Source: securityboulevard.com – Author: Marc Handelman Thursday, February 13, 2025 Home » Security Bloggers Network » DEF CON 32 – MFT Malicious Fungible Tokens Authors/Presenters: Mauro...
Day: February 14, 2025
Energy Regulations Are Rising: Stay Ahead with Modern DCIM – Source: securityboulevard.com
Source: securityboulevard.com – Author: Rajan Sodhi As data centers continue to serve as the backbone of the digital economy, they face an escalating challenge: the tightening...
Generative AI-centric technologies: Get Gartner® report – Source: securityboulevard.com
Source: securityboulevard.com – Author: Aaron Linskens Artificial intelligence (AI) continues to revolutionize how businesses operate, with generative AI (GenAI) technologies taking center stage as critical enablers...
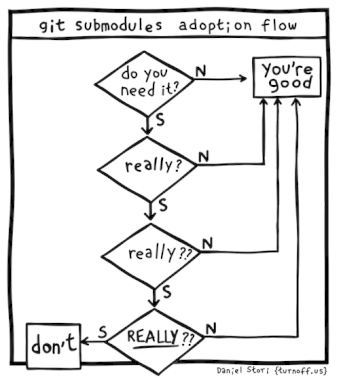
Daniel Stori’s Turnoff.US: ‘git submodules adoption flows’ – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman via the inimitable Daniel Stori at Turnoff.US! Permalink *** This is a Security Bloggers Network syndicated blog from Infosecurity.US authored...
Grip Security Adds SaaS Security Posture Management Offering – Source: securityboulevard.com
Source: securityboulevard.com – Author: Michael Vizard Grip Security today extended its portfolio of tools for securing software-as-a-service (SaaS) applications to provide an ability to proactively identify...
What developers think about application security might surprise you – Source: securityboulevard.com
Source: securityboulevard.com – Author: John P. Mello Jr. Cybersecurity is often viewed from the point of view of practitioners, which is why the DevSecOps company Jit...
Sophos Sheds 6% of Employees After Closing Secureworks Deal – Source: securityboulevard.com
Source: securityboulevard.com – Author: Jeffrey Burt The closing this month of Sophos’ $859 million deal to buy fellow cybersecurity firm Secureworks came with a 6% reduction...
Technical Analysis of Xloader Versions 6 and 7 | Part 2 – Source: securityboulevard.com
Source: securityboulevard.com – Author: Security Research | Blog Feeds This is Part 2 of our two-part technical analysis on Xloader versions 6 and 7. For details...
Nearly a Year Later, Mozilla is Still Promoting OneRep – Source: krebsonsecurity.com
Source: krebsonsecurity.com – Author: BrianKrebs In mid-March 2024, KrebsOnSecurity revealed that the founder of the personal data removal service Onerep also founded dozens of people-search companies....