Source: securityboulevard.com – Author: Devin Partida Adopting cloud computing allows organizations of all shapes and sizes to access data and collaborate in the most flexible ways...
Day: April 29, 2025
RSA Conference Dispatch: Mr. NHI – Leading the Movement to Expose Cybersecurity’s Biggest Blind Spot! – Source: securityboulevard.com
Source: securityboulevard.com – Author: John D. Boyle When you meet Lalit Choda, known across the cybersecurity industry as “Mr. NHI,” one word immediately comes to mind:...
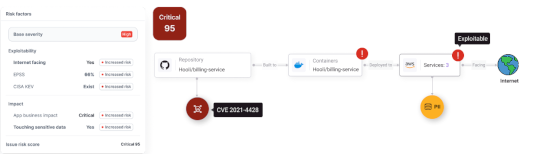
Announcing New Legit ASPM AI Capabilities – Source: securityboulevard.com
Source: securityboulevard.com – Author: Liav Caspi Get details on Legit’s new AI capabilities. Developers are increasingly leveraging AI to build faster and smarter. Its use has...
News alert: Case dismissed against VPN executive, affirms no-logs policy as a valid legal defense – Source: securityboulevard.com
Source: securityboulevard.com – Author: cybernewswire Toronto, Canada, Apr. 28, 2025, CyberNewswire — Windscribe, a globally used privacy-first VPN service, announced today that its founder, Yegor Sak,...
Your NHIDR Is Getting Better—How? – Source: securityboulevard.com
Source: securityboulevard.com – Author: Alison Mack Why Does Improving Non-Human Identity and Data Response (NHIDR) Matter? How often do we consider the impact of Non-Human Identities...
Harnessing Powerful Tools for Secrets Scanning – Source: securityboulevard.com
Source: securityboulevard.com – Author: Amy Cohn Capturing the Essence of Powerful Secrets Scanning Wondering how to enhance your organization’s cybersecurity measures? Among the vast spectrum of...
Certain Your Data Is Safe in the Cloud? – Source: securityboulevard.com
Source: securityboulevard.com – Author: Amy Cohn Are You Confident Your Data Safety Measures Are Up to Scratch? The rise of digital transformation is not without its...
BSidesLV24 – Ground Truth – PhishDefend: A Reinforcement Learning Framework – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman Home » Security Bloggers Network » BSidesLV24 – Ground Truth – PhishDefend: A Reinforcement Learning Framework Author/Presenter: Bobby Filar Our...
Bugcrowd Launches Red Team Service to Test Cybersecurity Defenses – Source: securityboulevard.com
Source: securityboulevard.com – Author: Michael Vizard Bugcrowd today at the 2025 RSA Conference announced its intent to create a red team service to test cybersecurity defenses...
Blackpoint Cyber Extends MDR Service to Improve Cyber Resiliency – Source: securityboulevard.com
Source: securityboulevard.com – Author: Michael Vizard Blackpoint Cyber today at the 2025 RSA Conference unveiled a unified security posture and response platform that is based on...
African Telecom Giant MTN Group Discloses Data Breach – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ionut Arghire MTN Group, one of the largest telecommunications services providers in Africa, says the personal information of some customers was compromised...