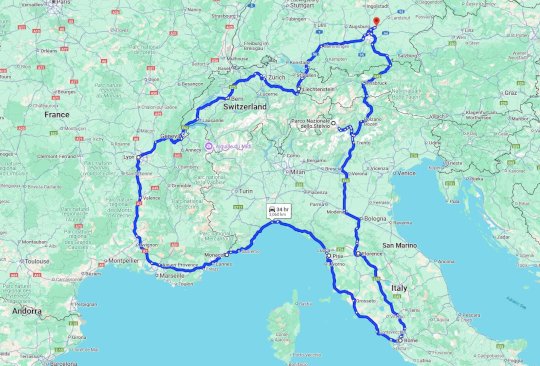
Source: www.troyhunt.com – Author: Troy Hunt I love a good road trip. Always have, but particularly during COVID when international options were somewhat limited, one road...
Day: May 2, 2025
PsyOps of Phishing: A Wolf in Shepherd’s Clothing – Source: securityboulevard.com
Source: securityboulevard.com – Author: Chris I am sure all of us have encountered CAPTCHA while browsing the internet. “Verify you are human”, “I’m not a robot”,...
Tonic.ai product updates: May 2025 – Source: securityboulevard.com
Source: securityboulevard.com – Author: Expert Insights on Synthetic Data from the Tonic.ai Blog We’re excited to share the latest updates and announcements designed to improve your...
Application-Layer Visibility and Security | Contrast ADR vs Traditional Tools | Contrast Security – Source: securityboulevard.com
Source: securityboulevard.com – Author: Contrast Marketing Imagine you’re a lifeguard at a beach, but you’re only allowed to watch from a helicopter or from a camera...
BSidesLV24 – Ground Truth – AI In The Human Loop: GenAI In Security Service Delivery – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman Home » Security Bloggers Network » BSidesLV24 – Ground Truth – AI In The Human Loop: GenAI In Security Service...
The organizational structure of ransomware threat actor groups is evolving before our eyes – Source: securityboulevard.com
Source: securityboulevard.com – Author: Bill Siegel Table of Contents Ransomware Evolution Payment Rates Types of Ransomware Attack Vectors TTPs Victimology As we approach the one year...
Kubernetes Resource Optimization & Best Practices with Goldilocks – Source: securityboulevard.com
Source: securityboulevard.com – Author: Andy Suderman Kubernetes is now the industry standard for orchestrating containerized workloads, but efficient resource management remains a challenge for many organizations....
The Rise of AI-Driven Cyberattacks: Accelerated Threats Demand Predictive and Real-Time Defenses – Source: securityboulevard.com
Source: securityboulevard.com – Author: MixMode Threat Research MixMode Threat Research MixMode Threat Research is a dedicated contributor to MixMode.ai’s blog, offering insights into the latest advancements and...
Vulnerability Management: A Race Against Time & Complexity – Source: securityboulevard.com
Source: securityboulevard.com – Author: Maycie Belmore One of the cornerstones of robust security is an effective vulnerability management process, which involves identifying, assessing, and mitigating risks...
Report Exposes Soft Security Underbelly of Mobile Computing – Source: securityboulevard.com
Source: securityboulevard.com – Author: Michael Vizard Zimperium, this week during the 2025 RSA Conference, shared an analysis of mobile computing environments that finds more than 60%...
BSidesLV24 – Ground Truth – I Won’t Allow My Child To Have A Smartphone: Why Smart Parents Make Not So Smart Children – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman Home » Security Bloggers Network » BSidesLV24 – Ground Truth – I Won’t Allow My Child To Have A Smartphone:...
McAfee Shines at CES 2025: Redefining AI Protection for All – Source:www.mcafee.com
Source: www.mcafee.com – Author: Jasdev Dhaliwal. As CES kicks off in Las Vegas, McAfee proudly stands at the forefront of innovation, showcasing our leadership in AI...
State of the Scamiverse – How AI is Revolutionizing Online Fraud – Source:www.mcafee.com
Source: www.mcafee.com – Author: Jasdev Dhaliwal. For less than the cost of a latte and in under 10 minutes, scammers today can create shockingly convincing deepfake...
Spyware distributed through Amazon Appstore – Source:www.mcafee.com
Source: www.mcafee.com – Author: McAfee Labs. Authored by Wenfeng Yu and ZePeng Chen As smartphones have become an integral part of our daily lives, malicious apps...
The Stealthy Stalker: Remcos RAT – Source:www.mcafee.com
Source: www.mcafee.com – Author: McAfee Labs. Authored By Sakshi Jaiswal, Anuradha M In Q3 2024, McAfee Labs identified a sharp rise in the Remcos RAT threat....
How to Protect Your Data While On-the-Go – Source:www.mcafee.com
Source: www.mcafee.com – Author: Jasdev Dhaliwal. Winter travel is filled with excitement—whether you’re heading to a snow-covered ski resort, visiting family for the holidays, or enjoying...
2024 Data Breaches Wrapped – Source:www.mcafee.com
Source: www.mcafee.com – Author: Jasdev Dhaliwal. It’s been a big year for big data breaches. Billions of records on millions of people have been exposed at...
How to Detect Signs of Identity Theft – Source:www.mcafee.com
Source: www.mcafee.com – Author: Amy Bunn. When it comes to identity theft, trust your gut when something doesn’t feel right. Follow up. What you’re seeing could be a problem. A missing bill or a mysterious charge on...
How to Delete Yourself from the Internet – Source:www.mcafee.com
Source: www.mcafee.com – Author: Jasdev Dhaliwal. While you can’t delete your personal info from the internet entirely, you can take strong steps to remove it from...
MY TAKE: RSAC 2025 – Conversing with vendors hanging out in the Marriott Marquis mezzanine – Source: www.lastwatchdog.com
Source: www.lastwatchdog.com – Author: bacohido By Byron V. Acohido SAN FRANCISCO — Sometimes, the best insights come not from the keynote stage, but from the hotel...
xAI Dev Leaks API Key for Private SpaceX, Tesla LLMs – Source: krebsonsecurity.com
Source: krebsonsecurity.com – Author: BrianKrebs An employee at Elon Musk’s artificial intelligence company xAI leaked a private key on GitHub that for the past two months could...
Cisco IOS XR Software Secure Boot Bypass Vulnerability – Source:sec.cloudapps.cisco.com
Source: sec.cloudapps.cisco.com – Author: . Cisco IOS XR Software Secure Boot Bypass Vulnerability High CVE-2025-20143 CWE-347 Download CSAF Email Summary A vulnerability in the boot process...
Cisco IOS XR Software Release 7.9.2 Denial of Service Vulnerability – Source:sec.cloudapps.cisco.com
Source: sec.cloudapps.cisco.com – Author: . Cisco IOS XR Software Release 7.9.2 Denial of Service Vulnerability High CVE-2025-20141 CWE-770 Download CSAF Email Summary A vulnerability in the...