Source: security.googleblog.com – Author: Kimberly Samra. Security Blog The latest news and insights from Google on security and safety on the Internet Original Post url: http://security.googleblog.com/2025/03/announcing-osv-scanner-v2-vulnerability.html...
Day: June 30, 2025
Vulnerability Reward Program: 2024 in Review – Source:security.googleblog.com
Source: security.googleblog.com – Author: Kimberly Samra. Security Blog The latest news and insights from Google on security and safety on the Internet Original Post url: http://security.googleblog.com/2025/03/vulnerability-reward-program-2024-in.html...
Ways to Mitigate Risk in Cybersecurity: Cybersecurity Risk Management – Source:www.hackercombat.com
Source: www.hackercombat.com – Author: Hacker Combat. Cyber threats can wreak havoc on businesses, from data breaches to loss of reputation. Luckily, there are effective strategies available...
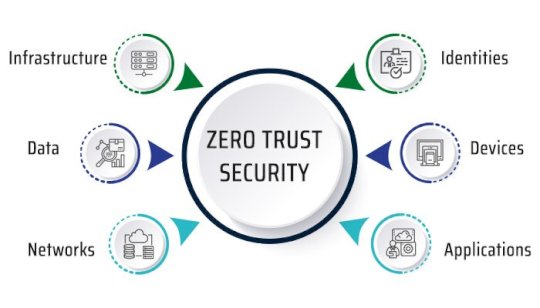
Zero Trust Architecture – Source:www.hackercombat.com
Source: www.hackercombat.com – Author: Hacker Combat. Zero trust security takes an “never trust, always verify” approach to access control. Access is only granted once an individual’s...
What Is a Security Operations Center (SOC)? – Source:www.hackercombat.com
Source: www.hackercombat.com – Author: Hacker Combat. A Security Operations Center (SOC) specializes in monitoring and analyzing data to detect cyber threats and prevent attacks from them....
Best Free EDR for Windows PC – Source:www.hackercombat.com
Source: www.hackercombat.com – Author: Hacker Combat. Endpoint detection and response (EDR) tools offer businesses that employ hybrid work models or remote employees an extra layer of...
Free EDR Solutions for Home Users in 2025 – Source:www.hackercombat.com
Source: www.hackercombat.com – Author: Hacker Combat. EDR can detect and respond to emerging and advanced cyber threats quickly and efficiently, making it an essential component of...
Cloud Security Essentials – Source:www.hackercombat.com
Source: www.hackercombat.com – Author: Hacker Combat. Cloud security involves employing perimeter defenses like firewalls, IDPSs and VPNs as well as guaranteeing isolation through network segmentation and...
Antivirus Software – Source:www.hackercombat.com
Source: www.hackercombat.com – Author: Hacker Combat. Antivirus software protects devices against viruses, malware, and other cyberthreats by detecting, quarantining, and deleting malicious code. Modern antivirus products...
How to Protect Against Ransomware Attacks? – Source:www.hackercombat.com
Source: www.hackercombat.com – Author: Hacker Combat. Criminal hackers employ ransomware attacks against their targets by encrypting their data and demanding that a ransom be paid within...
Celebrating 1 Year of CSF 2.0 – Source:www.nist.gov
Source: www.nist.gov – Author: Stephen Quinn. Sharing new CSF 2.0 resources; Taking a retrospective look at some resources and applications you may have missed; and Highlighting...
Privacy-Preserving Federated Learning – Future Collaboration and Continued Research – Source:www.nist.gov
Source: www.nist.gov – Author: Gary Howarth, Sue Anie. Reflections and Wider Considerations This is the final post in the series that began with reflections and learnings...
NIST’s International Cybersecurity and Privacy Engagement Update – New Translations – Source:www.nist.gov
Source: www.nist.gov – Author: Amy Mahn. As the year comes to a close, NIST continues to engage with our international partners to strengthen cybersecurity, including sharing...
Data Pipeline Challenges of Privacy-Preserving Federated Learning – Source:www.nist.gov
Source: www.nist.gov – Author: Dr. Xiaowei Huang, Dr. Yi Dong, Sikha Pentyala. Introduction In this post, we talk with Dr. Xiaowei Huang and Dr. Yi Dong (University of...
Kicking-Off with a December 4th Workshop, NIST is Revisiting and Revising Foundational Cybersecurity Activities for IoT Device Manufacturers, NIST IR 8259! – Source:www.nist.gov
Source: www.nist.gov – Author: Katerina Megas, Michael Fagan. In May 2020, NIST published Foundational Cybersecurity Activities for IoT Device Manufacturers (NIST IR 8259), which describes recommended...
