Source: thehackernews.com – Author: . Run by the team at workflow orchestration and AI platform Tines, the Tines library features pre-built workflows shared by security practitioners...
Month: May 2025
MintsLoader Drops GhostWeaver via Phishing, ClickFix — Uses DGA, TLS for Stealth Attacks – Source:thehackernews.com
Source: thehackernews.com – Author: . The malware loader known as MintsLoader has been used to deliver a PowerShell-based remote access trojan called GhostWeaver. “MintsLoader operates through...
Attackers Ramp Up Efforts Targeting Developer Secrets – Source: www.darkreading.com
Source: www.darkreading.com – Author: Robert Lemos, Contributing Writer Please enable cookies. Sorry, you have been blocked You are unable to access darkreading.com Why have I been...
Despite Arrests, Scattered Spider Continues High-Profile Hacking – Source: www.darkreading.com
Source: www.darkreading.com – Author: Rob Wright Please enable cookies. Sorry, you have been blocked You are unable to access darkreading.com Why have I been blocked? This...
Cut CISA and Everyone Pays for It – Source: www.darkreading.com
Source: www.darkreading.com – Author: Audian Paxson Please enable cookies. Sorry, you have been blocked You are unable to access darkreading.com Why have I been blocked? This...
Uncovering Insider Risks with Full Summary in Uncoder AI: A Microsoft Defender for Endpoint Case – Source: socprime.com
Source: socprime.com – Author: Steven Edwards Identifying unauthorized access to sensitive data—especially passwords—remains a critical concern for cybersecurity teams. When such access happens through legitimate tools...
Investigating Suspicious Rsync Shell Activity with Uncoder AI and Carbon Black Query Language – Source: socprime.com
Source: socprime.com – Author: Steven Edwards Monitoring remote file transfer utilities like rsync is essential in detecting stealthy lateral movement or data exfiltration across Unix-based environments....
Enhancing Cortex XQL Threat Detection with Full Summary in Uncoder AI – Source: socprime.com
Source: socprime.com – Author: Steven Edwards As attackers become more creative in bypassing traditional network defenses, analysts need fast, clear insight into the logic behind complex...
Visualizing Malicious curl Proxy Activity in CrowdStrike with Uncoder AI – Source: socprime.com
Source: socprime.com – Author: Steven Edwards Adversaries frequently repurpose trusted tools like curl.exe to tunnel traffic through SOCKS proxies and even reach .onion domains. Whether it’s...
Detecting Covert curl Usage with Uncoder AI’s Decision Tree in Carbon Black – Source: socprime.com
Source: socprime.com – Author: Steven Edwards When attackers repurpose legitimate binaries like curl.exe to tunnel through SOCKS proxies and access .onion domains, it poses a major...
Disney Slack attack wasn’t Russian protesters, just a Cali dude with malware – Source: go.theregister.com
Source: go.theregister.com – Author: Brandon Vigliarolo When someone stole more than a terabyte of data from Disney last year, it was believed to be the work...
Generative AI makes fraud fluent – from phishing lures to fake lovers – Source: go.theregister.com
Source: go.theregister.com – Author: Iain Thomson RSAC Spam messages predate the web itself, and generative AI has given it a fluency upgrade, churning out slick, localized...
Three Brits charged over ‘active shooter threats’ swattings in US, Canada – Source: go.theregister.com
Source: go.theregister.com – Author: Connor Jones Three young Brits are accused of stateside swatting offences and will appear in a UK court today to face their...
British govt agents step in as Harrods becomes third mega retailer under cyberattack – Source: go.theregister.com
Source: go.theregister.com – Author: Connor Jones Harrods, a globally recognized purveyor of all things luxury, is the third major UK retailer to confirm an attempted cyberattack...
Dems look to close the barn door after top DOGE dog has bolted – Source: go.theregister.com
Source: go.theregister.com – Author: Brandon Vigliarolo Elon Musk is backing away from his Trump-blessed government gig, but now House Democrats want to see the permission slip...
Healthcare group Ascension discloses second cyberattack on patients’ data – Source: go.theregister.com
Source: go.theregister.com – Author: Connor Jones It’s more bad news from Ascension Health which is informing some of its patients, potentially for the second time in...
