Source: securityboulevard.com – Author: Scott Fiesel by Source Defense Even with the PCI DSS 4.0 deadline now behind us, many organizations are still exposed to costly...
Month: May 2025
BSidesLV24 – PasswordsCon – Long Live Short Lived Credentials – Auto-Rotating Secrets At Scale – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman Home » Security Bloggers Network » BSidesLV24 – PasswordsCon – Long Live Short Lived Credentials – Auto-Rotating Secrets At Scale...
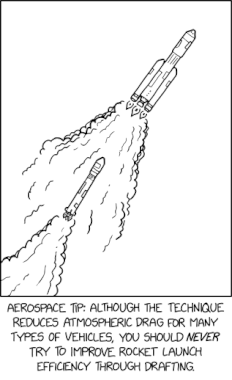
Randall Munroe’s XKCD ‘Drafting’ – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman Wednesday, May 28, 2025 Security Boulevard The Home of the Security Bloggers Network Community Chats Webinars Library Home Cybersecurity News...
RSA and Bitcoin at BIG Risk from Quantum Compute – Source: securityboulevard.com
Source: securityboulevard.com – Author: Richi Jennings Researchers find we’ll need 20 times fewer qubits to break public-key encryption than previously believed. A new paper puts a fire...
Seceon Wins “MSP Platform Provider Vendor of the Year” at Technology Reseller Awards 2025 – Source: securityboulevard.com
Source: securityboulevard.com – Author: Kriti Tripathi At Seceon, we’re honored to announce that we have been named the “MSP Platform Provider Vendor of the Year” at...
SBOM management and generation: How Sonatype leads in software supply chain visibility – Source: securityboulevard.com
Source: securityboulevard.com – Author: Aaron Linskens As software supply chain threats become more complex, organizations need more than just vulnerability scanning — they need complete visibility...
Protecting Biomedical Devices in the Large Healthcare Enterprise – Source: securityboulevard.com
Source: securityboulevard.com – Author: Bob Palmer The Cyber Risk to the Healthcare Enterprise is Significant—and it’s Growing Due to Increased Connectivity of Medical Devices Biomedical devices...
Unsophisticated Actors, Poor Hygiene Prompt CI Alert for Oil & Gas – Source: securityboulevard.com
Source: securityboulevard.com – Author: Teri Robinson A recent multiagency alert is pressing critical infrastructure organizations within the oil & gas sector to clean up their act...
BSidesLV24 – PasswordsCon – Combating Phone Spoofing With STIR/SHAKEN – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman Home » Security Bloggers Network » BSidesLV24 – PasswordsCon – Combating Phone Spoofing With STIR/SHAKEN Author/Presenter: Per Thorsheim Our sincere...
AI-Powered SPL Rule Generation for WRECKSTEEL IOC Detection – Source: socprime.com
Source: socprime.com – Author: Steven Edwards How It Works Uncoder AI converts complex threat intelligence—like the CERT-UA#14283 report on the WRECKSTEEL PowerShell stealer—into Splunk’s Search Processing...
BadSuccessor Detection: Critical Windows Server Vulnerability Can Compromise Any User in Active Directory – Source: socprime.com
Source: socprime.com – Author: Veronika Telychko Following the disclosure of CVE-2025-4427 and CVE-2025-4428, two Ivanti EPMM vulnerabilities that can be chained for RCE, another critical security...
AI-Generated SentinelOne DNS Query for WRECKSTEEL Detection – Source: socprime.com
Source: socprime.com – Author: Steven Edwards How It Works Uncoder AI streamlines threat detection in SentinelOne by automatically transforming raw intelligence into executable event queries. In...
AI-Powered IOC Parsing for WRECKSTEEL Detection in CrowdStrike – Source: socprime.com
Source: socprime.com – Author: Steven Edwards How It Works Uncoder AI automates the decomposition of complex IOC-driven detection logic authored in CrowdStrike Endpoint Query Language (EQL)....
IOC-to-Query Conversion for SentinelOne in Uncoder AI – Source: socprime.com
Source: socprime.com – Author: Steven Edwards How It Works 1. IOC Extraction from Threat Report Uncoder AI automatically parses and categorizes indicators from the incident report...
