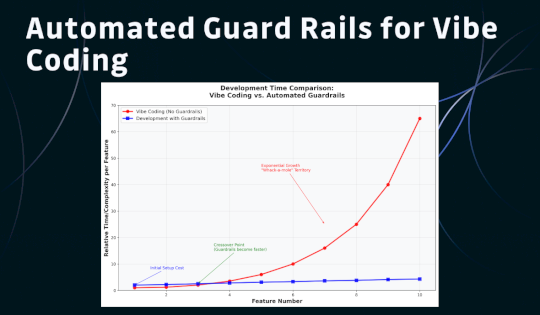
Source: securityboulevard.com – Author: Andy Rea There are countless warnings and horror stories about “vibe coding”—that flow state where you’re cranking out features and everything feels...
Day: June 17, 2025
App store malware AppSec Cyber Security News Cybersecurity Data Breach fake apps mobile app security Mobile Security Mobile threats rss-feed-post-generator-echo Security Boulevard Security Boulevard (Original) Social - Facebook Social - LinkedIn Social - X
App Store Security Threats in 2025: Why Hackers Target Mobile Ecosystems – Source: securityboulevard.com
Source: securityboulevard.com – Author: Alex Vakulov Mobile devices are now the primary gateway to the digital world. From banking to healthcare, users rely on apps for...
China-linked Hackers Cyber Security News Cybersecurity Data Privacy data security email hack FEATURED Identity & Access Industry Spotlight Mobile Security Network Security News rss-feed-post-generator-echo Security Boulevard Security Boulevard (Original) Social - Facebook Social - LinkedIn Social - X Spotlight Threat Intelligence Threats & Breaches Washington Post
Washington Post Journalists’ Microsoft Email Accounts Hacked – Source: securityboulevard.com
Source: securityboulevard.com – Author: Jeffrey Burt Several journalists with The Washington Post were targeted in a cyberattack that compromised their Microsoft email accounts, an echo of...