Source: www.darkreading.com – Author: Tara Seals Please enable cookies. Sorry, you have been blocked You are unable to access darkreading.com Why have I been blocked? This...
Day: June 6, 2025
F5 Acquires Agentic AI Security Startup Fletch – Source: www.darkreading.com
Source: www.darkreading.com – Author: Jeffrey Schwartz Please enable cookies. Sorry, you have been blocked You are unable to access darkreading.com Why have I been blocked? This...
BADBOX 2.0 Targets Home Networks in Botnet Campaign, FBI Warns – Source: www.darkreading.com
Source: www.darkreading.com – Author: Kristina Beek, Associate Editor, Dark Reading Please enable cookies. Sorry, you have been blocked You are unable to access darkreading.com Why have...
Docuseries Explores Mental, Physical Hardships of CISOs – Source: www.darkreading.com
Source: www.darkreading.com – Author: Arielle Waldman Please enable cookies. Sorry, you have been blocked You are unable to access darkreading.com Why have I been blocked? This...
Synthetic Data Is Here to Stay, but How Secure Is It? – Source: www.darkreading.com
Source: www.darkreading.com – Author: Hadi Chami Please enable cookies. Sorry, you have been blocked You are unable to access darkreading.com Why have I been blocked? This...
MSFT-CrowdStrike ‘Rosetta Stone’ for Naming APTs: Meh? – Source: www.darkreading.com
Source: www.darkreading.com – Author: Robert Lemos, Contributing Writer Please enable cookies. Sorry, you have been blocked You are unable to access darkreading.com Why have I been...
Prep for Layoffs Before They Compromise Security – Source: www.darkreading.com
Source: www.darkreading.com – Author: Mercedes Cardona Please enable cookies. Sorry, you have been blocked You are unable to access darkreading.com Why have I been blocked? This...
SecOps Teams Need to Tackle AI Hallucinations to Improve Accuracy – Source: www.darkreading.com
Source: www.darkreading.com – Author: Arielle Waldman Please enable cookies. Sorry, you have been blocked You are unable to access darkreading.com Why have I been blocked? This...
Attackers exploit Fortinet flaws to deploy Qilin ransomware – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Qilin ransomware now exploits Fortinet vulnerabilities to achieve remote code execution on impacted devices. Threat intelligence firm PRODAFT warned that...
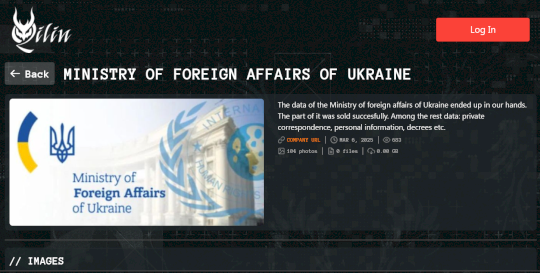
Russia-linked threat actors targets Ukraine with PathWiper wiper – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini A Russia-linked threat actor targeted a critical infrastructure organization in Ukraine with a new destructive malware dubbed PathWiper. Russia-linked threat...
U.S. Offers $10M bounty for info on RedLine malware creator and state hackers – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini The U.S. offers up to $10M for info on state hackers linked to RedLine malware and its creator, Maxim Rudometov,...
Play ransomware group hit 900 organizations since 2022 – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini A joint advisory from the US and Australian authorities states that Play ransomware has hit approximately 900 organizations over the...
New Atomic macOS Stealer Campaign Exploits ClickFix to Target Apple Users – Source:thehackernews.com
Source: thehackernews.com – Author: . Cybersecurity researchers are alerting to a new malware campaign that employs the ClickFix social engineering tactic to trick users into downloading...
Empower Users and Protect Against GenAI Data Loss – Source:thehackernews.com
Source: thehackernews.com – Author: . When generative AI tools became widely available in late 2022, it wasn’t just technologists who paid attention. Employees across all industries...
