Source: securityboulevard.com – Author: Michael Vizard Salt Security this week at the 2025 RSA Conference made available an early preview of an ability to secure Model...
Month: May 2025
McAfee Named One of America’s Best Employers by Forbes – Source:www.mcafee.com
Source: www.mcafee.com – Author: McAfee. We’re thrilled to share some exciting news—McAfee has been recognized on Forbes’ prestigious list of America’s Best Midsize Employers for 2025!...
Israel’s 77 Years Of Independence – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman Permalink *** This is a Security Bloggers Network syndicated blog from Infosecurity.US authored by Marc Handelman. Read the original post...
The 9 Most Common Social Media Scams—and How to Spot Them Before It’s Too Late – Source:www.mcafee.com
Source: www.mcafee.com – Author: Jasdev Dhaliwal. Social media connects us to friends, trends, and news in real time—but it also opens the door to scammers looking...
BSidesLV24 – Ground Truth – Hacking Things That Think – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman Home » Security Bloggers Network » BSidesLV24 – Ground Truth – Hacking Things That Think Author/Presenter: Matthew Canham Our sincere...
How to Spot a Crypto Scam: The Top Red Flags to Watch For – Source:www.mcafee.com
Source: www.mcafee.com – Author: Brooke Seipel. Cryptocurrency offers exciting opportunities—but it’s also a favorite playground for scammers. With the rapid rise of deepfake technology and deceptive...
Navigating the SaaS Attack Chain: Mitigating Risks with AppOmni – Source: securityboulevard.com
Source: securityboulevard.com – Author: Rebecca Crum In today’s fast-paced digital landscape, the attack chain for SaaS applications is both condensed and faster than ever before. Cybercriminals...
How to Avoid Romance Scams – Source:www.mcafee.com
Source: www.mcafee.com – Author: Jasdev Dhaliwal. It starts with a simple DM on Instagram. It ends with an AI-generated con artist, thousands of dollars lost, and...
Where’s the SOAR Magic Quadrant? – Source: securityboulevard.com
Source: securityboulevard.com – Author: Katie Bykowski If you’re searching for the Gartner SOAR Magic Quadrant, we hate to break it to you—but it no longer exists....
AI chatbots are becoming romance scammers—and 1 in 3 people admit they could fall for one – Source:www.mcafee.com
Source: www.mcafee.com – Author: Jasdev Dhaliwal. It started with a DM. For five months, 25-year-old computer programmer Maggie K. exchanged daily messages with the man she...
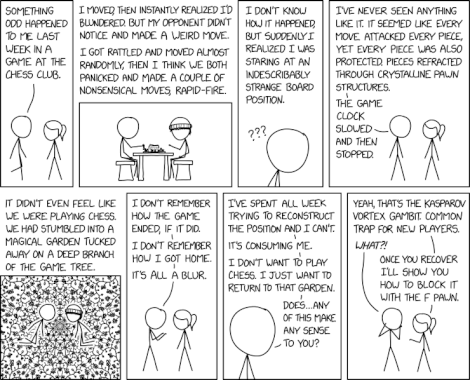
Randall Munroe’s XKCD ‘Chess Position’ – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman Thursday, May 1, 2025 Security Boulevard The Home of the Security Bloggers Network Community Chats Webinars Library Home Cybersecurity News...
Buying Tickets for Beyoncé’s Cowboy Carter Tour? Don’t Let Scammers Ruin Your Experience – Source:www.mcafee.com
Source: www.mcafee.com – Author: Jasdev Dhaliwal. Beyoncé has officially announced her Cowboy Carter world tour, and the excitement is through the roof! With her last tour...
Scam Alert: Fake Minecraft, Roblox Hacks on YouTube Hide Malware, Target Kids – Source:www.mcafee.com
Source: www.mcafee.com – Author: Brooke Seipel. Video games are a favorite pastime for millions of kids and teenagers worldwide, offering exciting challenges, epic battles, and opportunities...
How Uncoder AI Clarifies CVE-2024-35250 Detection in Cortex XSIAM – Source: socprime.com
Source: socprime.com – Author: Steven Edwards When new CVEs drop, defenders race to understand how attackers might exploit them. One such vulnerability—CVE-2024-35250—involves suspicious usage of the...
