ransomware implant currently in development. The researchers described...
Nevada “Network Security Incident” Shuts Down State Offices and Services – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: The State of Nevada has been hit by a “network security incident,” which has resulted in the closure of government offices and...
ShadowSilk Campaign Targets Central Asian Governments – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: A series of cyber-attacks against government organizations in Central Asia and the Asia-Pacific has been linked to a threat cluster known as...
Citrix Patches Three NetScaler Zero Days as One Sees Active Exploitation – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: Citrix has released patches for three zero-day vulnerabilities in NetScaler ADC and Gateway, one of which was already being exploited by attackers....
ENISA to Coordinate €36m EU-Wide Incident Response Scheme – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: The EU’s security agency is being given €36m ($42m) to handle incident response for major cyber-attacks targeting the bloc. ENISA yesterday announced...
New Data Theft Campaign Targets Salesforce via Salesloft App – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: Salesforce customers have again been targeted in a “widespread data theft campaign,” this time via compromised OAuth tokens associated with the third-party Salesloft...
New Phishing Campaign Abuses ConnectWise ScreenConnect to Take Over Devices – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: A novel phishing campaign attempts to trick victims into downloading ConnectWise ScreenConnect remote monitoring and management (RMM) software, enabling attackers to take...
AI Security Threat OneFlip Could Make Medical Devices, Self-Driving Cars Vulnerable – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: J.R. Johnivan OneFlip could cause self-driving cars to crash, facial recognition systems to fail, and biometric ID authenticators to shut down. A...
We Are Still Unable to Secure LLMs from Malicious Inputs – Source: www.schneier.com
Source: www.schneier.com – Author: Bruce Schneier Nice indirect prompt injection attack: Bargury’s attack starts with a poisoned document, which is shared to a potential victim’s Google...
News alert: Global security leaders to convene at OpenSSL 2025 — final week for early-bird rates – Source: www.lastwatchdog.com
Source: www.lastwatchdog.com – Author: cybernewswire Newark, N.J., Aug. 25, 2025, CyberNewwire — Only 7 days left to secure the Early Bird registration at the OpenSSL Conference...
UNC6384 Attack Detection: China-Linked Group Targets Diplomats and Hijacks Web Traffic Spreading a PlugX Variant – Source: socprime.com
Source: socprime.com – Author: Veronika Telychko The China-backed hacking collective tracked as UNC6384 has been observed behind cyber-espionage attacks against diplomats in Southeast Asia and various...