Source: www.darkreading.com – Author: Alexander Culafi, Senior News Writer, Dark Reading Please enable cookies. Sorry, you have been blocked You are unable to access darkreading.com Why...
Day: June 24, 2025
China-Nexus ‘LapDogs’ Network Thrives on Backdoored SOHO Devices – Source: www.darkreading.com
Source: www.darkreading.com – Author: Rob Wright Please enable cookies. Sorry, you have been blocked You are unable to access darkreading.com Why have I been blocked? This...
Steel Giant Nucor Confirms Data Stolen in Cyberattack – Source: www.darkreading.com
Source: www.darkreading.com – Author: Kristina Beek, Associate Editor, Dark Reading Please enable cookies. Sorry, you have been blocked You are unable to access darkreading.com Why have...
How the US Military Is Redefining Zero Trust – Source: www.darkreading.com
Source: www.darkreading.com – Author: Kelly Davis Please enable cookies. Sorry, you have been blocked You are unable to access darkreading.com Why have I been blocked? This...
Oh! Canada Added to List of Nations Targeted in Salt Typhoon Telecom Spree – Source: www.darkreading.com
Source: www.darkreading.com – Author: Elizabeth Montalbano, Contributing Writer Please enable cookies. Sorry, you have been blocked You are unable to access darkreading.com Why have I been...
IBM Pushes for More Collaboration Between Security, Governance – Source: www.darkreading.com
Source: www.darkreading.com – Author: Jeffrey Schwartz Please enable cookies. Sorry, you have been blocked You are unable to access darkreading.com Why have I been blocked? This...
Innovator Spotlight: Replica Cyber – Source: www.cyberdefensemagazine.com
Source: www.cyberdefensemagazine.com – Author: Gary Cybersecurity’s Dirty Little Secret: Reimagining Isolation – How Replica Cyber Empowers CISOs with Secure Environments in Seconds Imagine creating a completely...
Innovator Spotlight: Qualys – Source: www.cyberdefensemagazine.com
Source: www.cyberdefensemagazine.com – Author: Gary Demystifying Cyber Risk: How Qualys is Transforming Security Leadership Cybersecurity leadership is undergoing a profound transformation. No longer confined to technical...
The Hidden Front: Iran, Cyber Warfare, and the Looming Threat to U.S. Critical Infrastructure – Source: www.cyberdefensemagazine.com
Source: www.cyberdefensemagazine.com – Author: Gary By James Hess – CEO and Co-Founder, Unknown Cyber In today’s world, military strength is no longer defined solely by missiles...
TLDR* May Work for EULAs But Your Contracts? – Source: www.cyberdefensemagazine.com
Source: www.cyberdefensemagazine.com – Author: News team Time is a luxury few of us can afford to waste. Decision-makers often find themselves sifting through mountains of information,...
Trends in Ransomware Attacks in Q3, 2024 – Source: www.cyberdefensemagazine.com
Source: www.cyberdefensemagazine.com – Author: News team In the latest Q3 Ransomware Report from our team at Cyberint – a Check Point Software company and a leading...
Here’s a Subliminal Channel You Haven’t Considered Before – Source: www.schneier.com
Source: www.schneier.com – Author: Bruce Schneier HomeBlog Comments Mexaly • June 24, 2025 7:25 AM Look up, “The Clam Plate Orgy.” Circa 1975, this guy was...
UAC-0001 (APT28) Activity Detection: The russian State-Sponsored Group Targets Government Agencies Using BEARDSHELL and COVENANT Malware – Source: socprime.com
Source: socprime.com – Author: Veronika Telychko The nefarious nation-backed russian hacking collective known as UAC-0001 (aka APT28) reemerges in the cybersecurity spotlight. Over a year ago,...
Critical Authentication Bypass Flaw Patched in Teleport – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ionut Arghire Teleport on Friday warned of a critical-severity vulnerability in the open source platform that can be exploited remotely to bypass...
Half of Security Pros Want GenAI Deployment Pause – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: Around half (48%) of security professionals believe a “strategic pause” in generative AI deployment is needed to recalibrate defenses, according to a...
Reported Impersonation Scams Surge 148% as AI Takes Hold – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: The volume of impersonation scams has soared 148% year-on-year (YoY) thanks in part to AI tools making life easier for cybercriminals, according...
NCSC Urges Experts to Join Cyber Advisor Program – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: The UK’s leading cybersecurity agency has called for individuals and companies to join its Cyber Advisor scheme, in a bid to enhance...
Cyber Intel Pros and Hobbyists Can Now Report Threats Anonymously – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: Imagine a world in which any cybersecurity professional, or even a cyber hobbyist or whistleblower, could report a new cluster of malicious...
