Source: www.darkreading.com – Author: Robert Lemos, Contributing Writer Please enable cookies. Sorry, you have been blocked You are unable to access darkreading.com Why have I been...
Day: April 1, 2025
Google Brings End-to-End Encryption to Gmail – Source: www.darkreading.com
Source: www.darkreading.com – Author: Jeffrey Schwartz Please enable cookies. Sorry, you have been blocked You are unable to access darkreading.com Why have I been blocked? This...
Surge in Scans on PAN GlobalProtect VPNs Hints at Attacks – Source: www.darkreading.com
Source: www.darkreading.com – Author: Jai Vijayan, Contributing Writer Please enable cookies. Sorry, you have been blocked You are unable to access darkreading.com Why have I been...
As CISA Downsizes, Where Can Enterprises Get Support? – Source: www.darkreading.com
Source: www.darkreading.com – Author: Alexander Culafi, Senior News Writer, Dark Reading Please enable cookies. Sorry, you have been blocked You are unable to access darkreading.com Why...
Japan Bolsters Cybersecurity Safeguards With Cyber Defense Bill – Source: www.darkreading.com
Source: www.darkreading.com – Author: Kristina Beek, Associate Editor, Dark Reading Please enable cookies. Sorry, you have been blocked You are unable to access darkreading.com Why have...
Check Point Disputes Hacker’s Breach Claims – Source: www.darkreading.com
Source: www.darkreading.com – Author: Kristina Beek, Associate Editor, Dark Reading Please enable cookies. Sorry, you have been blocked You are unable to access darkreading.com Why have...
Google ‘ImageRunner’ Bug Enabled Privilege Escalation – Source: www.darkreading.com
Source: www.darkreading.com – Author: Alexander Culafi, Senior News Writer, Dark Reading Please enable cookies. Sorry, you have been blocked You are unable to access darkreading.com Why...
FDA’s Critical Role in Keeping Medical Devices Secure – Source: www.darkreading.com
Source: www.darkreading.com – Author: Morey J. Haber Please enable cookies. Sorry, you have been blocked You are unable to access darkreading.com Why have I been blocked?...
Lazarus APT Jumps on ClickFix Bandwagon in Recent Attacks – Source: www.darkreading.com
Source: www.darkreading.com – Author: Elizabeth Montalbano, Contributing Writer Please enable cookies. Sorry, you have been blocked You are unable to access darkreading.com Why have I been...
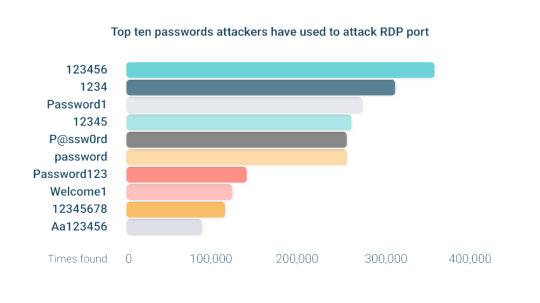
Top 10 Most-Used RDP Passwords Are Not Complex Enough – Source: www.darkreading.com
Source: www.darkreading.com – Author: Arielle Waldman Please enable cookies. Sorry, you have been blocked You are unable to access darkreading.com Why have I been blocked? This...
Trend Micro Open Sources AI Tool Cybertron – Source: www.darkreading.com
Source: www.darkreading.com – Author: Arielle Waldman Please enable cookies. Sorry, you have been blocked You are unable to access darkreading.com Why have I been blocked? This...
The AI Fix #44: AI-generated malware, and a stunning AI breakthrough – Source: grahamcluley.com
Source: grahamcluley.com – Author: Graham Cluley In episode 44 of The AI Fix, ChatGPT won’t build a crystal meth lab, GPT-4o improves the show’s podcast art,...
Hackers exploit little-known WordPress MU-plugins feature to hide malware – Source: www.bitdefender.com
Source: www.bitdefender.com – Author: Graham Cluley A new security issue is putting WordPress-powered websites at risk. Hackers are abusing the “Must-Use” plugins (MU-plugins) feature to hide...
