Source: securityboulevard.com – Author: Marc Handelman Creators, Authors and Presenters: Rohit Bansal, Zach Pritchard Our deep appreciation to Security BSides – San Francisco and the Creators,...
Day: August 28, 2025
The Coding Personalities of Leading LLMs—GPT-5 update – Source: securityboulevard.com
Source: securityboulevard.com – Author: Prasenjit Sarkar In our previous report, “The Coding Personalities of Leading LLMs,” we revealed the shared strengths and flaws of some of...
Emulating the Expedited Warlock Ransomware – Source: securityboulevard.com
Source: securityboulevard.com – Author: Francis Guibernau Introduction Warlock is a ransomware strain operating under the Ransomware-as-a-Service (RaaS) model that emerged in June 2025, following an advertisement...
TDL001 | Cybersecurity Explained: Privacy, Threats, and the Future | Chester Wisniewski – Source: securityboulevard.com
Source: securityboulevard.com – Author: Carly_Engelbrecht Summary “The Defenders Log” Episode 1 features host David Redekop and guest Chet Wisniewski discussing the dynamic world of cybersecurity. Wisniewski,...
DigiCert Discloses Details of Two Massive DDoS Attacks – Source: securityboulevard.com
Source: securityboulevard.com – Author: Michael Vizard DigiCert revealed today that over the last month it has thwarted two separate distributed denial of service (DDoS) attacks that...
Randall Munroe’s XKCD ‘Where Babies Come From’ – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman via the cosmic humor & dry-as-the-desert wit of Randall Munroe, creator of XKCD Permalink *** This is a Security Bloggers...
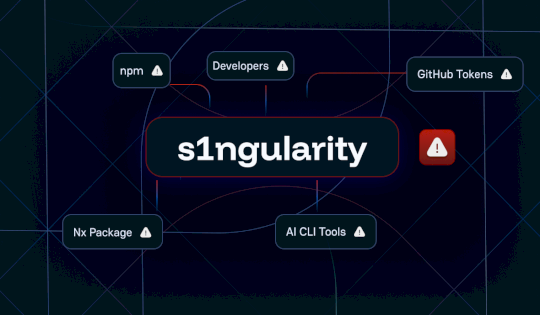
The Nx “s1ngularity” Attack: Inside the Credential Leak – Source: securityboulevard.com
Source: securityboulevard.com – Author: Guillaume Valadon This supply chain attack combines credential theft, environmental sabotage, and novel attack vectors, offering a glimpse into future threats. The...
CISA Strengthens Software Procurement Security With New Tool – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: A new Software Acquisition Guide: Supplier Response Web Tool has been released by the US Cybersecurity and Infrastructure Security Agency (CISA) to...
Researchers Discover First Reported AI-Powered Ransomware – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: In what is reportedly a world-first, ESET researchers have discovered PrompLock, a generative AI-powered ransomware implant currently in development. The researchers described...
Nevada “Network Security Incident” Shuts Down State Offices and Services – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: The State of Nevada has been hit by a “network security incident,” which has resulted in the closure of government offices and...
ShadowSilk Campaign Targets Central Asian Governments – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: A series of cyber-attacks against government organizations in Central Asia and the Asia-Pacific has been linked to a threat cluster known as...
Citrix Patches Three NetScaler Zero Days as One Sees Active Exploitation – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: Citrix has released patches for three zero-day vulnerabilities in NetScaler ADC and Gateway, one of which was already being exploited by attackers....
ENISA to Coordinate €36m EU-Wide Incident Response Scheme – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: The EU’s security agency is being given €36m ($42m) to handle incident response for major cyber-attacks targeting the bloc. ENISA yesterday announced...
New Data Theft Campaign Targets Salesforce via Salesloft App – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: Salesforce customers have again been targeted in a “widespread data theft campaign,” this time via compromised OAuth tokens associated with the third-party Salesloft...
New Phishing Campaign Abuses ConnectWise ScreenConnect to Take Over Devices – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: A novel phishing campaign attempts to trick victims into downloading ConnectWise ScreenConnect remote monitoring and management (RMM) software, enabling attackers to take...