Source: socprime.com – Author: Daryna Olyniychuk Gartner’s Top Cybersecurity Trends of 2025 report emphasizes the growing influence of generative AI (GenAI), highlighting new opportunities for organizations...
Day: May 15, 2025
Google’s Advanced Protection Now on Android – Source: www.schneier.com
Source: www.schneier.com – Author: Bruce Schneier HomeBlog Comments Steve67 • May 14, 2025 7:35 AM They are adopting features that already exist in GrapheneOS, such as...
Smashing Security podcast #417: Hello, Pervert! – Sextortion scams and Discord disasters – Source: grahamcluley.com
Source: grahamcluley.com – Author: Graham Cluley Skip to content Don’t get duped, doxxed, or drained! In this episode of “Smashing Security” we dive into the creepy...
New Chrome Vulnerability Enables Cross-Origin Data Leak via Loader Referrer Policy – Source:thehackernews.com
Source: thehackernews.com – Author: . Google on Wednesday released updates to address four security issues in its Chrome web browser, including one for which it said...
RaaS Explained: How Cybercriminals Are Scaling Attacks Like Startups – Source:hackread.com
Source: hackread.com – Author: Owais Sultan. There is a lot of money in cyberattacks like ransomware, and unfortunately for organizations of all sizes, the cybercrime business...
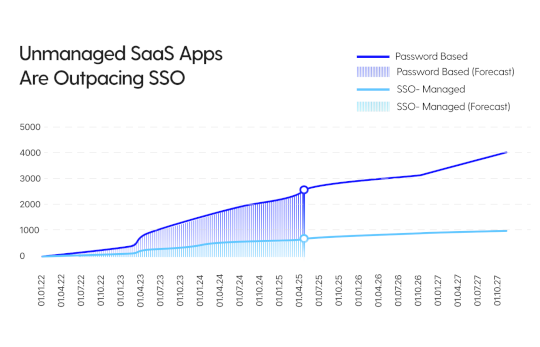
5 Identity Security Risks We Found in a Regulated Enterprise – Source: securityboulevard.com
Source: securityboulevard.com – Author: Grip Security Blog Even the most mature enterprises encounter new, subtle, and complex identity security challenges from the rapid growth of SaaS....
Stay Relaxed with Efficient Non-Human Identity Security – Source: securityboulevard.com
Source: securityboulevard.com – Author: Alison Mack Are You Safe With Your Current Non-Human Identity Security? The migration of services to the cloud promises flexibility, scalability, and...
Continuous Improvement in NHIs Management – Source: securityboulevard.com
Source: securityboulevard.com – Author: Alison Mack Can Continuous Improvement in NHIs Management Be the Key to Securing Your Operations? You’re no stranger to the importance of...
Building Trust Through Secure NHIs Practices – Source: securityboulevard.com
Source: securityboulevard.com – Author: Alison Mack How Can We Cultivate Trust with Secure NHIs Practices? When we navigate in increased digital interconnection, establishing trust in cybersecurity...
Cultivate Independent Secrets Management Protocols – Source: securityboulevard.com
Source: securityboulevard.com – Author: Alison Mack Why is Independent Secrets Management Crucial for Cybersecurity? How crucial do you believe independent secrets management is to your organization’s...
Implementing a SCIM API for Your Application: A Comprehensive Guide – Source: securityboulevard.com
Source: securityboulevard.com – Author: Devesh Patel Introduction: Why Your App Needs SCIM Yesterday Picture this: Your B2B SaaS product has finally landed that enterprise client you’ve...
BSidesLV24 – GroundFloor – A Quick Story Of Security Pitfalls With Exec Commands In Software Integrations – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman Home » Security Bloggers Network » BSidesLV24 – GroundFloor – A Quick Story Of Security Pitfalls With Exec Commands In...
SSOJet LLM-Friendly Documentation – Source: securityboulevard.com
Source: securityboulevard.com – Author: Ankit Agarwal Make SSOJet’s API documentation accessible and easy to understand for large language models like ChatGPT, Claude, GitHub Copilot, Cursor, and...
Hacking the Hardware Brains of Computers is the Ultimate Cyberattack – Source: securityboulevard.com
Source: securityboulevard.com – Author: Matthew Rosenquist Compromising the hardware layer, especially the CPU, is the Holy Grail of cyberattacks. Recent work by Christiaan Beek, a leading...
Randall Munroe’s XKCD ‘Deposition’ – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman Thursday, May 15, 2025 Security Boulevard The Home of the Security Bloggers Network Community Chats Webinars Library Home Cybersecurity News...
Cisco Catalyst SD-WAN Manager Arbitrary File Creation Vulnerability – Source:sec.cloudapps.cisco.com
Source: sec.cloudapps.cisco.com – Author: . Cisco Catalyst SD-WAN Manager Arbitrary File Creation Vulnerability Medium CVE-2025-20187 CWE-22 Download CSAF Email Summary A vulnerability in the application data...
Cisco IOS Software for Cisco Catalyst 2960X, 2960XR, 2960CX, and 3560CX Series Switches Secure Boot Bypass Vulnerability – Source:sec.cloudapps.cisco.com
Source: sec.cloudapps.cisco.com – Author: . Cisco IOS Software for Cisco Catalyst 2960X, 2960XR, 2960CX, and 3560CX Series Switches Secure Boot Bypass Vulnerability High CVE-2025-20181 CWE-347 Download...