Gamaredon Campaign Detection: russia-backed APT Group Targets Ukraine Using LNK Files to Spread Remcos Backdoor – Source: socprime.com
Source: socprime.com – Author: Veronika Telychko The russia-linked Gamaredon APT notorious for a wealth of cyber-offensive operations against Ukraine resurfaces in the cyber threat arena. The...
Download the Strategizing Data Analytics for AI Enterprise Spotlight – Source: us.resources.csoonline.com
Source: us.resources.csoonline.com – Author: Register Download the April 2025 issue of the Enterprise Spotlight from the editors of CIO, Computerworld, CSO, InfoWorld, and Network World. See...
Altgeräte bedrohen Sicherheit in Unternehmen – Source: www.csoonline.com
Source: www.csoonline.com – Author: Eine Studie legt nahe, dass veraltete Netzgeräte ein massives Problem für die Cybersicherheit darstellen und schnellstmöglich ersetzt werden sollten. Schwachstellen in alten...
Oracle warns customers of health data breach amid public denial – Source: www.csoonline.com
Source: www.csoonline.com – Author: Oracle continues to publicly deny two separate data breaches despite emerging evidence of the breaches. Oracle’s healthcare subsidiary, Oracle Health, has suffered...
LLMs are now available in snack size but digest with care – Source: www.csoonline.com
Source: www.csoonline.com – Author: Distilled models can improve the contextuality and accessibility of LLMs, but can also amplify existing AI risks, including threats to data privacy,...
After fake employees, fake enterprises are next hiring threat to corporate data – Source: www.computerworld.com
Source: www.computerworld.com – Author: news Mar 31, 20254 mins HiringSecurityTechnology Industry In Taiwan, investigators raided businesses they say acted as fronts for Chinese companies to hire...
Infostealer malware poses potent threat despite recent takedowns – Source: www.csoonline.com
Source: www.csoonline.com – Author: News Analysis 01 Apr 20255 mins Data and Information SecurityMalwareRansomware Law enforcement action has failed to dent the impact of infostealer malware,...
6 hard-earned tips for leading through a cyberattack — from CSOs who’ve been there – Source: www.csoonline.com
Source: www.csoonline.com – Author: When a cyberattack strikes, security leaders must go beyond the incident response plan to ensure holistic preparation, effective collaboration, and strong leadership...
7 Wege, Daten (besser) zu verschlüsseln – Source: www.csoonline.com
Source: www.csoonline.com – Author: Diese Encryption-Techniken stärken nicht nur das Datenschutzniveau – sie können auch dazu beitragen, neue Denkansätze zu entwickeln. Verschlüsseln Sie Ihre Daten zeitgemäß?...
Volume of attacks on network devices shows need to replace end of life devices quickly – Source: www.csoonline.com
Source: www.csoonline.com – Author: Cisco report reveals two of the three top vulnerabilities attackers went after in 2024 were in old network devices. Two of the...
Happy 21st Birthday, Gmail! Google’s Present to Enterprise Gmail Users: End-to-End Encryption – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: Fiona Jackson Image: Google All enterprise users of Gmail can now easily apply end-to-end encryption to their emails. Prior to today, this...
Cell Phone OPSEC for Border Crossings – Source: www.schneier.com
Source: www.schneier.com – Author: Bruce Schneier I have heard stories of more aggressive interrogation of electronic devices at US border crossings. I know a lot about...
Celebrating Women in Engineering in the Arab World
For National Arab American Heritage Month, SWE recognizes some of the Arab women engineers making their mark in the industry. Source Views: 1
Guiding the Future: The SWE Section Election Manual
Explore this new resource that helps SWE Sections select future leaders. Source Views: 2
How Mechanical Engineer Michelle Johnston Returned to Work After a Career Break
After a 14-year career break, Michelle Johnston returned to the engineering workforce after meeting her employer at the WE22 Career Fair! Read her story and learn...
Engineering Careers in Hair Care: Meet Maxine Tomlinson
As a Senior Scientist in R&D at Henkel, Maxine shares her unique career journey and discusses career paths in the personal care industry for engineers. Source...
SWE Diverse Podcast Ep 227: Un Cafecito With a Woman in STEM: Dr. Justina Sanchez
Celebrate Hispanic Heritage Month with our new podcast interview with Dr. Justina Sanchez and Lennis Perez! Source Views: 0