Source: www.securityweek.com – Author: Etay Maor The era of “agentic” artificial intelligence has arrived, and businesses can no longer afford to overlook its transformative potential. AI...
Day: February 19, 2025
CISO Conversations: Kevin Winter at Deloitte and Richard Marcus at AuditBoard – Source: www.securityweek.com
Source: www.securityweek.com – Author: Kevin Townsend Deloitte is one of the largest professional services firms in the world, providing services in audit, consulting, financial advisory, risk...
Blockaid Raises $50 Million to Secure Blockchain Applications – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ionut Arghire Blockchain application security startup Blockaid on Tuesday announced raising $50 million in a Series B funding round that brings the...
OpenSSH Patches Vulnerabilities Allowing MitM, DoS Attacks – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ionut Arghire On Tuesday, the developers of OpenSSH, the popular open source implementation of the Secure Shell (SSH) protocol, rolled out patches...
VC Firm Insight Partners Hacked – Source: www.securityweek.com
Source: www.securityweek.com – Author: Eduard Kovacs Private equity and venture capital company Insight Partners revealed on Tuesday that it was recently targeted in a cyberattack that...
Chrome 133, Firefox 135 Updates Patch High-Severity Vulnerabilities – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ionut Arghire Google and Mozilla on Tuesday announced fresh security updates for Chrome 133 and Firefox 135 to address high-severity memory safety...
New FrigidStealer macOS Malware Distributed as Fake Browser Update – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ionut Arghire A newly identified information stealer malware targeting macOS users is being distributed through a compromised website as a browser update,...
Free Diagram Tool Aids Management of Complex ICS/OT Cybersecurity Decisions – Source: www.securityweek.com
Source: www.securityweek.com – Author: Eduard Kovacs Admeritia has announced the availability of a new tool designed to help organizations manage complex cybersecurity decisions related to industrial...
Device Code Phishing – Source: www.schneier.com
Source: www.schneier.com – Author: Bruce Schneier This isn’t new, but it’s increasingly popular: The technique is known as device code phishing. It exploits “device code flow,”...
The AI Fix #37: DeepSeek is a security dumpster fire, and quicksand for AI – Source: grahamcluley.com
Source: grahamcluley.com – Author: Graham Cluley Skip to content In episode 37 of “The AI Fix”, Google Gemini gets the munchies, the wettest country in the...
Spam and phishing in 2024 – Source: securelist.com
Source: securelist.com – Author: Tatyana Kulikova, Olga Svistunova, Roman Dedenok, Andrey Kovtun, Irina Shimko, Anna Lazaricheva The year in figures 27% of all emails sent worldwide...
Patch Now: CISA Warns of Palo Alto Flaw Exploited in the Wild – Source: www.darkreading.com
Source: www.darkreading.com – Author: Elizabeth Montalbano, Contributing Writer Source: Chiew via Shutterstock Attackers are actively exploiting an authentication bypass flaw found in the Palo Alto Networks...
What Is the Board’s Role in Cyber-Risk Management in OT Environments? – Source: www.darkreading.com
Source: www.darkreading.com – Author: John Cusimano John Cusimano, Vice President, OT Security, Armexa February 19, 2025 4 Min Read Source: Lev Dolgachov via Alamy Stock Photo...
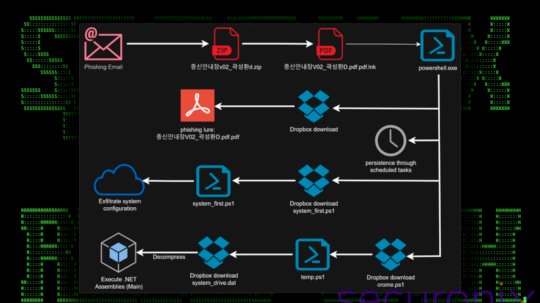
North Korea’s Kimsuky Taps Trusted Platforms to Attack South Korea – Source: www.darkreading.com
Source: www.darkreading.com – Author: Robert Lemos, Contributing Writer North Korea-linked threat groups are increasingly using living-off-the-land (LotL) techniques and trusted services to evade detection, with a...
