Dr. Meredith L. Dyck of the National Security Agency shares lessons from her career as a physicist, including her personal experiences with caregiving and work-life balance,...
Day: February 20, 2025
Joint Membership: Diversity, Equity, Inclusion, and Belonging (DEI&B) Beyond SWE
Learn how SWE is providing access for members to hold joint membership with other DEI&B professional societies. Source Views: 0
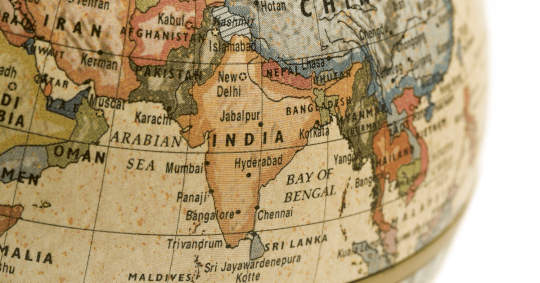
The Current Status and Path Forward of Women Engineers in India
In honor of International Women in Engineering Day, Swastika Chatterjee Das dives into the data on gender representation in senior leadership roles in manufacturing and heavy...
SWE Celebrates International Women in Engineering Day (INWED)
Explore the stories of women engineers from around the world with these magazine articles, blog posts, and podcast interviews. Source Views: 1
Promote SWE’s Goals on a Local Level in Your State
Public Policy Affinity Group (AG) member and SWE Fellow Jan Williams provides tips for those interested in shaping public policy in their area and beyond. Source...
Darktrace: 96% of Phishing Attacks in 2024 Exploited Trusted Domains Including SharePoint & Zoom Docs – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: Fiona Jackson Threat actors are increasingly targeting trusted business platforms such as Dropbox, SharePoint, and QuickBooks in their phishing email campaigns and...
Duo vs Microsoft Authenticator: Which Tool Is Better? – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: Luis Millares We may earn from vendors via affiliate links or sponsorships. This might affect product placement on our site, but not...
DEF CON 32 – Dysfunctional Unity: The Road To Nowhere – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman Wednesday, February 19, 2025 Home » Security Bloggers Network » DEF CON 32 – Dysfunctional Unity: The Road To Nowhere...
Migrating from kOps to EKS: A Technical Guide for When & Why to Switch – Source: securityboulevard.com
Source: securityboulevard.com – Author: Abdul Akhter As Kubernetes continues to mature, so do the tools we use to manage it. In this blog post, we’ll explore...
Randall Munroe’s XKCD ‘Archive Request’ – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman via the comic humor & dry wit of Randall Munroe, creator of XKCD Permalink *** This is a Security Bloggers...
From Defense to Offense: Inside-Out Data Security Strategies for CISOs in 2025 – Source: securityboulevard.com
Source: securityboulevard.com – Author: Anuj Jaiswal As organizations continue to generate and store colossal volumes of data — everything from customer records to intellectual property —...
Your Social Security Number is on the Dark Web: What Do You Do? – Source: securityboulevard.com
Source: securityboulevard.com – Author: Bogdan Botezatu If you’re worried about your Social Security number being shopped on the dark web, where cybercriminals go to buy and...
News alert: INE Security’s focus on practical security training enhances career stability in tech – Source: securityboulevard.com
Source: securityboulevard.com – Author: cybernewswire Cary, NC, Feb. 19, 2025, CyberNewswire — 2025 marks a time of unprecedented volatility in the technology job market. On one...
DEF CON 32 – MoWireless MoProblems: Modular Wireless Survey Sys. & Data Analytics – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman Wednesday, February 19, 2025 Home » Security Bloggers Network » DEF CON 32 – MoWireless MoProblems: Modular Wireless Survey Sys....
CaaS Surges in 2025, Along With RATs, Ransomware – Source: securityboulevard.com
Source: securityboulevard.com – Author: Nathan Eddy Cybercrime-as-a-Service (CaaS) now accounts for 57% of all cyberthreats, marking a 17% increase from the first half of 2024, according...
Securing multi-environment deployments: Cloud, on-premise, and air-gapped – Source: securityboulevard.com
Source: securityboulevard.com – Author: Aaron Linskens Modern software delivery makes use of many different deployment environments, from public cloud to private cloud and traditional on-premise data...
Flaws in Xerox VersaLink MFPs Spotlight Printer Security Concerns – Source: securityboulevard.com
Source: securityboulevard.com – Author: Jeffrey Burt Security flaws found in Xerox VersaLink C7025 multifunction printers (MFPs) could allow attackers to grab authentication credentials, which would pave...