Law Firms Warned of Silent Ransom Group Attacks – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ionut Arghire The FBI is cautioning US law firms that they have become frequent targets of the Silent Ransom Group (SRG) extortion...
Chinese-Owned VPNs – Source: www.schneier.com
Source: www.schneier.com – Author: Bruce Schneier One one my biggest worries about VPNs is the amount of trust users need to place in them, and how...
Quantencomputer knacken RSA-Verschlüsselungen noch schneller – Source: www.csoonline.com
Source: www.csoonline.com – Author: Neue Forschungsergebnisse zeigen, dass die RSA-Verschlüsselung in Zukunft mit Hilfe von Quantentechnologie 20 mal schneller geknackt werden können. Im Hinblick auf die...
Wer landet im Netz der Cyber-Spinne? – Source: www.csoonline.com
Source: www.csoonline.com – Author: Feature 27. Mai 20254 Minuten RansomwareSicherheitspraktikenSocial Engineering Nach einer Angriffsserie auf britische Kaufhäuser geben Experten Ratschläge, wie sich CISOs gegen Scattered Spider...
Hackers drop 60 npm bombs in less than two weeks to recon dev machines – Source: www.csoonline.com
Source: www.csoonline.com – Author: All malicious npm packages carried identical payloads for snooping sensitive network information from developers’ systems. Threat actors have likely made off with...
How CISOs can defend against Scattered Spider ransomware attacks – Source: www.csoonline.com
Source: www.csoonline.com – Author: CISOs should fortify help desk and employee defenses, enhance intrusion detection and tracking capabilities, and recognize that paying ransoms is not a...
Diese Social-Engineering-Trends sollten Sie kennen – Source: www.csoonline.com
Source: www.csoonline.com – Author: Social Engineering ist fast so alt wie die IT. Doch der Einsatz von KI bietet Cyberkriminellen neue Möglichkeiten. Beim Social Engineering nutzen...
US Government Launches Audit of NIST’s National Vulnerability Database – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: The US government has begun an audit of its National Vulnerability Database (NVD) to ensure its team can catch up with the...
Governments Urge Organizations to Prioritize SIEM/SOAR Adoption – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: A new joint government advisory has urged organizations to prioritize the implementation of Security Information and Event Management (SIEM) and Security Orchestration,...
Chinese Hackers Exploit Cityworks Flaw to Target US Local Governments – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: Chinese hackers are targeting local government organizations in the US by exploiting a vulnerability in Cityworks, a popular asset management system. Cisco...
Understanding the Importance of Incident Response Plans for Nonprofits – Source: securityboulevard.com
Source: securityboulevard.com – Author: Devin Partida Nonprofits do vital work in their communities, which may create a tempting target for criminals. Increasingly sophisticated cybersecurity threats make...
MSP Case Study: How PowerDMARC Became a Game-Changer for HispaColex Tech Consulting – Source: securityboulevard.com
Source: securityboulevard.com – Author: Ahona Rudra “PowerDMARC has been a game-changer for our IT team!” Sebastián Valero Márquez (IT Manager at HispaColex Tech Consulting) Overview Company:...
How Free Are Your NHIs from Cyber Threats? – Source: securityboulevard.com
Source: securityboulevard.com – Author: Alison Mack How Secure Are Your Non-Human Identities From Cyber Threats? Are you confident that your non-human identities (NHIs) are free from...
How NHIs Deliver Value to Your Security Architecture – Source: securityboulevard.com
Source: securityboulevard.com – Author: Alison Mack Why Does NHI Value Matter To Your Security Architecture? For many businesses embarking on digital transformation journeys, the role of...
Feel Relieved by Perfecting Your NHI Tactics – Source: securityboulevard.com
Source: securityboulevard.com – Author: Alison Mack Is Your Cybersecurity Strategy Ready for Non-Human Identities? Non-Human Identities (NHIs) and Secrets Security Management have emerged as crucial components...
The Hidden Cyber Risks in Your Executive Team’s Digital Footprint – Source: securityboulevard.com
Source: securityboulevard.com – Author: Laura Bruck Executive Team’s Digital Footprint Exposure Is Real Executives, board members, and other high-profile users carry more than just influence –...