Deepwatch Acquires Dassana to Boost Cyber-Resilience With AI – Source: www.darkreading.com
Source: www.darkreading.com – Author: Dark Reading Staff Source: Gajus via Adobe Stock Photo NEWS BRIEF Deepwatch, an artificial intelligence (AI) and human cyber-resilience platform provider, has...
CVE-2025-26465 & CVE-2025-26466 Vulnerabilities Expose Systems to Man-in-the-Middle and DoS Attacks – Source: socprime.com
Source: socprime.com – Author: Veronika Telychko Two newly uncovered security flaws in the open-source OpenSSH suite tracked as CVE-2025-26465 and CVE-2025-26466 could enable adversaries to launch...
Spies Eye AUKUS Nuclear Submarine Secrets, Australia’s Intelligence Chief Warns – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: Several countries are “relentlessly” seeking information about Australia’s military capabilities, including the country’s submarine partnership with the UK and the US, warned...
Cyber Investor Insight Partners Suffers Security Breach – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: New York-based venture capital firm Insight Partners has confirmed it was hit by a cyber-attack in January 2025. In a public statement...
Hackers gain root access to Palo Alto firewalls through chained bugs – Source: www.csoonline.com
Source: www.csoonline.com – Author: A recently disclosed medium-severity bug was chained with critical, older bugs to gain root-level access to PAN firewall systems. A high-severity authentication...
Mehrheit der Deutschen fürchtet sich vor Cyberangriffen – Source: www.csoonline.com
Source: www.csoonline.com – Author: Hacker-Attacken aus dem Ausland, zerstörte Strom- und Datenkabel in der Ostsee, Angriffe auf die kritische Infrastruktur. Eine Reihe von Vorfällen dieser Art...
Think being CISO of a cybersecurity vendor is easy? Think again – Source: www.csoonline.com
Source: www.csoonline.com – Author: Making the shift from a security product developer to the same role at an enterprise taught made one CISO more prepared, more...
Customer Identity & Access Management: Die besten CIAM-Tools – Source: www.csoonline.com
Source: www.csoonline.com – Author: Customer Identity and Access Management liefert die Grundlage, um den Zugriff Dritter auf das Unternehmensnetz besser zu managen und zu kontrollieren. Das...
OpenSSH fixes flaws that enable man-in-the-middle, DoS attacks – Source: www.csoonline.com
Source: www.csoonline.com – Author: Researchers from Qualys found two vulnerabilities that can be combined to bypass the server key verification in OpenSSH clients when the VerifyHostKeyDNS...
Ransomware-Banden geben Opfern immer weniger Zeit – Source: www.csoonline.com
Source: www.csoonline.com – Author: Ransomware-Banden agieren viel schneller als früher. Dadurch bleibt Unternehmen weniger Zeit, Ransomware-Attacken zu erkennen. Ransomware-Gruppen haben den Zeitraum bis zur Lösegeldübergabe immer...
Get a Lifetime of 1TB Cloud Storage for Only $60 With FolderFort – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: TechRepublic Academy Published February 18, 2025 We may earn from vendors via affiliate links or sponsorships. This might affect product placement on...
How to Fix the Four Biggest Problems with Failed VPN Connections – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: Erik Eckel Virtual private networks have risen from obscurity to become the frequently preferred method of linking private networks. Although VPNs became...
New Mac Malware Poses as Browser Updates – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: Megan Crouse A new macOS malware called FrigidStealer is spreading through fake browser update alerts, allowing attackers to steal sensitive data, according...
Exploring SWE Affinity Groups: Technical Career Path AG
Each month throughout the year, we spotlight a SWE Affinity Group. We are excited to highlight the Technical Career Path AG. Source Views: 2
Say It Like a Civilian
The SWE Military and Veterans Affinity Group (MAVAG) shares five tips to help you communicate with your peers in a civilian workplace. Source Views: 1
SWE Diverse Podcast Ep 269: Building Legacies, Changing Lives: Donor Perspectives on SWE’s Endowed Scholarship Program
Hear the stories of how endowed scholarships leave a legacy for generations to come on this episode of Diverse: a SWE podcast. Source Views: 0