SpyLoan: A Global Threat Exploiting Social Engineering – Source:www.mcafee.com
Source: www.mcafee.com – Author: McAfee Labs. Authored by: Fernando Ruiz The McAfee mobile research team recently identified a significant global increase of SpyLoan, also known as...
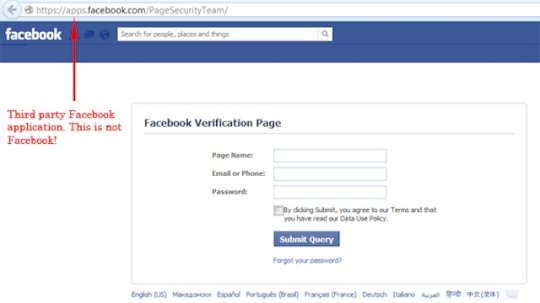
How to Protect Your Social Media Passwords with Multi-factor Verification – Source:www.mcafee.com
Source: www.mcafee.com – Author: Jasdev Dhaliwal. Two-step verification, two-factor authentication, multi-factor authentication…whatever your social media platform calls it, it’s an excellent way to protect your accounts....
How to Protect Your Personal Info – Source:www.mcafee.com
Source: www.mcafee.com – Author: Amy Bunn. Whether it tags along via a smartphone, laptop, tablet, or wearable, it seems like the internet follows us wherever we...
Lumma Stealer on the Rise: How Telegram Channels Are Fueling Malware Proliferation – Source:www.mcafee.com
Source: www.mcafee.com – Author: McAfee Labs. Authored by: M, Mohanasundaram and Neil Tyagi In today’s rapidly evolving cyber landscape, malware threats continue to adapt, employing new...
How to Recognize a Phishing Email – Source:www.mcafee.com
Source: www.mcafee.com – Author: Jasdev Dhaliwal. How do you recognize phishing emails and texts? Even as many of the scammers behind them have sophisticated their attacks,...
How to Protect Your Smartphone from SIM Swapping – Source:www.mcafee.com
Source: www.mcafee.com – Author: Jasdev Dhaliwal. You consider yourself a responsible person when it comes to taking care of your physical possessions. You’ve never left your wallet in...
How to Be Your Family’s Digital IT Hero for the Holidays – Source:www.mcafee.com
Source: www.mcafee.com – Author: Jasdev Dhaliwal. The holiday season often brings a rush of new gadgets—smartphones, tablets, laptops, and smart home devices—into households. One survey revealed...
What is the Dark Web? – Source:www.mcafee.com
Source: www.mcafee.com – Author: Jasdev Dhaliwal. The dark web. The name raises all kinds of questions. What is the dark web, really? Where is it? Can...
200+ Fake Retail Sites Used in New Wave of Subscription Scams – Source:hackread.com
Source: hackread.com – Author: Deeba Ahmed. Bitdefender uncovers a massive surge in sophisticated subscription scams disguised as online shops and evolving mystery boxes. Learn how to...
Cisco IOS XR Software Border Gateway Protocol Confederation Denial of Service Vulnerability – Source:sec.cloudapps.cisco.com
Source: sec.cloudapps.cisco.com – Author: . Cisco IOS XR Software Border Gateway Protocol Confederation Denial of Service Vulnerability Medium CVE-2025-20115 CWE-120 Download CSAF Email Summary A vulnerability...
Cisco IOS XR Software Image Verification Bypass Vulnerability – Source:sec.cloudapps.cisco.com
Source: sec.cloudapps.cisco.com – Author: . Cisco IOS XR Software Image Verification Bypass Vulnerability High CVE-2025-20177 CWE-274 Download CSAF Email Summary A vulnerability in the boot process...
Microsoft sets all new accounts passwordless by default – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Microsoft announced that all new accounts will be “passwordless by default” to increase their level of security. Microsoft now makes...
Luxury department store Harrods suffered a cyberattack – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Harrods confirmed a cyberattack, following similar incidents suffered by M&S and Co-op, making it the third major UK retailer targeted...
U.S. CISA adds SonicWall SMA100 and Apache HTTP Server flaws to its Known Exploited Vulnerabilities catalog – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini U.S. Cybersecurity and Infrastructure Security Agency (CISA) adds SonicWall SMA100 and Apache HTTP Server flaws to its Known Exploited Vulnerabilities...