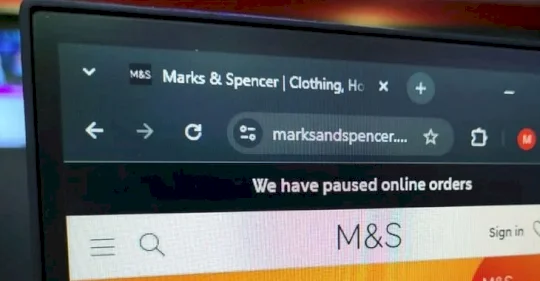
Marks & Spencer ransomware attack was good news for other retailers – Source: grahamcluley.com
Source: grahamcluley.com – Author: Graham Cluley Skip to content When Marks & Spencer paused online orders after it was hit by ransomware, it was bad news...
Twitter refuses to explain what it’s doing about hate speech and misinformation, sues New York State for asking – Source: grahamcluley.com
Source: grahamcluley.com – Author: Graham Cluley Skip to content Elon Musk’s Twitter (surely no-one really calls it X?) is suing New York State. Why? Because apparently...
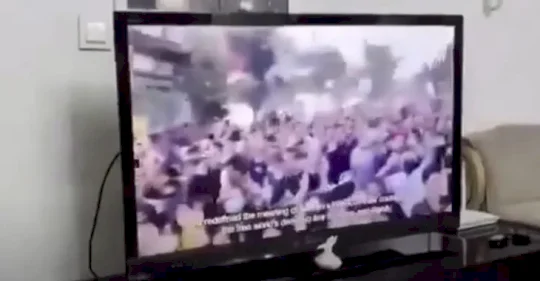
Iranian State TV hacked, and that’s modern warfare – Source: grahamcluley.com
Source: grahamcluley.com – Author: Graham Cluley Skip to content In modern warfare, it’s not just about who has the biggest bombs — it’s about who controls...
Yes, the Co-op lost your data. Have a £10 shopping voucher – Source: grahamcluley.com
Source: grahamcluley.com – Author: Graham Cluley Skip to content The Co-op is offering a £10 shopping discount to members after a cyber-attack saw hackers steal personal...
Infecting insurance firms with ransomware… for dummies – Source: grahamcluley.com
Source: grahamcluley.com – Author: Graham Cluley Ransomware gang infects insurance company, but DOESN’T install ransomware. Instead it steals information about insurance company’s clients, learns which have...
Breaking news – the Washington Post has been hacked – Source: grahamcluley.com
Source: grahamcluley.com – Author: Graham Cluley Skip to content The Washington Post says that the email accounts of some of its journalists have been hacked. The...
Cybercriminals left hanging as Victoria’s Secret bounces back – Source: grahamcluley.com
Source: grahamcluley.com – Author: Graham Cluley Skip to content Lingerie giant Victoria’s Secret says that it has restored all of its critical systems and is fully...
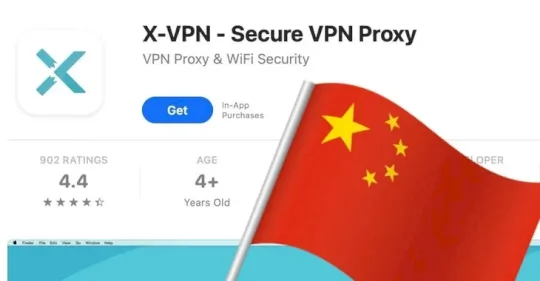
Chinese-owned VPN apps hide their origin – Source: grahamcluley.com
Source: grahamcluley.com – Author: Graham Cluley According to a new report, there are 13 China-owned VPN apps in the Apple App Store. None of them clearly...
SparkKitty Swipes Pics From iOS, Android Devices – Source: www.darkreading.com
Source: www.darkreading.com – Author: Jai Vijayan, Contributing Writer Please enable cookies. Sorry, you have been blocked You are unable to access darkreading.com Why have I been...
‘Echo Chamber’ Attack Blows Past AI Guardrails – Source: www.darkreading.com
Source: www.darkreading.com – Author: Alexander Culafi, Senior News Writer, Dark Reading Please enable cookies. Sorry, you have been blocked You are unable to access darkreading.com Why...
Citrix Patches Critical Vulns in NetScaler ADC and Gateway – Source: www.darkreading.com
Source: www.darkreading.com – Author: Kristina Beek, Associate Editor, Dark Reading Please enable cookies. Sorry, you have been blocked You are unable to access darkreading.com Why have...
DHS Warns of Rise in Cyberattacks in Light of US-Iran Conflict – Source: www.darkreading.com
Source: www.darkreading.com – Author: Kristina Beek, Associate Editor, Dark Reading Please enable cookies. Sorry, you have been blocked You are unable to access darkreading.com Why have...