Source: thehackernews.com – Author: . The U.S. Cybersecurity and Infrastructure Security Agency (CISA) has added a maximum-severity security flaw impacting Commvault Command Center to its Known...
Month: May 2025
⚡ Weekly Recap: Nation-State Hacks, Spyware Alerts, Deepfake Malware, Supply Chain Backdoors – Source:thehackernews.com
Source: thehackernews.com – Author: . What if attackers aren’t breaking in—they’re already inside, watching, and adapting? This week showed a sharp rise in stealth tactics built...
Perfection is a Myth. Leverage Isn’t: How Small Teams Can Secure Their Google Workspace – Source:thehackernews.com
Source: thehackernews.com – Author: . Let’s be honest: if you’re one of the first (or the first) security hires at a small or midsize business, chances...
How to Prevent AI Agents From Becoming the Bad Guys – Source: www.darkreading.com
Source: www.darkreading.com – Author: Marla Hay Please enable cookies. Sorry, you have been blocked You are unable to access darkreading.com Why have I been blocked? This...
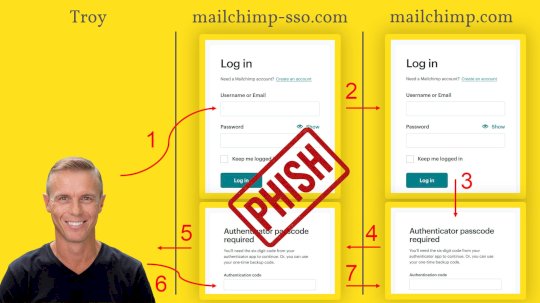
Passkeys for Normal People – Source: www.troyhunt.com
Source: www.troyhunt.com – Author: Troy Hunt Let me start by very simply explaining the problem we’re trying to solve with passkeys. Imagine you’re logging on to...
Small Businesses Create Big Impact: NIST Celebrates 2025 National Small Business Week – Source:www.nist.gov
Source: www.nist.gov – Author: Daniel Eliot. This week we’re celebrating National Small Business Week—which recognizes and celebrates the small and medium-sized business (SMB) community’s significant contributions to...
NIS2 Compliance Checklist – Source: heimdalsecurity.com
Source: heimdalsecurity.com – Author: Gabriella Antal The NIS2 Compliance Directive is a pivotal regulation aimed at enhancing cybersecurity within critical sectors across the European Union. With...
EU Adopts New Cybersecurity Rules for Critical Infrastructure Under NIS2 Directive – Source: heimdalsecurity.com
Source: heimdalsecurity.com – Author: Gabriella Antal The European Commission has adopted new cybersecurity rules for critical infrastructure across the EU, taking a major step toward enhancing...
Experts shared up-to-date C2 domains and other artifacts related to recent MintsLoader attacks – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini MintsLoader is a malware loader delivering the GhostWeaver RAT via a multi-stage chain using obfuscated JavaScript and PowerShell. Recorded Future...
Sansec uncovered a supply chain attack via 21 backdoored Magento extensions – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Supply chain attack via 21 backdoored Magento extensions hit 500–1,000 e-stores, including a $40B multinational. Sansec researchers reported that multiple...
US authorities have indicted Black Kingdom ransomware admin – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini A 36-year-old Yemeni man behind Black Kingdom ransomware is indicted in the U.S. for 1,500 attacks on Microsoft Exchange servers....
Ransomware-Attacke auf AWO Gießen – Source: www.csoonline.com
Source: www.csoonline.com – Author: Die Arbeiterwohlfahrt (AWO) Gießen wurde Ziel einer Cyberattacke. Die Täter haben Server verschlüsselt und eine Lösegeldforderung hinterlassen. Cyberkriminelle haben die Server der...
Company behind modified Signal app used by Mike Waltz allegedly hacked – Source: www.csoonline.com
Source: www.csoonline.com – Author: News May 5, 20255 mins EncryptionMessaging SecuritySecurity Researchers uncover security weaknesses in obscure TM SGNL app and indications that its Israeli maker...
Top cybersecurity products showcased at RSA 2025 – Source: www.csoonline.com
Source: www.csoonline.com – Author: From automated defense to advanced analytics, AI was at the heart of nearly every breakthrough as cybersecurity giants showcased innovative approaches to...
12 most innovative launches at RSA 2025 – Source: www.csoonline.com
Source: www.csoonline.com – Author: Discover the companies redefining cybersecurity with AI-powered solutions, from emerging players to seasoned pros. The RSA 2025 conference didn’t just belong to...
CISO vs CFO: why are the conversations difficult? – Source: www.csoonline.com
Source: www.csoonline.com – Author: Bridging the gap between CISOs and CFOs means ditching old stereotypes, speaking the same language, and turning cybersecurity from a budget battle...
Multiple Cisco Products Snort Rate Filter Bypass Vulnerability – Source:sec.cloudapps.cisco.com
Source: sec.cloudapps.cisco.com – Author: . Multiple Cisco Products Snort Rate Filter Bypass Vulnerability Medium CVE-2024-20342 CWE-1025 Download CSAF Email Summary Multiple Cisco products are affected by...
Cisco Crosswork Network Controller Stored Cross-Site Scripting Vulnerabilities – Source:sec.cloudapps.cisco.com
Source: sec.cloudapps.cisco.com – Author: . Cisco Crosswork Network Controller Stored Cross-Site Scripting Vulnerabilities Medium CVE-2025-20123 CWE-79 Download CSAF Email Summary Multiple vulnerabilities in the web-based management...
TikTok Fined €530m Over Transfers of European User Data to China – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: The Irish Data Protection Commission (DPC) announced on May 2 that it was issuing a €530m ($600m) fine to TikTok’s European branch...
Ransomware Attacks Fall in April Amid RansomHub Outage – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: Ransomware attacks declined significantly in April, partly as a result of the RansomHub gang experiencing infrastructure outages, according to a new analysis...
Trump promises protection for TikTok, for which he has a ‘warm spot in my heart’ – Source: go.theregister.com
Source: go.theregister.com – Author: Simon Sharwood US President Donald Trump has said TikTok will be “very strongly protected” as the made-in-China social network has “a warm...
India’s chipmaking ambitions hurt by Zoho’s no-go and Adani unease – Source: go.theregister.com
Source: go.theregister.com – Author: Simon Sharwood PLUS: China spring cleans its AIs; South Korea fines Meta, probes Broadcom; and more! India’s ambition to become a global...
Microsoft tries to knife passwords once and for all – at least for consumers – Source: go.theregister.com
Source: go.theregister.com – Author: Brandon Vigliarolo Infosec In Brief Microsoft has decided to push its consumer customers to dump password in favor of passkeys. The software...
RSAC wrap: AI and China on everything, everywhere, all at once – Source: go.theregister.com
Source: go.theregister.com – Author: Jessica Lyons RSAC Another RSAC has come and gone, with almost 44,000 attendees this year spread across San Francisco’s Moscone Center and...
ID Me and You for SWE Section Taxes
As tax season approaches the SWE Finance Committee wants your SWE section to be prepared. Source Views: 2
Technical Career Path Panel
This event is organized by the Technical Career Path Affinity Group Source Views: 0
SWE-ET High School Summer Research Experience
As a rising junior at Highlands Ranch High School in Colorado, in the summer of 2022, I had the chance to intern for the Pak Research...
Black History Month: Stand Out Women in STEM
In honor of Black History Month, we are recognizing African American women who don’t just work in some of the world’s most innovative STEM fields, they...
Considerations When Selecting a College
Narrowing down which college you will go to can be a stressful decision. Use the tips below to help make picking your final choice easier! Source...