Microsoft Helps CBI Dismantle Indian Call Centers Behind Japanese Tech Support Scam – Source:thehackernews.com
Source: thehackernews.com – Author: . India’s Central Bureau of Investigation (CBI) has revealed that it has arrested six individuals and dismantled two illegal call centers that...
Inside the Mind of the Adversary: Why More Security Leaders Are Selecting AEV – Source:thehackernews.com
Source: thehackernews.com – Author: . Cybersecurity involves both playing the good guy and the bad guy. Diving deep into advanced technologies and yet also going rogue...
Friday Squid Blogging: Squid Run in Southern New England – Source: www.schneier.com
Source: www.schneier.com – Author: Bruce Schneier HomeBlog Friday Squid Blogging: Squid Run in Southern New England Southern New England is having the best squid run in...
Hearing on the Federal Government and AI – Source: www.schneier.com
Source: www.schneier.com – Author: Bruce Schneier Hearing on the Federal Government and AI On Thursday I testified before the House Committee on Oversight and Government Reform...
Report on the Malicious Uses of AI – Source: www.schneier.com
Source: www.schneier.com – Author: Bruce Schneier OpenAI just published its annual report on malicious uses of AI. By using AI as a force multiplier for our...
Popular Chrome Extensions Found Leaking Data via Unencrypted Connections – Source:hackread.com
Source: hackread.com – Author: Waqas. A recent investigation has revealed that several widely used Google Chrome extensions are transmitting sensitive user data over unencrypted HTTP connections,...
Scattered Spider Uses Tech Vendor Impersonation and Phishing Kits to Target Helpdesks – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: Scattered Spider, the ransomware collective believed to be behind recent retail hacks in the UK, including those targeting Marks & Spencer (M&S)...
#Infosec2025: Top Six Cyber Trends CISOs Need to Know – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: This year’s Infosecurity Europe 2025 saw industry experts come to together to discuss the latest trends, challenges and successes in the field....
Microsoft startet neues europäisches Sicherheitsprogramm – Source: www.csoonline.com
Source: www.csoonline.com – Author: Vor dem Hintergrund der zunehmenden Bedrohungslage im Cyberraum hat Microsoft eine neue Sicherheitsinitiative für Europa angekündigt. Microsoft will die Cybersicherheit in Europa...
New phishing campaign hijacks clipboard via fake CAPTCHA for malware delivery – Source: www.csoonline.com
Source: www.csoonline.com – Author: A single click and Ctrl+V combo now compromises endpoints with zero file downloads. A new wave of browser-based phishing tricks unsuspecting users...
Colossal breach exposes 4B Chinese user records in surveillance-grade database – Source: www.csoonline.com
Source: www.csoonline.com – Author: A meticulously curated dataset included WeChat IDs, bank details, Alipay data, home addresses, and behavioral profiles. A colossal data breach has reportedly...
Don’t give hacktivists what they really want – Source: www.csoonline.com
Source: www.csoonline.com – Author: Overload attacks such as DDoSes hurt society for the moment, but keeping our reactions to a reasonable level can help avoid an...
CISOs urged to push vendors for roadmaps on post-quantum cryptography readiness – Source: www.csoonline.com
Source: www.csoonline.com – Author: News Analysis Jun 6, 20254 mins Data and Information SecurityEncryption The looming ‘Q-Day’ should also be used as the stick to get...
Cybersecurity in der Lieferkette: Wie Sie Ihre Software-Supply-Chain schützen – Source: www.csoonline.com
Source: www.csoonline.com – Author: Software-Lieferketten stehen unter Druck: Eine Schwachstelle entlang der Lieferkette kann zu einer Vielzahl von Opfern führen. So können sich Unternehmen schützen. Um...
CISA asks CISOs: Does that asset really have to be on the internet? – Source: www.csoonline.com
Source: www.csoonline.com – Author: News Jun 5, 20255 mins Data and Information SecuritySecurityThreat and Vulnerability Management Too many vulnerable IT/OT assets are unnecessarily online, says CISA....