Source: www.csoonline.com – Author: Feature 12 Mar 20257 mins RansomwareSecurityThreat and Vulnerability Management Fresh cybercrime threats are emerging from rebranded, leaked, or purchased code, as data...
Day: March 12, 2025
Was CISOs von Moschusochsen lernen können – Source: www.csoonline.com
Source: www.csoonline.com – Author: Der “Moschusochsen-Ansatz” kann Sicherheitsentscheider in Sachen Drittanbieter-Risikomanagement entscheidend voranbringen. Von Moschusochsen können sich CISOs eine Scheibe abschneiden – wenn es nach unserem...
Microsoft patches privilege escalation flaw exploited since 2023 – Source: www.csoonline.com
Source: www.csoonline.com – Author: The privilege escalation flaw in the Win23k driver affects older versions of Windows and is one of six zero-day vulnerabilities fixed by...
March Patch Tuesday warnings: Act fast to plug zero day holes in Windows, VMware – Source: www.csoonline.com
Source: www.csoonline.com – Author: Note also that apps using OpenSSH have to be patched to close a decade-old hole. CISOs need to lean on their admins...
Ivanti EPM vulnerabilities actively exploited in the wild, CISA warns – Source: www.csoonline.com
Source: www.csoonline.com – Author: Three of the four critical path traversal flaws fixed in January in Ivanti Endpoint Manager are being exploited in cyberattacks after proof-of-concept...
Google paid nearly $12 million to bug hunters last year – Source: www.csoonline.com
Source: www.csoonline.com – Author: The company says it has paid out over $65 million since its bug hunting program started. Google announced it has paid out $11.8 million...
How to Use NordPass: A Step-by-Step Guide – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: Luis Millares NordPass, Nord Security’s password manager, is an intuitive application offering reliable password storage and protection. In this article, we walk...
Webinar: Credential security in the age of AI: Insights for IT leaders – Source: grahamcluley.com
Source: grahamcluley.com – Author: Graham Cluley Skip to content Fireside chat with Graham Cluley about credential security in the age of AI Make a note in...
UK Cybersecurity Sector Revenue Grows 12% to Top £13bn – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: The UK’s cybersecurity industry demonstrated “exceptional performance” in the past financial year, increasing total revenue by 12% to reach £13.2bn, according to...
Blind Eagle Targets Colombian Government with Malicious .url Files – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: A new cyber-threat campaign targeting Colombian government institutions and organizations since November 2024 has been linked to the threat group Blind Eagle, also...
New York Sues Allstate Over Data Breach and Security Failures – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: New York attorney general, Letitia James, has filed a lawsuit against Allstate’s National General unit, alleging the company failed to adequately protect...
CVE-2025-27840: Vulnerability Exploitation in Espressif ESP32 Bluetooth Chips Can Lead to Unauthorized Access to Devices – Source: socprime.com
Source: socprime.com – Author: Veronika Telychko Following the disclosure of an authorization bypass vulnerability in the Motorola Mobility Droid Razr HD (Model XT926), another major security...
SOC Prime Announces Referral Program for Individual Cyber Defenders – Source: socprime.com
Source: socprime.com – Author: Daryna Olyniychuk Invite Your Peers, Get 20% Off SOC Prime Platform Solo Subscriptions At SOC Prime, we foster a strong cybersecurity community...
Silk Typhoon Hackers Indicted – Source: www.schneier.com
Source: www.schneier.com – Author: Bruce Schneier Lots of interesting details in the story: The US Department of Justice on Wednesday announced the indictment of 12 Chinese...
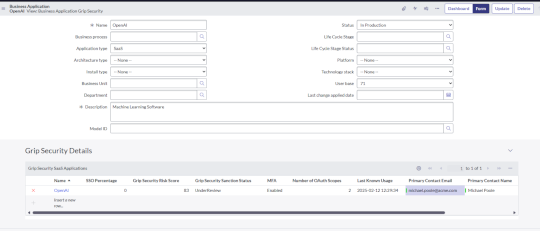
Unlock the Power of ServiceNow CMDB with Grip Security – Source: securityboulevard.com
Source: securityboulevard.com – Author: Grip Security Blog Managing IT assets is already a complex challenge, but keeping track of SaaS applications—especially shadow SaaS—makes it even more...
How the EU Product Liability Directive (EU PLD) is Changing Software Security | Contrast Security – Source: securityboulevard.com
Source: securityboulevard.com – Author: Contrast Marketing Companies that sell software that can be used or downloaded by anyone in the European Union are facing a major...
News alert: GitGuardian discloses 70% of leaked secrets remain active 2 years — remediation urgent – Source: securityboulevard.com
Source: securityboulevard.com – Author: cybernewswire Boston, Mass., Mar. 11, 2025, CyberNewswire — GitGuardian, the security leader behind GitHub’s most installed application, today released its comprehensive “2025...
BSides Exeter 2024 – Purple Track – Exercise Army Cyber Spartan – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman Wednesday, March 12, 2025 Home » Promo » Cybersecurity » BSides Exeter 2024 – Purple Track – Exercise Army Cyber...
Lessons from the Field, Part III: Why Backups Alone Won’t Save You – Source: securityboulevard.com
Source: securityboulevard.com – Author: hmeyers James Keiser, Director of Secured Managed Services Southeast, CISO Global, Inc. March 11, 2025 It’s been a while since I’ve put...
Microsoft’s March 2025 Patch Tuesday Addresses 56 CVEs (CVE-2025-26633, CVE-2025-24983, CVE-2025-24993) – Source: securityboulevard.com
Source: securityboulevard.com – Author: Tenable Security Response Team 6Critical 50Important 0Moderate 0Low Microsoft addresses 56 CVEs, including seven zero-day flaws, with six of those being exploited...
Silk Typhoon Hackers Indicted – Source: securityboulevard.com
Source: securityboulevard.com – Author: Bruce Schneier Lots of interesting details in the story: The US Department of Justice on Wednesday announced the indictment of 12 Chinese...
Randall Munroe’s XKCD ‘Tall Structures’ – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman via the comic humor & dry wit of Randall Munroe, creator of XKCD Permalink *** This is a Security Bloggers...
AlgoSec and ColorTokens: Integrated to Stop Cyberattacks in Every Direction – Source: securityboulevard.com
Source: securityboulevard.com – Author: Bob Palmer There are two vectors that hackers use to attack your enterprise. One is characterized as the North-South vector, which describes...
News alert: GitGuardian discloses 70% of leaked secrets remain active 2 years — remediation urgent – Source: www.lastwatchdog.com
Source: www.lastwatchdog.com – Author: cybernewswire Boston, Mass., Mar. 11, 2025, CyberNewswire — GitGuardian, the security leader behind GitHub’s most installed application, today released its comprehensive “2025...
News alert: 360 Privacy secures $36M to deliver turnkey digital executive protection platform – Source: www.lastwatchdog.com
Source: www.lastwatchdog.com – Author: bacohido Nashville, TN – Mar. 11, 2025 – 360 Privacy, a leading digital executive protection platform, today announced that it has secured a $36...