Detecting NimScan Activity in SentinelOne with Uncoder AI – Source: socprime.com
Source: socprime.com – Author: Steven Edwards Potentially Unwanted Applications (PUAs) like NimScan.exe can silently operate within enterprise environments, probing internal systems or facilitating lateral movement. Detecting...
Uncovering PUA: NimScan Activity with Full Summary in Uncoder AI – Source: socprime.com
Source: socprime.com – Author: Steven Edwards In threat detection, time is everything. Especially when identifying tools like NimScan—a known Potentially Unwanted Application (PUA) often associated with...
Password Discovery via Notepad: How Uncoder AI Simplifies SPL Detection Logic – Source: socprime.com
Source: socprime.com – Author: Steven Edwards Attackers often use trusted tools like Notepad to discreetly access sensitive files, especially those labeled as password-related. This tactic blends...
Cisco IOS, IOS XE, and IOS XR Software SNMP Denial of Service Vulnerabilities – Source:sec.cloudapps.cisco.com
Source: sec.cloudapps.cisco.com – Author: . Cisco IOS, IOS XE, and IOS XR Software SNMP Denial of Service Vulnerabilities High CVE-2025-20169 CVE-2025-20170 CVE-2025-20171 More… CWE-805 Download CSAF...
Cisco IOS XR Software Access Control List Bypass Vulnerability – Source:sec.cloudapps.cisco.com
Source: sec.cloudapps.cisco.com – Author: . Cisco IOS XR Software Access Control List Bypass Vulnerability Medium CVE-2025-20145 CWE-264 Download CSAF Email Summary A vulnerability in the access...
News alert: Link11 integrates DOSarrest, Reblaze to deliver advanced, integrated security platform – Source: www.lastwatchdog.com
Source: www.lastwatchdog.com – Author: cybernewswire Frankfurt, Apr.30, 2025, CyberNewswire – Link11, DOSarrest, and Reblaze have combined their strengths into a single, integrated platform with a new...
RSAC Fireside Chat: Shift left, think forward — why MDR is emerging as cyber’s silver bullet – Source: www.lastwatchdog.com
Source: www.lastwatchdog.com – Author: bacohido By Byron V. Acohido With RSAC kicking off next week, the conversation is shifting—literally. Cybersecurity pros are rethinking how “shift left”...
Welcoming The Gambia National CSIRT to Have I Been Pwned – Source: www.troyhunt.com
Source: www.troyhunt.com – Author: Troy Hunt Today, we’re happy to welcome the Gambia National CSIRT to Have I Been Pwned as the 38th government to be...
Weekly Update 445 – Source: www.troyhunt.com
Source: www.troyhunt.com – Author: Troy Hunt Well, this certainly isn’t what I expected to be talking about this week! But I think the fact it was...
A Sneaky Phish Just Grabbed my Mailchimp Mailing List – Source: www.troyhunt.com
Source: www.troyhunt.com – Author: Troy Hunt You know when you’re really jet lagged and really tired and the cogs in your head are just moving that...
Weekly Update 444 – Source: www.troyhunt.com
Source: www.troyhunt.com – Author: Troy Hunt Sponsored by: It’s time to fly! 🇬🇧 🇮🇸 🇮🇪 That’s two new flags (or if you’re on Windows and can’t...
Weekly Update 443 – Source: www.troyhunt.com
Source: www.troyhunt.com – Author: Troy Hunt Sponsored by: What an awesome response to the new brand! I’m so, so happy with all the feedback, and I’ve...
Soft-Launching and Open Sourcing the Have I Been Pwned Rebrand – Source: www.troyhunt.com
Source: www.troyhunt.com – Author: Troy Hunt Designing the first logo for Have I Been Pwned was easy: I took a SQL injection pattern, wrote “have i...
Weekly Update 442 – Source: www.troyhunt.com
Source: www.troyhunt.com – Author: Troy Hunt We survived the cyclone! That was a seriously weird week with lots of build-up to an event that last occurred...
We’re Backfilling and Cleaning Stealer Logs in Have I Been Pwned – Source: www.troyhunt.com
Source: www.troyhunt.com – Author: Troy Hunt I think I’ve finally caught my breath after dealing with those 23 billion rows of stealer logs last week. That...
Weekly Update 441 – Source: www.troyhunt.com
Source: www.troyhunt.com – Author: Troy Hunt Sponsored by: Processing data breaches (especially big ones), can be extremely laborious. And, of course, everyone commenting on them is...