Source: www.infosecurity-magazine.com – Author: Two local information-disclosure vulnerabilities have been identified in popular Linux crash-reporting tools, allowing attackers to access sensitive system data. The vulnerabilities, uncovered...
Month: June 2025
Sophisticated Malware Campaign Targets Windows and Linux Systems – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: A newly uncovered malware campaign targeting both Windows and Linux systems has revealed advanced evasion and credential theft techniques, according to the...
Cryptojacking Campaign Targets DevOps Servers Including Nomad – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: Researchers claim to have discovered the first case of threat actors using misconfigured HashiCorp Nomad deployments as an attack vector. The popular...
#Infosec2025: Ransomware Drill to Spotlight Water Utility Cyber Risks in ‘Operation 999’ – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: In the face of growing geopolitical instability, critical infrastructure organizations face an unprecedented level of cyber threats, putting their operations, data and...
Acreed Emerges as Dominant Infostealer Threat Following Lumma Takedown – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: An infostealer strain known as ‘Acreed’ could become the new market leader in credential theft malware, according to ReliaQuest. The cybersecurity company’s...
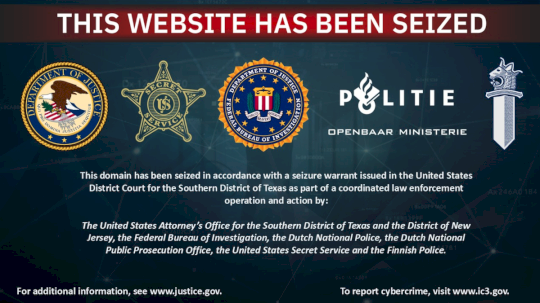
Dutch Police Lead Shut Down of Counter AV Service AVCheck – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: European and American law enforcers claim to have taken offline one of the world’s most prolific Counter Antivirus (CAV) services. AVCheck allowed...
Chrome to Distrust Chunghwa Telecom and Netlock Certificates – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ionut Arghire Google on Friday announced that the Chrome Root Store will no longer trust digital certificates issued by Chunghwa Telecom and...
Counter Antivirus Service AVCheck Shut Down by Law Enforcement – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ionut Arghire Dutch authorities announced the takedown of AVCheck, one of the largest counter antivirus (CAV) services used by cybercriminals worldwide. CAV...
SHARED INTEL Q&A: When every IoT Device and AI assistant has an identity — who’s in control? – Source: www.lastwatchdog.com
Source: www.lastwatchdog.com – Author: bacohido As enterprise adoption of generative AI accelerates, security teams face a new identity dilemma — not just more users and devices,...
Finding Stability in Cloud-Native Security Solutions – Source: securityboulevard.com
Source: securityboulevard.com – Author: Alison Mack How Critical is Stability in Cloud-Native Security? Stability is an essential aspect of a reliable cloud-native security strategy. Do you...
Future-proofing your enterprise: the role of crypto-agile PKI in long-term security – Source: securityboulevard.com
Source: securityboulevard.com – Author: Jason Soroko Traditional PKI creates bottlenecks that slow digital transformation due to manual processes and limited integration. As organizations adopt cloud, DevOps,...
OffensiveCon25 – Pwn20wn Winners Announcement – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman Author/Presenter: Brian Gore and Dustin Childs Our sincere appreciation to OffensiveCon by Binary Gecko, and the Presenters/Authors for publishing their...
Addressing Our ‘Age of Insecurity’ — in Cyber Too – Source: securityboulevard.com
Source: securityboulevard.com – Author: Lohrmann on Cybersecurity Lohrmann on Cybersecurity Recent cyber attacks have given a new urgency to business resiliency in the public and private...
Zero-Knowledge-Protokoll: Was Sie über zk-SNARK wissen sollten – Source: www.csoonline.com
Source: www.csoonline.com – Author: Eine Einführung in das populärste Zero-Knowledge-Protokoll zk-SNARK. Zero-Knowledge-Protokolle wie zk-SNARK nutzen die kleinstmögliche Informationsmenge zur Authentifizierung. Nomad Soul | shutterstock.com Unter den...
US Sanctions Philippine Company for Supporting Crypto Scams – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ionut Arghire The US Treasury Department on Thursday announced sanctions against a Philippines-based company for providing infrastructure to hundreds of thousands of...
Celebrate Pride Month with SWE
View our compilation of online stories and resources highlighting the LGBTQ+ community. Source Views: 2
Surveillance Via Smart Toothbrush – Source: www.schneier.com
Source: www.schneier.com – Author: Bruce Schneier HomeBlog Comments Clive Robinson • May 29, 2025 8:52 AM @ Bruce, ALL, This time it’s a “Smart Device”, or...
Scalable Strategies for Managing Cloud Machine Identities – Source: securityboulevard.com
Source: securityboulevard.com – Author: Alison Mack Are We Doing Enough to Safeguard Our Machine Identities? Securing human identities and their access permissions has been a focal...
Ensuring Safety in Your Secrets Vaulting Techniques – Source: securityboulevard.com
Source: securityboulevard.com – Author: Alison Mack Is Your Organization Unlocking Optimum Secrets Vaulting Possibilities? A particularly striking component is Non-Human Identities (NHIs). They have become a...
Is Innovation Driving Better NHI Management? – Source: securityboulevard.com
Source: securityboulevard.com – Author: Alison Mack How is Innovation Paving the Way for Improved NHI Management? Innovation stands as the lighthouse amidst the tumultuous sea of...
How Secrets Scanning is Evolving for Better Security – Source: securityboulevard.com
Source: securityboulevard.com – Author: Alison Mack Why is Secrets Scanning Important in Cybersecurity? Secrets scanning is paramount in cybersecurity. It involves identifying and mitigating risks associated...
BSidesLV24 – Keynotes: Closing Ceremony – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman Security Bloggers Network Home » Security Bloggers Network » BSidesLV24 – Keynotes: Closing Ceremony by Marc Handelman on May 31,...
New Relic Enhances Software Reliability with GitHub Copilot Integration – Source: securityboulevard.com
Source: securityboulevard.com – Author: Goverdhan Sisodia New Relic Integration with GitHub Copilot Coding Agent New Relic has introduced an integration with GitHub Copilot’s Coding Agent, enhancing...
Cybersecurity Alert: Major Breaches at TikTok and Ticketmaster – Source: securityboulevard.com
Source: securityboulevard.com – Author: Rajveer Singh A threat actor known as “Often9” has claimed to sell 428 million TikTok user records on a dark web forum....
Empowering Your Team with Strong IAM Practices – Source: securityboulevard.com
Source: securityboulevard.com – Author: Alison Mack Can Your Team Truly Benefit from Robust IAM Practices? I’ve had the chance to observe how different teams tackle their...
How Secure Are Your Non-Human Identities in the Cloud? – Source: securityboulevard.com
Source: securityboulevard.com – Author: Alison Mack Are Your Non-Human Identities As Secure As They Should Be? Cloud security is a pressing concern, particularly when it comes...
Can We Rely on Current Secrets Management Solutions? – Source: securityboulevard.com
Source: securityboulevard.com – Author: Alison Mack Can Secrets Management Really Secure our Digital Assets? How effective are current secrets management solutions? Are they adequate to safeguard...