Unlocking Cybersecurity Talent: The Power of Apprenticeships – Source:www.nist.gov
Source: www.nist.gov – Author: Marian Merritt. Cybersecurity is a fast-growing field, with a constant need for skilled professionals. But unlike other professions — like medicine or...
Scalability Challenges in Privacy-Preserving Federated Learning – Source:www.nist.gov
Source: www.nist.gov – Author: Joseph Near, David Darais, Mark Durkee. This post is part of a series on privacy-preserving federated learning. The series is a collaboration...
Managing Cybersecurity and Privacy Risks in the Age of Artificial Intelligence: Launching a New Program at NIST – Source:www.nist.gov
Source: www.nist.gov – Author: Katerina Megas. The rapid proliferation of Artificial Intelligence (AI) promises significant value for industry, consumers, and broader society, but as with many...
Standing Together Against Scams: McAfee Joins the Global Anti-Scam Alliance – Source:www.mcafee.com
Source: www.mcafee.com – Author: Jasdev Dhaliwal. At McAfee, we see the real faces behind the statistics. Our research shows, globally, people spend an average of 83...
Adidas Data Breach: What Consumers Need to Know and How to Protect Yourself – Source:www.mcafee.com
Source: www.mcafee.com – Author: Jasdev Dhaliwal. German sportswear giant Adidas has confirmed a significant cybersecurity incident that compromised customer personal information through an attack on their...
Cory’s Scam Story: A Fake Text Nearly Took His Identity – Source:www.mcafee.com
Source: www.mcafee.com – Author: Brooke Seipel. Cory considers himself pretty cautious. But like millions of people juggling packed schedules, one click on a hectic day proved...
Brittany’s Scam Story: Eras Tour Chaos – Source:www.mcafee.com
Source: www.mcafee.com – Author: Brooke Seipel. Brittany C., a dedicated teacher, had been planning a special night for months. After saving up steadily, she landed four...
Henry’s Scam Story: The Social Media Con – Source:www.mcafee.com
Source: www.mcafee.com – Author: Brooke Seipel. Henry A. had been trying for weeks to score a ticket to see Tyler, the Creator in Dallas. Even without...
Bradley’s Scam Story: New Dad vs Fake IRS Call – Source:www.mcafee.com
Source: www.mcafee.com – Author: Brooke Seipel. Bradley K. was a brand-new dad, sleep-deprived and juggling life with a newborn, when he received a phone call that...
This Week in Scams: $16.6 Billion Lost, Deepfakes Rise, and Google Email Scams Emerge – Source:www.mcafee.com
Source: www.mcafee.com – Author: Brooke Seipel. Welcome to the first edition of This Week in Scams, a new weekly series from McAfee breaking down the latest...
Interviewing for a Job? Spot a Scam with These Questions – Source:www.mcafee.com
Source: www.mcafee.com – Author: Brooke Seipel. Job scams are on the rise. And asking the right questions can help steer you clear of them. That rise...
Multiple Cisco Products Unauthenticated Remote Code Execution in Erlang/OTP SSH Server: April 2025 – Source:sec.cloudapps.cisco.com
Source: sec.cloudapps.cisco.com – Author: . Multiple Cisco Products Unauthenticated Remote Code Execution in Erlang/OTP SSH Server: April 2025 Critical CVE-2025-32433 CWE-306 Download CSAF Email Summary On...
AI in Endpoint Security – Source:levelblue.com
Source: levelblue.com – Author: hello@alienvault.com. It’s no revelation to say that the world of connectivity has fundamentally changed since the pandemic. What may be more eye-opening,...
Cisco Identity Services Engine RADIUS Denial of Service Vulnerability – Source:sec.cloudapps.cisco.com
Source: sec.cloudapps.cisco.com – Author: . Cisco Identity Services Engine RADIUS Denial of Service Vulnerability High CVE-2025-20152 CWE-125 Download CSAF Email Summary A vulnerability in the RADIUS...
DMARC MSP Case Study: How S-IT Automated Email Authentication Management with PowerDMARC – Source: securityboulevard.com
Source: securityboulevard.com – Author: Ahona Rudra “Reliable DMARC Solution with Excellent Support” Tom Glavas, Owner of S-IT Overview Company: S-IT Customer Type: MSP Partner Country: Belgium...